
Content:
CRO at F-Secure Mikko Hypponen provides a captivating insight into the onset and advancement of computer infections in his talk at Defcon 19 called “The History and the Evolution of Computer Viruses”.

My name is Mikko Hypponen, and we’ll be doing the first session here talking about the history and evolution of computer viruses.
I am from Finland. I’ve been playing around with viruses for the past 20 years, a little bit more than that.
And we are at an interesting point in history, and I’ll get back to that in just a moment, and that’s the main reason why I wanted to speak about the whole evolution of where we’ve been, where we are right now, and where we will be going with malware, trojans, backdoors, worms, viruses.
Now, all those years I’ve been working with the same company – F-Secure. So, we run antivirus labs around the world. And of course in the early days our operations were very small. A couple of guys in the lab analyzed everything by hand, reverse-engineered the code, built detection, tried to figure out how they spread.
Today, all professional antivirus companies run massive labs around the world with automation, because we are, on typical day right now, receiving some range of 100,000 to 200,000 samples coming into our systems. So, obviously we can’t keep up with normal human power any more.
1986 – 1991
But we’ll start from ‘Brain’. So, what you’re seeing on the image here is an original 5.25-inch floppy disk infected by ‘Brain’. Last year, around November, we were cleaning our labs and in one of the cupboards, we found this box which was full of 5.25-inch floppy disks. And that box had basically the first 100 PC viruses in it, including this ‘Brain.A’. And ‘Brain.A’ is considered to be – and is known to be – the first PC virus in history. That’s the first PC virus. We’ve seen before 1986, for example, some Apple II viruses and stuff like that. But this is actually important because we are still finding PC viruses today, right?
So, I did the math, 1986 – 2011, that’s 25. It’s gonna be 25 years. And we had a meeting in the lab. Okay, what should we do about this? It’s gonna be 25 years since the first PC virus. And our media team thought that we should have some sort of social media campaign to raise awareness of computer security. And I thought that that’s boring, what about if I try to go and find the guys who wrote ‘Brain’ 25 years ago. And if I find them, I’ll speak with them, and I ask them, like, you know, why did you do it, what were you thinking, and what do you think about what you started 25 years ago.
And actually, doing that – like trying to find virus authors 25 years later – typically would be impossible. In case of ‘Brain’, it actually isn’t, and I’ll show you.
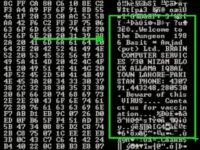
Here is the actual boot code of a floppy infected by ‘Brain’. So, if you just take a closer look, you’ll see some text inside here (see image) saying ‘Welcome to the Dungeon, 1986, Basit and Amjad’, and Basit and Amjad are first names. They are Pakistani first names. Then there is a phone number and a street address.
So, in February, I went to the town of Lahore in Pakistan, which was the address listed inside the ‘Brain’ code. So I knocked on the door. You wanna guess who was at the door? Basit and Amjad. They are still there. Nowadays these guys run an Internet operator, and it is a telco operator for the city of Lahore, and the company is called ‘Brain Telecommunications’.
So, we had a very interesting chat about, okay, why did you do it, and what were you thinking, and… Their explanation was that it was a proof of concept. These guys had a background in Unix1 world. They had been running different mainframe systems in the early 1980s, when they were like in their late teens – early 20s. And then PC DOS2 came around, in 1985. And they hated it. They thought that it wasn’t secure – and obviously, it wasn’t. And they decided to prove it by writing a virus. And that’s what they did. And of course they had no idea that virus would go around the world, infect computers in more than 100 countries around the world, but that’s what it did.
They also started getting phone calls from around the world, from people who had been infected by the virus and all that. They really weren’t expecting that to happen, but of course it went global, became a global problem.
1987 – Stoned
1987 – Cascade
1989 – Yankee Doodle
1989 – Dark Avenger
1990 – Form
What we have to remember is that in 1986 we didn’t have networks. I mean normal computers, PC computers, were not connected to each other in any way. In fact, most computers didn’t have a hard drive. They would typically have two floppy drives only, right. So, if you wanted to move data around you had to put it on a floppy, there were no other means of doing it. And that’s why floppy-based infectors spread so quickly.
Many of these viruses at that time were also, in one way or another, visual. What I mean by that is that you would typically know that you are infected. And one good example of that is the ‘Omega’ virus. This one is not so important or pointed in any history books or anywhere actually, to anyone else except to me. But it’s important to me because it’s the first virus I analyzed. In September 1991, we had a customer case of a large company, actually a telco, where they had damage on their computers and they were suspecting a virus, and they sent us a sample. And I got assigned to look at the sample, because around that time in F-Secure, I was the only guy who would do reverse-engineering in assembly language. Even that I actually had never done on PC, I had background with Commodore 643 and doing assembly there, but, you know, I decided to do that. And I printed out the code, spent a couple of days trying to go through and understand how it works, and learning the interrupts of DOS system and all that.

