Director of Technology Strategy at Sophos James Lyne expresses his vision of the way malware production has evolved over time, shifting from mostly prankish activities to the complex sophisticated cybercrime infrastructure that we’re seeing today.
 Hello there, my name is James Lyne from Sophos, and today I am gonna be talking about how malware authors are winning the war. My job at Sophos is to focus on long-term technology trends: the next five years of things that are happening in IT, like mobilization, virtualization, de-perimeterization1, PSaaS2(-‘ization’) – you can basically apply it to anything. But I am also a bit of a geek. I love playing with malware and looking at the bad guys’ creations in the labs, and figuring out exactly what they are up to.
Hello there, my name is James Lyne from Sophos, and today I am gonna be talking about how malware authors are winning the war. My job at Sophos is to focus on long-term technology trends: the next five years of things that are happening in IT, like mobilization, virtualization, de-perimeterization1, PSaaS2(-‘ization’) – you can basically apply it to anything. But I am also a bit of a geek. I love playing with malware and looking at the bad guys’ creations in the labs, and figuring out exactly what they are up to.
I’ve been at Sophos for more than seven years, and over that time I’ve seen a huge change in the nature of malicious code that we are having to deal with for our customers. We are now in what I like to call the third wave of malware.
That was the time when one of our PR people Graham Cluley, well known gentleman, annoyed virus writers so much that they put his face in the middle of the screen, you had to throw coconuts at him to be able to use your computer again. The first wave of malicious code was basically lots of fun.
The third wave of malicious code is far more serious. The third wave of malicious code is about organized criminals producing malware. And I believe that this change has not yet been appropriately recognized by the industry. People aren’t taking action to protect themselves against this escalated threat.
So, what’s changed in the third wave of malicious code? Firstly, a massive increase in the volume, the quantity of malicious code. At Sophos Labs, we now see 95,000 unique individual pieces of malicious code every single day. It’s an astronomical quantity of malware. Only a few years ago, we were dealing with on average 5000 pieces of malware.
And indeed, if you look back over the history of all time you can see that the dinosaurs didn’t particularly have a problem with malicious code. So, what is it that we are doing wrong? It is a serious issue.
What’s happened is the bad guys have brought professionalism to their trade. They’ve developed a black market economy. They are adopting the latest and greatest technology. And they are garnering more resource than most vendors and most public sector organizations, and governments can put towards this issue. That’s principally because they are not bound by law, they are able to steal these resources. It is easy for them to go out to the Internet, click their fingers and get 80,000 computers.
So the bad guys with their illicit economy have changed the game. As any economist will tell you, when you get a market, when you get people providing services, franchising, products – you get research, innovation, development and competition. And that is what is behind the significant escalation in the quantity and the quality of malicious code out there today.
It’s actually quite astonishing when you go and look at what these guys are now producing. Just to poke fun at SaaS, the ‘SaaSificationization’ of crime, crimeware as a service – all these ridiculous buzzwords, but underneath it there is a real trend.
There are lots of AV check sites on the Internet, all set up by the bad guys to provide services for people producing suspicious files. The idea is simple: you write a virus, a piece of malicious code that you are going to launch against a specific organization, and then you upload it to this cloud-based service. And the bad guys run your virus against twenty to thirty antivirus products, and they produce a nice little PDF report with pretty graphics and charts showing how your malicious code was detected. And they even give you tips on how better to avoid being detected in the future. It’s a cloud-based quality assurance service for malware authors. What the hell is wrong with the world? It’s insane.
These guys now are diversifying out into providing exploit toolkits4. Some of them even provide for relatively high price profiling of specific organizations that you want to target, so that your success rate when you go trying to knock on that door is very high. These services are an absolutely terrifying trend, and at one point they are starting to defeat the technologies that we’ve all relied upon for the past twenty years to keep ourselves safe.
This is astonishing. You go online, you type in trying to buy your Viagra and you get redirected to a Canadian Pharmacy site through black search engine optimization, or perhaps, you know, if you are clicking on the link in a spam message. And for some reason, everyone trusts the Canadian, it’s a good place to buy drugs. You are typing your credit card details, click ‘Buy’, and the bad guys run off with those details, go and spend lots of money from your credit card. Your bank locks the card down, replaces it, and hopefully you’ve learned your lesson. That’s been the model for a very long time.
