
 Penetration tester Andy Cooper, when participating in DerbyCon event, shares his perspective of methods for evading the regular antivirus defenses.
Penetration tester Andy Cooper, when participating in DerbyCon event, shares his perspective of methods for evading the regular antivirus defenses.
So, I was at DerbyCon and I couldn’t get my AV working. Fortunately, Adrian Crenshaw was able to jump in and actually assist me and fix this problem. Anyways, my name is Integgroll and I will talk about stopping your fighting antivirus. It’s something that I am kind of passionate about for some strange reason.

I was a systems administrator with a development background. I hate the word or term DevOps – I don’t know why, it just seems odd to me and it doesn’t describe as well I think. So I prefer Administration and Development – it works better. Currently I’m a penetration tester.
I wrote Wharf Whacker, which none of you know what that is. If anyone knows what that is, please raise your hand. Ok, that’s, like, three people. That’s exciting, because Wharf Whacker is the world’s only – if somebody else has written one, I’d love to hear about it – two-factor authentication port knocking suite that is written in Python as a library. You can take it and roll it into anything that you want and actually have a two-factor authentication port knocking for anything, that is written in Python.
I learned not too long after DerbyCon last year that I actually have a single user who’s not me. Somebody emailed me and had me assist them getting this running. I don’t know what they’re doing with it; I don’t really want to know, because if you’re using stuff at that point… I’m also an avid curler. By that I mean that I sport with brooms and big stones, the rocks and all of that fun stuff. I love it; it’s an exciting fun time.
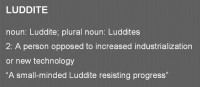
I’m also a Luddite. And here is the definition of Luddite that I like to use: it’s “a person opposed to increased industrialization or new technology”. And this quote is actually pretty accurate on this for my opinion on what I am: a small-minded Luddite resisting progress. It’s not like I hate all technology or anything like that – obviously I hate setting up AV stuff.
However, what I mean by that is things like home automation – that scares the shit out of me. I don’t know about you guys, but I don’t want that. Any sort of biometrics – that’s another thing I’m not a fan of. I don’t want that in this world; it’s a terrible idea. But I adhere to new technologies like that, and it makes me kind of cringe a lot. But what it really makes me want to do is take these new technologies and put them into a box, and then put them into another box, mail that box to myself, and then smash it with a hammer.