And I did it, I decoded it. I actually didn’t have a spare PC I could infect at that time, so I actually couldn’t run the code, I was just reading it, trying to figure out what it does. And one of the things that I thought it did, just looking at the code, was that it would be displayed on 13th of the month. If it was a Friday, it would activate and display one character: character number 232, I believe. And I looked up that character and that is the ‘Omega’ sign. So, I named the virus ‘Omega’. That’s the first virus I ever named. And the name stuck, if you google around, you will still find this virus as the ‘Omega’ virus.
And that actually started a tradition. In our days, in our company, once you’ve been 10 years with the company, you’ll get a genuine Swiss OMEGA watch. So, I should have named the virus ‘Ferrari’.
1991 – 1992
Now, many of you remember viruses like ‘Michelangelo’ at that time, that was destructive. So, one way that you would know that you’re infected by a virus is that it would destroy your files, like ‘Michelangelo’ would overwrite the first 100 sectors on your hard drive, destroying FAT1 on DOS systems, and your PC won’t boot.
Let me demonstrate other examples of the viruses which were visual. I have a collection of binaries dated 1992-1994. These are all examples of virus code which at that time I modified slightly to remove all the destructive parts and replication parts. What we are left with is basically the activation code.
So, for example, the ‘V-Sign’ virus which would infect your boot sectors. If you’re running the code right here, it activates by drawing a V sign on your screen (see upper image to the right), that’s why it is called the ‘V-Sign’ because you get a Victory sign. So, what I am running right here is actually a code from 1992, which is the original virus code, but everything else has just been mopped out except the visual part of the virus.
And many of the viruses at that time would do this. They would show themselves to the user. ‘V-Sign’ would do this once a month. Once a month, when you boot up your PC, it would draw this V sign on your screen.
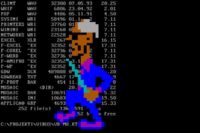
And we have plenty of these examples in here. For example the ‘Walker’ virus (see image in the middle). Guess why it’s called the ‘Walker’… The ‘Tequila’ virus is similar, it draws a fractal, and that’s of course not graphics but DOS-based ASCII graphics with colors.
‘Alex’ – I think it’s some sort of demolition, everything on your screen just burns down, it’s pretty nice actually. You wanna get more examples? We have for instance the ‘Ambulance Car’ virus which is named that way because it displays a little ambulance car moving across the screen and making ‘dee-daa dee-daa dee-daa’ sounds.
Let’s do one more. The ‘Crash’ virus makes a complete mess out of your screen, so you know you’re infected because it looks pretty bad. Oh yeah, this is a good one – the ‘Coffee Shop’, made in the Netherlands (see bottom image in the graphical section above).
So, you would know that you’re infected by a virus because you would get visual displays on your screen, or the virus would play games with you. Like the ‘Joshi’, which does the following: one day of the year, when you boot up the PC, it won’t boot, you get an empty screen. And then you have to type: “Happy Birthday Joshi”, and then it continues. Apparently, that’s the nickname of the virus writer of that time.
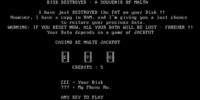
Actually I wanna show one more example, which is a good example of virus playing games with the user. Let’s try with the ‘Casino’ virus, here we go (enlarge the image to see what it does). ‘Casino’ virus is neat, it actually takes a copy of your file allocation table to memory, then it overwrites it on your hard drive. So, you’ve just lost all your files because the file allocation table is gone. But it has a copy in RAM, right. And now it lets you play a game. You have 5 credits and if you win, it’s gonna write the allocation table back to the drive. And if you just reset the machine you lose, because it has already deleted the stuff. And it explains this in detail to the user, and it actually lets you play, and if you win it actually does what it claims. So that’s what I mean by viruses which play games with the user, or at the very least, make themselves known to the user.
1991 – Michelangelo
1991 – MtE
1992 – V-Sign
1992 – VCL
Viruses started getting more and more advanced: things like mutation engine ‘MtE’ made by a Bulgarian virus writer who we knew at that time as ‘Dark Avenger’. It was basically not a virus but a kit that you could use to turn any other virus into polymorphic virus which would encrypt itself with different encryption every single time. Or ‘VCL’ – Virus Creation Laboratory – which actually was the first one that had a user interface you could use to create viruses. That’s VCL: you just choose the menus, you select ‘Generate’, and it makes a virus for you. And this is in 1992, so pretty advanced, 19 years ago.