What we’ve seen over the last year that’s interesting is these sites have actually started sending out the product. So you can go online, type in your credit card details and they actually do send you, say, performance enhancing drug. And it works. And don’t ask, it was one of the most interesting tests we had to perform at Sophos Lab compared to conventional file analyses, but anyway… What they are sending you is a cheap Chinese knockoff, not the officially branded product. And they are sending it to you, you believe it is working, you believe that it is the premium product, and they are stealing money from you on an ongoing basis, a subscription theft model rather than a one-hit wonder, because they’ve realized that overall that’s far, far more profitable. So that’s a structured decision to use a different business model for profit. Quite a terrifying trend.
For example, if we look at the breakdown of vulnerabilities in the most popular crime kits out there at the moment, you can see the lion share focus is on PDF. And interestingly, if you go to any CISO1 and say “When did you have MS08-067 (the Conficker2) patch deployed?”, they’ll know. It may have taken two days, it may have taken a month, but they will have a solid picture. Ask them what version of Adobe PDF they are running, and they through their hands into the air and have absolutely no idea whatsoever.
The bad guys know what we in IT all suck at – deploying, and that’s what they are targeting. These exploit packs make it really easy for the bad guys to go after things like PDF, Internet Explorer, Firefox, and Java – all the things that aren’t so well controlled in the IT environment. So good for Microsoft that they’ve managed to get themselves out of the frame to a large extent, that patching is paying off to security responsiveness. The bad guys are now targeting the application layer, and we all need to be thinking about how we keep apps up-to-date.
Another terrifying trend of 2010 that will undoubtedly continue in 2011 and 2012 – fake antivirus. Now, if imitation is the highest form of flattery, then antivirus companies should be very flattered indeed.
Anyway, they sit there and they think: “Right, the IT administrator told me about viruses and worms and trojans, and how they wirelessly connect to my fridge and put my milk off and scare my cat at 2 a.m.” They get the details wrong but they basically know that viruses are bad. So they type in their credit card details to ‘register’ the product to clean up the malicious code, compromising their personal finances, providing an attacker with backdoor access to a corporate asset and the access to data, and potentially joining it to a large-scale botnet.
The astonishing thing here is that it used to be free to get infected with malicious code, but now people actually pay for the privilege. People pay to run malicious code from the bad guys. And these are all over the web, they make Conficker look like a pussy cat.
But it’s not just Windows. We see it happening on other platforms too now as well. I am a Mac user, I have been for a long time. I had the understanding that while running a Mac I should run antivirus because I would feel bad if I accidentally infected a PC user. There wasn’t really this feeling of risk of actually compromising your own computer. The metaphor for this is Typhoid Mary, a woman that worked in a hospital in the U.S and was a carrier of Typhus and could infect other people, but wouldn’t actually become ill herself.
Some of these products actually have support, you can call them up and get technical assistance on how better to use their fake antivirus, it’s insane! But if you are a Mac user, if you are a CEO regularly giving presentations, if you are in a creative team, if you are in IT sitting there with lots of access to privileged information – be aware that the bad guys are targeting you too now, and you need to be protecting yourself appropriately. Times have changed.
The other big trend that we are at the beginning of the wave – we will certainly see more of it in the next couple of years – is mobile. I just have to say this – really, mobile. For the last seven or eight years, certain vendors, certain parts of security industry have been running around, waving their hands in the air saying: “This is the year that all of the malware will go from the Windows PC, and it will stop targeting them, and it will affect Symbian”. And, you know, every year nothing happens.
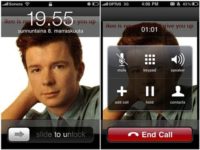
Over this year, we started to see malicious code. I am showing here the consequences of the first known malicious code for jailbroken iPhones, which you knew you were infected when this picture of Rick Astley came up in the background with the line: “Ikee is never gonna give you up” – apologies for that inadvertent rickroll. It is rumored that Rick Astley was Rick-rolled by his own phone, but no one has been able to confirm that for me yet.
This malware may be low distribution, but it is the beginning of a huge trend. The reason the bad guys haven’t been targeting these platforms is not because they are eminently secure, actually they are a bit like Windows 95; the reason is that until recently there wasn’t interesting data on these platforms to steal. But as we all use these devices more and more as a replacement for our laptop, as they become more and more a part of our lives and our identity – they are going to be more targeted.
So we need to see people focusing on protecting these devices. It’s not about the same protection model as the conventional PC. It’s not about antivirus in the same sense. But we do need to be thinking about compliance, patching and security to keep these devices safe.