Now to get a little bit into the actual antivirus evasion part of this talk, I’m going to go back a little bit to Fred Cohen here. Fred Cohen did some pretty interesting research about antivirus. In 1984 he wrote a paper about viruses and how they actually affect the world, and different things along those lines. Then three years later he actually goes out and writes another paper and demonstrates that there’s really no way that antivirus can detect and avoid anything and everything that we can write.
Three years after he really starts looking into it, and he realizes that it is a no-win game. It’s not something that you can actually succeed at. And then in 1989, three years later, he writes another paper about it and actually starts writing antivirus programs.
Even though he saw the defeat in it, he realized that it is something that we kind of need as an industry and as everybody, and so it’s something that we need to go with.
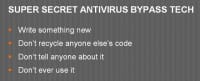
Now I’m going to tell you the only actual antivirus evasion part of this talk. I’m going to give you the exact secrets to avoiding antivirus.
• Write something new.
• Don’t recycle anyone else’s code.
• Don’t tell anyone about it.
• Don’t ever use it.
Then you can start bypassing AV for the rest of time, as long as someone else does not write your code that you wrote, which is why you don’t want to share it or recycle it or anything like that, because usually what AV is picking up nowadays is actual stubs from malware that’s sitting around, other things of that sort.
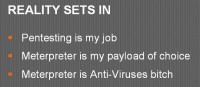
But in realizing all this kind of stuff that is going on, I can’t really just sit down and cancel this stuff out, because, like I said, pentesting is my job. Obviously, Meterpreter is my payload of choice; it’s what I actually like to go with. But the biggest problem on that is that Meterpreter is kind of antivirus’ bitch, in that almost any way that you have of automated through Metasploit without Pro (because I’m cheap), it’s going to get caught by AV.
So, if I just go and PsExec across a network, AV is going to pick it up every single time, because it’s so used to it. So I have to set a custom .exe or do anything else, run it through a different program and do goofy things like that. That’s not always the way I like to do it. I would just like to be able to send a payload and have it work, especially while I am on a pentest.
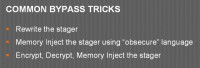
Some of the common bypass tricks on that if you actually want to make that happen is to rewrite the stager on it so that it actually accepts a different way or does it a little bit differently. And then you have all that stuff nowadays that is doing memory injection using some language, that’s, you know, not what they’re expecting. Or somebody’s encrypting and decrypting it on the other side and injecting it through memory that way. Memory injection is really hot right now, for good reason – it works really well and it tends to bypass a lot of antiviruses. However, it’s not always getting caught right now, but I think part of the reason for that is that the AV industry and different companies as a whole are kind of waiting until they have that problem as a whole solved, because they see that as this one thing that once they’ve solved that problem, all of that goes away, and so they’re not hitting on things individually as it gets incremented upon, at least not as much as I’m noticing.
So, why am I here? I’m going to tell you a little story about a pentest I was on a little while back. What ended up happening with this pentest is I was working in a company through the organization, and I noticed that they had an ESX server that was open. So I went ahead and downloaded vSphere and did all that stuff so I could actually interact with it. I typed in a default password, it worked. I saw that they had a bunch of VMs running; I saw that they had a VM template that they were using, so I downloaded the VM template, set it up locally, booted BackTrack on top of it, took the hash out of it, and then just started passing the hash to the admin hash that they had left on the box, because they didn’t change it, to all those different boxes.
So, while the authentication was properly working, it actually had Symantec Endpoint Protection set up that was really well set up. While I sat there and tried a bunch of different AV bypass methods that I had, it took me a little bit to realize what it was picking up on, and it wasn’t necessarily some of the antivirus. It was actually the point where my memory was going from just being writable or readable or rewritable to where it would be executable. And whenever it did that, it would just delete the payload that I had loaded. So, that would go away and I would no longer have that there.
Conveniently, to do any sort of memory injection, especially with things like Metasploit, to get Meterpreter on there, you kind of need to have executable memory to make it really easy. So it’s not something that could just magically have it happen. I did eventually find a solution for this, but I will talk about it later on, because everything else that I did, I beat my head against the wall for hours long, and it made me very embarrassed, because I got the chance to steal the entire operating systems from them, but I didn’t get the chance to actually get in there and really do what felt like the last couple of minutes.

What that really means for us is that antivirus is getting a little bit better over time. It’s not going to happen today or tomorrow. I really think that Meterpreter’s days are numbered. There’s going to come a time where the antivirus industry is going to have it essentially nailed down, because Meterpreter, as awesome as it is, doesn’t change a whole lot. Most of the new stuff that comes into Meterpreter gets thrown as additional modules that you load after the fact, and not the actual delivery system. And so, that’s one of the things that we’re going to have to work around. We don’t really have an option of doing it forever, so we’ve got to do something about it.

Now, what do we do here? You’ll notice that this (see right-hand image) is a picture of the Alan Parsons Project, and I have this here because they have a song Time, and I think the time flows like a river, much like they do. So I like to look back whenever I’m thinking about things like that as: “How can I solve today’s problems with yesterday’s solutions?”