1992 – 1996
And then comes Windows. First Windows viruses were written for Windows 3.0 in 1992. The very first one was called ‘WinVir’, did nothing special. It was the first one capable of infecting the PE file structure that Windows was using at that time. Other viruses of the time – ‘Monkey’, ‘One_half’ – these are mostly encrypting boot sector viruses.
1992 – WinVir
1993 – Monkey
1994 – One_half
1995 – Concept
1996 – Laroux
‘Laroux’ was a close follower, ‘Laroux’ did not infect ‘Word’ files, it infected ‘Excel’ spreadsheet files. In fact, we later found a variant of ‘Laroux’ which would not just infect your ‘Excel’ spreadsheet but it would also randomly round your random numbers inside your spreadsheets by 0,01% up or down, once a day. So it would slowly corrupt the numbers you are working with. And that’s a pretty nasty attack because you will not notice the problem until it’s been happening for quite a while, which means the data you’re working with is bad, your backups are bad, and there is no easy way to recover.
There is no easy way to figure what it has changed and when. That’s a big deal.
1996 – 2001
The early Windows viruses were often visual as well. I mean they would show themselves. This is the ‘Boza’ virus, written by a virus writing group from Australia calling themselves ‘VLAD’. And that’s the name of the group, that’s the nickname of the guys in the group. So, viruses were still very much being done by hobbyists – for fame, for challenge, just because they could.
Another example is the ‘Marburg’ virus from 1998, which would change your Windows desktop to look like this, so you would know you’re infected (the image fully proves this). This was still the norm in the late 1990s.
More Windows viruses: ‘RemoteExplorer’, ‘Happy99’, and the latter is actually important because ‘Happy99’ is the very first email worm1, we’re talking about late 1998. This was an email worm which claimed to be a greeting card wishing Happy New Year 1999, and would actually show you fireworks on your screen. And while it’s doing that, it would take your address book and email itself as an email which looks like you sent it, to everybody listed in your address book. And the email contents were ‘Happy New Year 1999!!’ and there was an attachment called ‘Happy99.exe’ in it. And of course your friends would believe you sent it because it looks like you sent it, and they would open up the attachment then, they thought that was what it was supposed to do, and it would replicate and replicate and replicate.
And this kind of email worms quickly became the biggest problem we have. The one thing which feels funny now is that you could actually do that: I mean, you could just take a binary, like an executable, and email it to someone else anywhere else in the world, and they would get it, no problem, and they would run it, no problem. Obviously, you can’t do that anymore. I mean, if I try emailing an .exe Windows binary to every single one of you, I don’t think any of you would actually get it. I mean, my operator, your operator or your firewall, whatever, would kill off an executable attachment nowadays, but that wasn’t the case back then.
So more ‘Windows’ viruses at that time: ‘Funlove’, ‘ZippedFiles’, ‘Melissa’. Concerning ‘Melissa’, it became one of the largest outbreaks in history because it combined these two big trends at that time: it combined an email worm with a macro virus infecting ‘Word’ documents. So, it would send itself as an email which looks like it’s coming from you once get infected, sending it to all of your contacts in your address book, and the attachment is not an executable. It’s a DOC file, it’s a ‘Word’ document file. In fact, it’s one of your own ‘Word’ document files which has been infected with a macro virus.
1998 – Marburg
1998 – Happy99
1999 – Melissa
2000 – Loveletter
2001 – Nimda
‘Loveletter’ is still in the history books as one of the largest single email outbreaks. It probably will stay as the largest email outbreak or one of them, because we don’t see email outbreaks anymore. This was one of the problems which just have gone away. Regarding the ‘Loveletter’ virus, I was initially making an estimate that no, it’s not going to be a big problem. Of course I was completely wrong, it became one of the largest outbreaks in history.
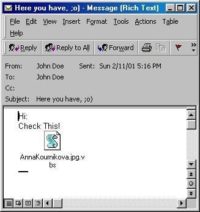
‘AnnaKournikova’ – I just picked this one as an example of the email worms of that time. Many of these would simply try to fool the user into opening up an attachment. And ‘AnnaKournikova’ was an email worm which claimed that it had an image of Anna Kournikova. And here is an example of that email (on the image), and for those of you who don’t remember, Anna Kournikova used to be a tennis player, a pretty tennis player.
So, it is the email they would send. ‘Here you have’ – that’s subject field, and then the content: ‘Hi, check this! Annakournikova.jpg.vbs’. And VBS is visual basic script for Windows system which is an executable, or scripting executable.
And we actually had quite a large outbreak on this virus. And we had people calling our labs, I actually spoke with one guy myself, and he told me that he had received the email, and he heard in the radio news that it was a worm, so he knew it was a worm, and our product actually blocked it, so he was safe. But he still wanted to see the picture. Basically, he asked me how he could disable our antivirus so he could just click on it. And of course it didn’t actually show you any images.