Now, I’ve talked a lot about threats and malicious code but it wouldn’t be right to talk about the bad guys without getting a little bit into social engineering. The bad guys love social media, brilliant tool for them to do social engineering. And it is not due to vulnerabilities in the platform, it’s just that social media is a really good way to reach lots of people and interest groups.
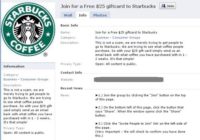
However, in the digital world we don’t have the same equivalent. The very first sentence on this page says: “This is not a scam”. What does that mean? It’s a scam. Of course it’s a scam. And any economist is immediately gonna be going: “25 dollars of free coffee which you can share with all of your friends: okay, the world has free coffee for about four days. Probably cannot afford to do that”.

These bad guys were too lazy to write a virus. They put the code on the page, they asked people to run it, and people did! What? Is that simple – social engineering. Thousands and thousands of people joined this page and followed these instructions before the page was torn down, all in attempt to get their 25 dollars of morning caffeine.
To add insult to injury, at the end of it you get to go to this wonderful official page which has got a padlock on it that says: “Zero fraud tolerance”. Good to know this criminal gang wouldn’t be sharing my details with other criminal gangs. And the page says: “We are now just minutes away from being complete”, which is fascinating because I started off this journey hoping for 25 dollars of free coffee. Who knew social media was so powerful that all of my life had been leading up to this very moment? Brilliant social engineering, incredibly effective.
So the challenge we have is that the bad guys are not only using more affective technology, they are not only producing a much, much larger volume of malicious code, they are not only taking advantage of our stereotypes, of the fact that we need to protect a Microsoft PC and not other platforms – but they are diversifying away from these expectations users have on how they are going to get infected. They are moving beyond email and simple web. They are using social media. They launch incredible campaigns, and users aren’t updating their knowledge to know they need to not click those nasty links.
And there are some astonishing examples of these diverse scam techniques, like letters resembling the ‘traditional’ Nigerian scam. But they print those and put official logos on them, and post them to people. Now, most users, if you send them a link saying: “I am going to sell you a Rolex for five dollars” these days will probably delete it. There’s always one, but the success rate is much lower. How confident are you that your users will apply the same sense to social media on the mobile platform, or if they received a targeted letter?
So we need to be thinking about broadening the tenets of our acceptable use policy. Incidentally, if you are wondering what we did with the letter – we shredded it and posted it back to them for fun.
So, what have we got to do? The bad guys have fundamentally changed the game. The volume of malicious code, the quality, the quantity is making traditional protection unsustainable. It’s not working. Signature AV, traditional AV is dead, nails in the coffin, incinerated – game over. We all have to modernize our approach to protection. We all need to be looking at tenets like content, reputation and behavior.
We need to be thinking about remediation and hardening. We need to be making sure that we are patching things like Firefox, these other applications, raising the profile of our systems, not just the Windows PC.
To the security industry, the most critical message is this: most security technology for many years has been based on the concept of content, matching files, matching packets. It is too easy for the bad guys with these tools to generate massive quantities of malware that makes content-based detection fail.
All these things like advanced persistent threats, samples that will never be seen on a large scale – make content security fundamentally challenged. We need security technologies to be building in the concept of reputation and behavior. It doesn’t matter what PDF caused Adobe PDF to go off and start trying to create Admin accounts. What matters is it’s doing something bad. So we need these tenets to be built-in across the industry.
So, what should you do as a user to keep yourself safe, to drive cyber victory – it is our Internet, the bad guys cannot have it? You need to go back to the office, you need to make sure you are patching PDF, Flash, Firefox; take advantage of the good work that Adobe and others are doing.
You need to make sure that you are adopting and using behavior and reputation based capabilities, modernizing your protection portfolio. And you need to make sure that you are thinking about more than just the PC. Think about where all that valuable data flows across your environment, and have appropriate controls at each point.
And to the industry – simplify. The reason people don’t use technologies like HIPS1 is because they get these screens that say: “Right, there is a mob here, now turn it to the left, and of course now the A vector of anthological analyses engine with kernel32.dll on Internet Explorer, when accessed by user B, and IP address is C at 13:37 on Tuesday when the North wind is going this way and my hair is particularly ginger…” What on Earth does that mean? Where is the checkbox that says ‘Stop bad stuff’? We have got to make this stuff simple and adoptable. People don’t have the resources to be chasing all this flexibility and dealing with 95000 threats a day.
We’ve got to, as an industry, drive policy centrally, take advantage of community intelligence and make this stuff work for the customer. And please stop using the term ‘SaaSification’.




