And the thing that I find about it is, if we look back to the Labor Movement we can actually find a really good solution for this, as I think. For example, back then they were dealing with problems of having really long hours, shitty pay, they didn’t have any job security, and the work they were doing was pretty damn hazardous. And it wasn’t a good work environment for anyone. These people were getting screwed over, while the people who were up there were making big money and didn’t really care about it.
So people ended up banding together on this, and I can imagine the first conversation that actually happened with this, where a guy walks into the office and he is looking at his boss, he’s got his hat in his hand, if he can afford a hat, so that’s an imaginary hat; and he’s talking to his boss. He’s like: “Hey, listen, we’ve got to do something about this, I’m not making enough money to actually survive here, and that’s not a good thing, because I’m never home to see my family. Why do I have any of this? Why am I working this job?” And his boss kind of looks at him and says: “Yeah, you’re fired.”
So, that doesn’t really help him at all. He’s got this organization that wants nothing to do with him, much like I think the antivirus industry is with our industry; and I’ll explain that in a little bit. And so, what ended up happening is everyone had to get together on this, so they had to get as many people as they could into collective bargaining groups, basically, unions, to actually go to their bosses all at once and say: “Listen, you’ve got, effectively, two choices, and they are either a) we stop the work here, or b) you guys actually listen to what we’re saying and help to adjust some of these things.”
And it didn’t happen all overnight. If you look back, there were a bunch of different laws that happened. For example, some of them that some of the fat cats had made collective bargaining illegal for a while. Unions weren’t legal. And then all of a sudden they were back, and then things started to trickle after that, slowly. So they got it reduced down from like a 16-hour day to a 12- and then gradually to 10-hour day, and then they got the minimum wage thrown in. And then they got the 10-hour day thrown back to an 8-hour day, which is where we are now – well, not in this industry, but that’s because those extra hours we do on top usually – we just love it.

And so, while this whole time it’s not all sunshine and rainbows, they still got some things to do and move in a direction that really helped them out, and also helped everyone out at that point, because the whole economy of the world actually went up like that – when Britain did it, when we did it, everything went out better.
However, there is this other group of people (see right-hand image), the other definition of Luddite – in fact, the number 1 definition whenever you google for it – and that would be “A member of bands of English workers who destroyed machinery, especially in cotton and woolen mills, that they believed was threatening their jobs”. And the Luddites, basically, along with a couple of other riot incidents, hindered the labor movement. They made a lot of people look like they weren’t organized. They made a lot of people that actually were there and caring about what was going on and trying to make a difference, look like idiots who nobody cared about.
Because when you come in and you have this group of people that looks like they’ve got their ducks in a row, but you have three people somewhere else who are burning shit down. If they’re burning things down, this other group, if they’re associated with them at all, they all look bad, and everyone actually is the problem then, and no one is going to deal with them. And so, this Luddite kind of act of smashing looms was a problem. It really, like I said, hindered the Labor Movement.
And while I was talking to a previous coworker about this, and this is my exact point here, he gave me this quote: “The only way to make antivirus vendors know their product is a joke is to embarrass them.”
Now, I’m not putting his name up there on purpose, because I think this is actually a really core quote to attribute to someone, because I think it’s really short-sided. It sounds very much of the Luddite way in that the only way we’re going to make this work is to shut them down as much and as often as possible and make none of this work for them. And by doing that then they will listen to us, which is not the case, that’s not how it’s going to work. It’s not how it’s worked, obviously, because if that was the case, the first time anybody had an antivirus bypassed, they would have already listened to us. They would have already been: “Oh, we need to work on that”, rather than just updating signatures and dealing with it.
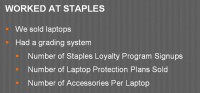
Another part of this big problem here is – I’ll explain it in a second. I worked at Staples for a while, and Staples sells laptops. Staples has this grading system (see right-hand image), where they go based on the number of loyalty programs that you sell and the number of protection plans that you sell for laptops, as well as the number of accessories that you sell with laptops. And by accessories, that includes the protection plan, so that’s really cool if you can get that, that’s a bonus accessory. It also includes things like mice, it includes things like Microsoft Office, the backup discs that come with it, and, conveniently enough, antivirus.
Now, when you’re in a store at Staples, the biggest metric for wanting to sell these things and making sure that every single person walks away with it is the amount of time your boss will spend yelling at you, and otherwise if you do not. So, to reduce that time it usually ends up that you’re increasing the amount of time that you’re wasting on your customers to actually get these products into their hands. So you have a bunch of people that are working at places like Staples and Best Buy and all these other organizations that are purposely handing antivirus out to people.