But when you actually click on the VBS file, it would just replicate further, you wouldn’t actually see an image. I believe I told the guy – you know, we already had web at that time – I told him to go online an find some pictures, maybe that’s the easy way out.
Some more viruses of that time were ‘Badtrans’, ‘Sircam’, ‘Nimda’ – maybe this latter one is more important than others. This was one of the first Windows network share replicating viruses and got its name from ‘admiN’, which, well, it’s clear why it’s named that.
There were lots of conspiracy theories at that time because ‘Nimda’ was found in 2001, in September 2001, exactly one week after the terrorist attacks. And there were lots of conspiracy theories that these were somehow related, but it was never actually proven either way. Nowadays, looking back, I don’t think it was related in any way, but everybody was pretty paranoid at that time.
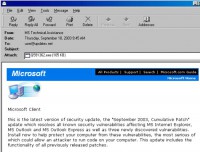
More viruses, and these are all Windows email replicating viruses. Actually, there were several email viruses of this kind that appeared after 2001, those were ‘Klez’, ‘Bugbear’, ‘Mimail’ and ‘Swen’. The latter (‘Swen’) is a good example on the kind of social engineering tricks they were using. Here is an email sent by ‘Swen’, and it looks like it’s an email coming from ‘Microsoft’, so sender is ‘MS Technical Assistance’ (see image). It explains that, you know, there’s new patches. And this is in 2003, so we didn’t have ‘Microsoft’ updates yet, you didn’t have automatic updates. If you wanted to patch your system you had to download the patch file (an executable file) and run it.
So, this used that trick to its benefit. Looks fairly convincing, looks like a real ‘Microsoft’ email and there’s a file, you can see it here at the top, Q<something>.exe attached into it. And that is a name in convention ‘Microsoft’ used at that time for patches.
And it’s especially handy because the message explains to you that this is a security update for September 2003, and it would actually get the current date, so when this virus gets to replicating for a number of years, it would always speak about the current month and the current year. If you would run ‘Swen’ today, it would speak about August 2011, so it felt pretty real, and that’s one of the reasons why it became such a big problem.
And this is also one of the viruses, where the virus author was caught, the Swedish guy was caught and sentenced for some sort of online disruption, based on Swedish laws at that time.
2001 – 2004
…But then things started changing. We entered the years of Internet worms, or web worms, like ‘Code Red’. ‘Code Red’ did not infect Windows workstations. ‘Code Red’ infected Windows servers. It specifically infected Windows web servers, running IIS1. Using a remote exploit, it would infect those servers and immediately continue replicating from that infected server. It would just scan IP ranges trying to find more servers and then, using the remote exploit, infect them. On this image, you can actually see the replication patterns and scope of ‘Code Red’ within the first 24 hours of its existence.
And it started getting copycats of various kinds including: ‘Slapper’, ‘Slammer’, ‘Blaster’ and ‘Sasser’, most of these targeting Windows workstations using remote exploits in LSASS2 or in RPC3 or some other network visible resources of Windows.
2003 – Slammer
2003 – Blaster
2004 – Sasser
So, if you think about that, you got one infected PC, and it starts scanning either random IP addresses or just one by one, like try to go through all IPv4 addresses. We have 4.3 billion IP addresses, which are perfectly scannable, you can scan them all. Most of these worms scanned every single IP address in the world. And of course they’ll find empty addresses, addresses which route nowhere, so there is nothing to infect. Or they find an address which has a computer but it’s a wrong kind of computer, like it’s a Mac, and Windows worm wouldn’t be able to infect it. Or it finds a right kind of computer, like, you know, a Windows computer but it’s blocked, I mean it’s behind a firewall or some sort of routing protection, so you can’t connect, or it’s already patched, so the vulnerability has already been closed by the user.
But as you can guess, if it just keeps on scanning and keeps on scanning, eventually, it will find a computer which is the right kind of a computer, which is not behind a firewall, which has not yet been patched, and in that case of course, it will infect that computer and it will immediately start replicating further from that computer. In fact, they are now both scanning the whole public IP ranges, and it gets faster and faster. And this explains why we got these massive spreading speeds, including ‘Slammer’ – it was later proven that it scanned the whole IPv4 address range in less than 20 minutes from the moment when it was started.
And that’s pretty remarkable: in 20 minutes, all of us who were online in 2003 – it scanned our computers, it scanned our mobile phones if we had mobile phones with the Internet connectivity at that time.