And so, antivirus companies are still making sales, and much like this guy (see left-hand image), the embarrassment that you’re causing them does not matter. They don’t care – they’re still in the race, they’re still making money, and they’re still going to keep running, because they don’t have to change.

So, obviously, where I’m really going with this, what I’m actually talking about at this point is kind of what’s going on. This right here is a list of the features that come with Symantec Endpoint Protection right now. I’m hitting on them right now because that’s the one that I had the biggest problem with, really.
But if you notice at the bottom, I mean, they’ve got stuff for Mac and Linux – that’s kind of cool. They have stuff for virtualization features. But the thing at the very bottom is the thing that interests me. They have a centralized and granular policy management system.
What that means is that they have a server sitting there somewhere, or some sort of service, that is controlling all of the stuff in the background. It actually sits there and reports on things. It actually talks to the stuff, it updates the virus signatures, all that kind of stuff. And it’s really helpful for your client and for your customer, and really for security as a whole – I won’t say otherwise, because antivirus is not a bad thing. It’s annoying for me, but it’s not a bad thing overall. It could be better, but that’s something we need to work on.

What’s going on here is I have a solution program for this (see right-hand image). One of them is we need to work with antivirus vendors to set up a system of bypass bounty, basically. As you find a way to get Meterpreter running on a system in whatever antivirus, at that point you should be able to go to that antivirus vendor, say: “This is the method that I’m using, this is how I’m bypassing it”, and whenever they realize that it works and whatnot, they throw money in your direction.
Now, this works great, as long as they continue to keep this faith and we do the same thing, so we don’t have problems like Facebook not paying their researchers because they’ve misfollowed something and somebody didn’t listen to them. And so we actually had to go as a community and pay this person.
Another thing that we have to do in this is set up a system where penetration testing isn’t actually stopped. Because if we do end up sending constant antivirus bypasses to AV vendors, what’s going to end up happening is they’re going to apply them and apply them, and then we won’t be able to do penetration testing; or we won’t be able to do it as effectively as we should be able to do it.
And the third thing is that we need to continue to do our bypass research through the bounty processes, so we need to actually go and continue to do this stuff, continue to research it and work with them to make their product better, and in turn to end up making security better.
The second step looks a little funny; it’s kind of like the Underwear Gnomes here. But I have a few ideas for how to make that second step work. And one of them is kind of like centralized alert and approve. What ends up happening is during a penetration test they’ve got someone who sits there and waits for the alerts and clicks OK whenever they actually happen. It’s not ideal, and if they actually said: “That’s the system that they’re allowed to do things on with Meterpreter or whatever”, it’s not the ideal solution, but it is a solution that could work.
Another thing that we could do is actually do straight-out application white-listing. So I hand them my payload and they plug it into their centralized server and anytime it sees that payload, it says: “Ok, we’re not going to execute anything on it; we’re going to let it go.” Also not ideal; a lot of the reason for that is that I don’t want them to have that payload, because it may still be that they have other things in place that they’re going to hate on. And it also informs probably more people in the organization that I’m doing a penetration test for, than they really need to know what’s going on – another slight problem.

I have a third idea that I’ve come up with, which is cert signing. Whenever it comes down to certs, we know that SSL certs for websites are iffy at best as to how they work, but it’s not the cert’s fault on that. Certs are great for what they’re doing. The real problem at that point is actually the chain of trust that goes with the certs; it’s been well established.