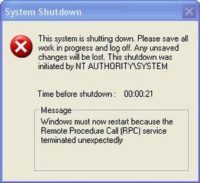
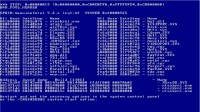
And as the end user, you would typically know that something like this was happening, because you got some sort of a crash on your system. ‘Slammer’, ‘Blaster’ and ’Sasser’ for example would cause a system shutdown because they would remotely crash RPC or LSASS in Windows at that time (see error message screenshot). So, the end user would see that there’s a problem. His PC would shut down. He would have 60 seconds of time to save his data and then it would shut down. He would reboot and he would most likely see it again, in a minute or two, or maybe ten minutes, maybe half an hour, depends on when the next time someone else is scanning his IP address.
So, let’s think about this. You are an end user, you start seeing this regularly on your PC, you can’t work because you PC keeps rebooting. What are you gonna do? Well, you ask around, like – what should I do, my PC reboots? Somebody will know, that, yeah, it’s a virus, all right, what should I do? Well, you should patch the hole, patch the RPC vulnerability or the LSASS vulnerability. Alright, how do I patch it? Well, you go to www.microsoft.com and you find the patch, you download and run it. Okay, let’s do it then. You visit Microsoft download pages and find the actual patch for the RPC vulnerability MS03-039, click ‘Download’ – excellent, you get an executable file. Here we go, and now you are downloading it. And of course this takes a while, which means it’s more than likely that while you are downloading it you actually get the same error message. And now you have two counters on your screen at the same time: you have to count down from 60 seconds to 0 of reboot, and you have the download counter, like how many percentages of the actual patch you’ve downloaded.
So you’re basically running a game or race, like who’s gonna be first. And this game was being run on thousands and thousands of computers around the world. And of course most of the users lost the game, they didn’t get the patch before it rebooted again. Very, very frustrating.
And these are the kinds of problems that led Microsoft to change the way they are looking to security. In 2003, they did the big overhaul code review of Windows base code and started taking security seriously. This resulted first in Service Pack 2 for Windows XP; later into what we have today, in for example 64-bit Windows 7 which actually has a decent security model. So, this was the basic reason why security in Windows world, regarding troubles like these, was finally taken serious.
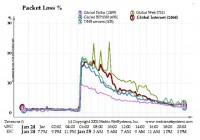
And the problems we saw at the time were serious. The image shows the ‘Packet Loss’ chart of the whole Internet during the hours when the ‘Slammer’ worm started spreading: typical packet loss globally 1% to 2%. Then suddenly jumps to 20%, 30% – massive problem. So, we started getting denial-of-service problems on systems which weren’t infected themselves, but they were in the same networks with infected systems, and the packet generation that they saw was so massive that we started seeing problems with critical infrastructure.
So, in 2003 I wrote down some of the things we saw, ‘thanks’ to ‘Slammer’, and ‘Blaster’, and ‘Sasser’. We had air traffic control problems, we had ATM networks down, we had 911 services down, we had infected nuclear plants in USA in 2003 because of ‘Sasser’ (see particular instances below). We had flight problems, government systems infected, ‘Heathrow’ airport check-in systems infected. ‘Air Canada’ couldn’t operate because they were infected by ‘Sasser’, I believe, and there were Windows blue screens at their check-ins.
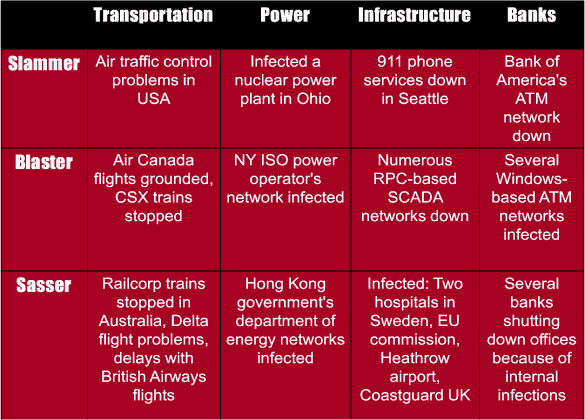
And it wasn’t just computers, I mean normal computers at that time. For example the automation gear started getting affected. In August 2003, ‘CSX’ – those of you who don’t know, ‘CSX’ is one of the largest railroad operators here in USA – announced on their website that they had an in-house infection, which resulted in a slowdown of major applications, including dispatching and signal systems. As a result, passenger and freight train traffic was halted immediately, including the morning commuter train service in the metropolitan Washington D.C. area.
So, trains around the capital of the United States of America stopped in the middle of the day, in the middle of their tracks, because of a computer virus. This actually happened in 2003. And things like these were the wakeup call.
And then of course, we had infections even in things like forest tractors – there was a large case of infected forest tractors, because they run Windows and they got infected because they had GPRS connections. They couldn’t operate these ones as they got infected. And they were, like, typically far away in forests and you had to somehow rescue them from there.
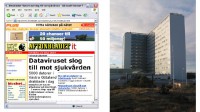
And then we had cases like these: this is a screenshot from a Swedish ‘Aftonbladet’ magazine explaining that the hospital in Vastra Gotaland had in-house infection, with 5000 computers infected, which is bad. But what’s even worse is that also their X-Ray systems which were running Windows were infected. And they actually had patients put into ambulance cars and driven to other hospitals to be taken care of, because they had infections in their hospital systems at that time.
2003 – 2005
But something even more important was about to happen: 2003, a virus called ‘Fizzer’, which I claim nobody here remembers, and I also claim it’s one of the most important viruses in history.
Because ‘Fizzer’ was the first virus we would conclusively prove, that from the very beginning this virus was written for one motive only, and that motive was money.
So, before 2003 everything we saw was written for fun, for challenge, for laughs, for kicks, right? Nobody tried to make money with viruses until ‘Fizzer’. And the way ‘Fizzer’ tried to make money is by sending spam. So, it would infect computers, build a proxy network out of them, so you could reroute proxy or email traffic through them, and that service was then sold to spammers.
And this is something we still see today: spam, email spam still exists, and it’s still being sent through infected home computers, and obviously there’s money to be made out of this.
Very quickly, many of the hobbyists virus writers of that time realized that they could actually use their skills to make money by cooperating with spammers, by starting to steal passwords with keyloggers1, starting to steal credit card details when people were doing online purchases from infected computers and typing in their usernames and passwords.
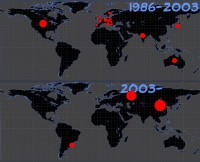
And very quickly we also started seeing the shift, geographical shift on where viruses were coming from. In the good old days, before viruses turned into money making machines, they were mostly done in developed western nations, like Europe, USA, Canada, Japan, Australia. (Upper image to the right).
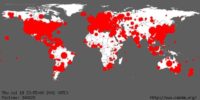
Today the biggest hotspots are Russia, Ukraine, Kazakhstan, Romania, Moldova, China obviously, and South America, especially Brazil, which is the biggest source of banking trojans which steal money during online banking (See bottom world map image).
And the virus writers themselves changed. We had completely new kinds of online criminals getting onto the Internet and doing this. Here’s examples of caught virus writers of 1990s, including in the top middle Mr. Chen Ing Hau, who wrote the ‘CIH’, aka the ‘Chernobyl’ virus.
In the lower section of the image, there are some caught virus writers after 2003. Do you see any difference? So, they became much more organized, much more professional. The guy at the bottom middle Mr. Tariq Al-Daour was actually using keyloggers to steal credit card numbers and they were then laundering money from those credit card numbers by putting them into online poker games, and losing money on purpose from the credit card numbers to accounts that they controled, and then they would move it back to the real world. What they did is they laundered close to 2 million Euros. And that money was then used to purchase gear – gear like hiking boots, tents, sleeping bags, knives, GPS navigators, plane tickets. And all this was shipped to Iraq, to the insurgents fighting over there. So what we have here, for example, is a link between online crime – viruses, trojans, backdoors – and funding the insurgents in Iraq.
2003 – Sobig
2003 – Witty
2003 – SDBot
2004 – Mydoom
2004 – Netsky
2005 – Mytob
And then, open source bots, like ‘SDBot’ whose source code is actually licensed under GNU2 public license, and we’ve seen tens of thousands of variants of this throughout the years, we probably still see versions of ‘SDBot’ being made today, like 8 years later.
Another typical problem at that time was botnets creating bots. So you have a number of infected machines, and they could all be controlled centrally, creating a botnet which could be used not just to send spam but also do banking trojan attacks and credit card theft, and stuff like that.
And then we got ‘Sony’. Now, ‘Sony’ gets a lot of fame. And they get it for a good reason. They’ve been doing bad stuff for a number of years. I think it pretty much really started with the rootkit that they were shipping on ‘Van Zant’, ‘Switchfoot’ and ‘Celine Dion’ music CDs.
So if you would buy a ‘Celine Dion’ music CD and listen to it on your CD player – no problem. But if you put it inside your computer, it would autorun an installer which would install a DRM3 code on your system. No questions asked, no prompting, nothing – it just installs a DRM system. And then it installs a rootkit, a Windows rootkit which hides the DRM. And in fact, it doesn’t just hide the DRM. It hides any file or any folder which starts with specific characters. Basically, a ‘$_$’, I believe, or something like that.
Which means, yes, could hide the DRM, but you could also hide anything else, and viruses very quickly started naming their binaries with ‘$_$’, because if a computer which had been used to listen to ‘Celine Dion’ got infected, ‘Sony’ would now hide the virus. And it would hide it so well that pretty much none of the antivirus program at that time could scan the files anymore – they’re just gone. And of course some would claim that if you listen to ‘Celine Dion’ you deserve to get infected, but I’m not saying that.