Code signing certs kind of have the same problem. But in this kind of situation, code signing certs are appropriate for what I’m talking about doing, because it’s something I can assign to any payload that I have, so it doesn’t just have to be Meterpreter, it doesn’t have to be this other piece of code that I’m trying to run – it can be any of these different executables that I’m talking about. I’m only talking about touching disc, I’m not actually talking about buffer overflows or anything like that because that’s not something that will work without slowing things down too much.
But for this I’m talking about, essentially, PsExec. So I’m setting the payload over there, it’s written in disc, AV checks it, deletes it, basically, most of the time. But with this, what it ends up letting you do is sign your code, send it over through PsExec. At this point it can actually check the certificate that’s actually loaded up on there. So antivirus checks out the cert, checks out the dates that are on this cert. If it’s correct and it’s inside the system, then it goes ahead and lets the code run, as long as the dates are also accurate. And then, when the dates are wrong, or afterwards, AV will go through and check and delete that anyways, so your files go away when your penetration test is done. And it also, like I said, lets you do multiple types of payloads.
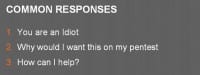
Now, as I’ve been telling a bunch of different people about this, they thought I was idiotic, which is basically common response number 1: “You’re an idiot”, to which – yeah, pretty much. Another one that I get is, this is very common: “You’re a penetration tester, your job is to break into my systems and then tell me about it later.” And I really wish that it was my job to walk in, break your systems, drop the mic and walk out, because that would be awesome. It really would be a great day.
But really, what my job is – is to come in, check out your organization, yes, find your exploits that may be there, find your vulnerabilities that are on your systems, get in there and find and demonstrate an impact just of what’s actually going on, to how I can make this look good for your organization, to where fixing these security problems is a good solution for you; and, at the same time not waste my time, or your time, really, trying to find more impact and more vulnerabilities on your systems by trying to bypass antivirus, which is something that, effectively, we know is bypassable. I mean, as it’s already stated, somebody is going to find a way to get around it, because I can always write something new, Meterpreter just happens to be the best tool to use, because I only have a week to do it in. But if I want to write custom software to come and screw your agency over, I can do it, it’s not the end of the world for me.
That’s basically what all that is. And this cert solution came to my mind because what I ended up finding was the only way to bypass it at that point was to actually sign the code that I was sending over there with just any signature, because that was really what was going on. It was checking the executable and saying: “Well, I’ve never seen this executable before, so I don’t think I want to let it have executable memory; that’s not a good thing, apparently.” So it didn’t allow that; clipped it the second that it happened.
There were two ways that I got around it. One was signing the code, and the other one was actually kind of goofy. I set the memory as “rewrite”, wrote to the memory, told the memory to go away and then set it back as “read-execute” in the same spot, and that actually caused it to work as well, which it shouldn’t have.
The third response is the one that I actually never get, and that is: “How can I help?” One of the things I’d like to do is I’d like to talk to as many antivirus vendors about this kind of stuff that I can and get one, if not all of those different things set up to help make their product better. It’s not the worst thing that we can have. We could just have no AV solution at all, and then everyone would be screwed. But as we continue to help and actually work with organizations to make things better for them, their product gets better, our customers get better, everyone’s threshold goes up, and that’s a good thing, I think.
Stop using VirusTotal is another great idea, because you are effectively doing a bug bounty program with VirusTotal, but you are not getting paid for your work at that point. So you’re straight out just giving them free payloads that they can go and check and know what’s going on, especially with the number of them that get thrown that just have Meterpreter in them. So, go in, I go into a new pentest, my freaking bypass is not working anymore, or I have to waste another 6 hours of my customer’s time, or my free time, which I’m probably going to spend on it anyways, but that’s not the point, to actually get this stuff working.
The other thing that is really important here is if you look at the way you’re dealing with organizations like that, where there are two huge departments that have the biggest amount of push whenever it comes to antivirus or anything like that; and they are marketing and sales. They get the most anything from all of those organizations. And so, if you really want something to go through, for what I’ve noticed, to change, you actually need to go and bug the sales guys and say: “Hey, this is something I heard being talked about. Do you guys have anything like that in your pipeline? Are you actually doing something like that?” 90% of the time you’re going to get someone saying: “Yeah, that’s in the next version, of course, so just buy this one now, and then we’ll roll that over in the next one, whenever it happens.”
That is something that is iffy, but still that 10% that you can get through, as more and more people do it, the more they will start to actually pay attention to it. So, if anybody does have any antivirus contacts, I would love to have them shared and to hear as much about it as possible, because I’d love to talk to these people. I haven’t been successful anyways – it’s just: “Hey, I need a meeting” – it doesn’t really work like that. You can contact me at Twitter @integgroll, you can also get me at integgroll@gmail.com.






