But there were interesting comments coming out of ‘Sony’ at that time. Especially, the person named Thomas Hesse, President for ‘Sony BMG’ International. He made a quote which was so cool that we actually printed T-shirts out of it: ‘Most people don’t even know what a rootkit is, so why should they care about it?’
And that’s a great quote, I mean, it says ‘you don’t know what it is’. I mean, most people don’t even know what a brain damage is, so why should they care about it?
2005 – 2008
Then we started seeing more and more rootkits. Not just from ‘Sony’ but from traditional virus writing gangs who wanted to hide their malicious code better. ‘Haxdoor’ basically was a kit which you could use to hide any other binary or processes, or registry keys, or open ports.
2006 – Warezov
2007 – Storm Worm
2008 – Mebroot
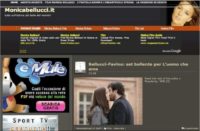
And then we had ‘Mebroot’. ‘Mebroot’ which probably for a number of years stayed as the most advanced malware we’ve ever seen. Now we have two contenders for the same title. But ‘Mebroot’, when we first found it, was all related to this. Do you know Monica Bellucci? She plays the part of Persephone in the ‘Matrix’ movie. This is the website of Monica Bellucci, MonicaBellucci.it (see the website screenshot), in Italy, she is Italian. And this was one of the first, if not the very first website that we saw, that was used to spread ‘Mebroot’. So, we entered the days of drive-by downloads. You would get infected by just browsing the web.
And now today this is number 1 way of getting infected. Email and email worms haven’t been the main problem for a number of years. It’s the web, you browse the web, and there’s an injected JavaScript line there which goes through all your plugins in your browser, including ‘Java’ and ‘QuickTime’ and ‘Flash’ and what have you, tries to find an old version, if you have an old version, it will pup it – and you’re infected, that’s exactly what this page did.
It was one of the first cases where we saw it happening. And what ‘Mebroot’ actually did is that it installed itself to the master boot record of the infected computer, which is pretty much exactly what ‘Brain’ did. Except when ‘Brain’ was in the wild we didn’t have hard drives, so it went to the boot sector of the floppy. This actually goes to the boot sector of your hard drive, the first master boot record.
And that’s pretty hard to do under Windows, but they did it. And even more remarkably – I think it’s a good example of how advanced these viruses started to become – it’s that obviously when you’re running below Windows (it boots before ‘Windows’ boots), you run the risk of crashing Windows, but it almost never did. It was very well tested. And if it did, I mean, if something went wrong, then you actually ended up with a Windows blue screen. Now, obviously Windows has crashed, Windows is no longer running, but ‘Mebroot’ was still running. And in this case, ‘Mebroot’ would make a diagnostic dump of the crashed computer and send it back to the virus writers over the Internet, so they could debug and figure out why it crashed: remote quality assurance for malware, right?
2009 – 2011
‘Conficker’ – the biggest outbreak of 2009 – still remains one of the biggest mysteries we have in the history of viruses. Massive, massive infection which wasn’t used to do anything at all.
And then we started finding even more advanced viruses. If ‘Mebroot’ was advanced, this is pretty much the state of the art nowadays: ‘TDSS’, aka ‘Alureon’ rootkits which are today capable of infecting a 64-bit Windows 7 in the MBR1, booting all the way from the MBR, surviving the Windows boot, regardless of all the security features that were introduced in Windows 7, pretty remarkable stuff.
The amount of infected machines around the world right now, with this, is in the millions. And it’s being used for different kinds of a moneymaking scams. It’s one of the biggest problems we have at the moment.
But that was still quite different from these ransom trojans that we started seeing as well. By this time, like I explained earlier, most of the infections were invisible: you wouldn’t know that you’re infected. But then we started seeing Trojans like ‘GPCode’ which were very visible.
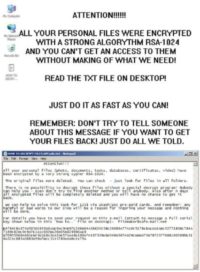
What ‘GPCode’ does is it infects your system, then it waits for the PC to be idle, so that you are not at the computer, and then it starts encrypting your hard drive: goes through your hard drive, encrypts everything. And then it changes the Windows wallpaper to the message shown on the image, where it explains that, you know, all your files have now been encrypted, if you want to get your files back, please read the ‘how to decrypt’ txt-file. And when you read the ‘how to decrypt’ txt-file, it explains to you in detail that “Yup, we just encrypted your files using RSA 1024 with an ASCII, and if want to get your files back, please email us at ‘filemaker@safe-mail.net’ and send us 125 bucks through a Ukash pre-paid system, and provide this unique key, which is unique to your system, and they will provide you with the decrypter.
Well, they actually will. We’ve worked with multiple cases where affected users have sent them money and have gotten the decrypter back.
And as much as I hate the idea of anybody sending any money to these clowns, I know that people have done it and they have gotten their files back.
2009 – Conficker
2010 – Stuxnet
2011 – Ransom Trojans
Many of these cases have actually been corporate users, where not just the corporate laptops have been encrypted but also network shares have been encrypted. And then they learned that they actually don’t have good backups. And that’s a big problem, so they would be more than happy to pay 125 dollars to get their files back.
But all this work with malware like this did not prepare us for what we would find next. And that was ‘Stuxnet’ – ‘Stuxnet’ which was found in summer of 2010, ‘Stuxnet’ which had been around spreading in the wild already for a year.
And that’s actually remarkable. And that’s actually embarrassing to us, I mean, us antivirus vendors and security companies. We missed ‘Stuxnet’ for a freaking year. Nobody saw it going around. Eventually, when it was found, it already had done what it wanted to do. And of course, as we know by now, ‘Stuxnet’ was written by you guys, I mean, the Americans, the U.S. Government.
And it was a successful operation that attempted to disrupt the Natanz nuclear enrichment plant in Iran. And it did. In fact, we believe it already did what it wanted to do in 2009, so by the time we found it in 2010, it didn’t actually matter anymore, it had already done what was meant for.
So, let’s look at that a little closer. We obviously have computers everywhere: in factories, in plants…You go to any chemical plant, any power plant, any food producing plant, and you look around – it’s all being run by these. That’s a ‘Siemens S7-400’ (see image), a typical PLC2 programmable logic controller. For example, the elevators in this building most likely run PLCs or maybe something along these lines – automation which isn’t running Windows. ‘Siemens’ gear is running 32-bit Linux inside, very fault-tolerant systems. And the way they are being programmed is typically for Windows workstations. And that’s the route in, the ‘Stuxnet’ will infect pretty much any Windows computer in the world.
But it won’t do anything except replicating, unless the computer has the ‘Siemens Step 7’ programming environment installed. And that’s the environment you use to program these. And even if it finds ‘Step 7’ running on a computer, it won’t do anything unless it’s connected to the right kind of a PLC, it has to be ‘Siemens S7-417’ or another model. If it finds the right PLC, then it will reprogram the PLC. And now it waits for somebody to disconnect the PLC from the computer and take it to a factory floor. And it still won’t do anything, unless it’s connected exactly to the right kind of gear, and it’s looking specifically for the things you can see on the image; these are high frequency power converters manufactured by a company called ‘VaCom’. It’s looking for a specific number of the right kind of high frequency power converters. And of course, these, we believe, were the converters that were used to spin the centrifuges in the Natanz nuclear enrichment plant. So, the real target becomes not just the high frequency power converters, but the whole nuclear program, or the nuclear enrichment program.
So, it has been a pretty wild ride. We look at the last 25 years – from ‘Brain’ spreading on 5.25 inch floppy disks, to ‘Stuxnet’ which is more than a megabyte of code, multimillion-dollar project, more then 10 man-years in making, targeting completely undocumented tailor-made systems, infecting PLCs, which has never been done before.
It’s been an amazing change that we’ve seen. Many things have changed, and at the same time, many things haven’t changed. For example, ‘Brain’ never spread over the Internet because we didn’t really have Internet in 1986 as we have it today. ‘Stuxnet’ does not spread over the Internet, it spreads on USB sticks. Why? Because the systems it wants to reach are not on the Internet, obviously nuclear systems are not online, they are separated, that’s why it spreads on USB sticks.
‘Brain’ was actually a rootkit, if you tried to read the infected boot sector, you wouldn’t see it, it would give you the original boot sector instead. ‘Stuxnet’ has a rootkit to hide itself not just on the infected Windows computer, but also on the infected PLC.
So, everything has changed, and nothing has changed. And it will be interesting to see what kind of viruses we will be analyzing 25 years from now. Thank you very much!











































Before 1987, I read an article about the “Israeli” or PLO” virus. It infected .EXE files, not the boot sector, and I believe it was triggered to delete files on April 1. I obtained a copy of the virus and examined the executable code, and used it as a demonstration in a series of speeches about viruses beginning in 1986. It was the first virus I learned about. Why isn’t that listed as the first, or one of the first, viruses?
Dave,
Thanks for letting our site visitors and us know about that pioneering virus sample! Great to know.
With regard to why it’s not listed – the article is based on Mykko Hypponen’s presentation and perspective.
Anyway, thank you again for the useful information!