Robert David STEELE Vivas is a native New Yorker who has lived practically all over the world. He is best known for promoting the ubiquitous use of Open-Source Intelligence (OSINT), and more recently for his latest book, “THE OPEN SOURCE EVERYTHING MANIFESTO: Transparency, Truth & Trust“.
Steele is a former clandestine operations officer with the CIA. He served three overseas tours focused on terrorists and extremists. Returning to Washington he managed global counterintelligence for a denied area target and then served in two other of the CIA’s four directorates doing advanced information technology (after which he was selected into CIA Mid-Career Course 10).
He left the CIA to serve as the second-ranking civilian in Marine Corps Intelligence, responsible for setting up the Marine Corps’ intelligence center while creating a new global analytic model that fully integrated military, civilian, and natural factors, each with three to five level of difficulty. All of it – sources, methods, and finished intelligence – was unclassified and shareable with foreign coalitions and the public as well as every member of Congress.
Steele is against unwarranted secrecy and torture in any form — he was among those who signed the letter to Senator John McCain. He has, since his articles in the 1990’s and his first book, “ON INTELLIGENCE: Spies and Secrecy in an Open World” (2000), been arguing that U.S. intelligence reform is desperately needed, and that the private sector can perform a high percentage of U.S. open-source intelligence needs and reduce the cost thereof to the U.S. government. As the foremost pioneer in the world for modern OSINT, his focus has been on sharing instead of secrecy; on making sense instead of producing secrets, and on leveraging open source and methods to provide universally-transparent ethical evidence-based decision-support.
He is one of a handful of pioneers of “Collective Intelligence” and was among the first and is still among the most committed advocate for hackers as a national resource — “like astronauts, pushing the edge of the envelope, full of the right stuff.” Like one of his heroes, Michel Bauwens, he also advocates peer-to-peer technologies in every aspect of our life, recommending an “all in” approach to all the opens together. Steele specializes in multinational information sharing, harnessing the distributed (and largely volunteer) intelligence of the Whole Earth, increasing transparency, empowering bottom-up self-governance while striving to eradicate fraud, waste, and abuse – corruption – through the creation of public intelligence in the public interest.
Steele’s Open-Source Everything philosophy – unusual for a former spy – was presented in 2007 at Gnomedex; the keynote speech: “Open Everything: We Won, Let’s Self-Govern” has become cult viewing within many communities including Anonymous.
In 2011 Steele became one of the three original candidates for the Reform Party nomination for the presidential race in 2012.
Steele has written 1880 book reviews on Amazon, and is the #1 reviewer for non-fiction, reading in 98 categories. He is the author of numerous books on intelligence and information operations. Book in progress: “Intelligence with Integrity: Enabling Hybrid Public Governance with Open-Source Decision-Support.”
Steele’s work — and that of 25 other contributors as well as archived materials from over 750 international authorities on OSINT — can be seen at Phi Beta Iota Public Intelligence Blog – “The truth at any cost reduces all other costs.” Today he is unemployed and seeking righteous work anywhere in the world.
– Robert, you worked with the CIA in the midst of the Cold War when the KGB was your main adversary. The USSR is long gone now, and much of the warfare has moved over to computer displays, so to speak. What is your viewpoint concerning the chance of a real cyber-war breaking out? If it happens who can be the major opponent to the US in it?
– First off, let me say that when it was my privilege to be in the clandestine service, we did everything. The KGB certainly was the first priority, but we covered virtually every target of possible interest.
Now to your question. The chances of a cyber-war are the same as the chances of Y2K bringing down the economy – zero. As with nuclear war, no one wins in a cyber-war. Much more likely is a pathetic melt-down stemming from continued government and corporate irresponsibility with respect to the security of Supervisory Control and Data Acquisition (SCADA) systems, as well as personal financial and communications information.
I would also point readers to Mark Bowden’s “WORM: The First Digital World War”, which ably makes the point that no one in the USG is doing anything relevant to defend us against a cyber-war – the heavy lifting is being done outside the government, despite the fact that this has been a primary responsibility for the National Security Agency (NSA) since the 1990’s. I wrote the warning letter in 1994 that was ignored, and more recently, in 2010, I wrote a piece on “America’s Cyber-Scam” for Homeland Security Today.
Much scarier is the very high probability that small groups, whatever their motivation, will attack specific cables that are easily identified – as I used to lecture years ago, we make it easy by identifying cable entry and exit points at the water’s edge. Just today there is a story out on three Egyptians captured 750 meters offshore who actually found and were cutting a major cable that could have taken an entire continent (Africa) offline. This is one reason I feel very strongly that we must create an Autonomous Internet that is impervious to both non-state actor attacks and state attempts to censor or close down civil Internets.
As long as our government fails to act in the public interest, it is the greatest threat to our continued security and prosperity, not any other contrived or inflated threat.
– What do you think of the CIA’s current human resources from an IT professional perspective?
– Gus Hunt is the best of the best within a rather limited lot. The Amazon initiative is a good idea that will be badly managed by CIA – Amazon will fail, as Google failed in its early days with CIA, because CIA has multiple issues, I commented on this online. In 1985 Gordon Oehler, Diane Webb, and Dennis McCormick, clearly established the eighteen functionalities needed at the desktop level for all analysts, and we still do not have that today (nor do analysts have access to all relevant open sources and all relevant classified sources). There are in my view three persistent problems with CIA, NSA, and all others including USG generally:
1) these people are still bogged down in buying the T without a clue about the I – something Peter Drucker in 1998 and I in 2002 (speaking to NSA) have emphasized as central;
2) Reptilian security mind-sets are a fatal cancer – a cultural mind-set that consistently strives to pay for worst case security while over-looking the opportunity cost of keeping analysts inside a bunker with no air;
3) there are no adults with authority over USG and IC IT – no one with financial authority is forcing the issue of integration and interoperability at the code and data level.
OMB and GSA do what they can in the search for common solutions, but the reality is that secrecy and accountability are incompatible, and the degree of ignorance and arrogance among USG CTOs cannot be understated. I served on the Information Handling Committee (IHC) as well as the Advanced Information Processing and Analysis Steering Group (AIPASG) in the 1990’s, and have supported major commands with up to 23 non-interoperable software implementations in the past decade and the bottom line is still the same: CTOs have not learned the fundamentals that Paul Strassman has written about is all of his books including The Squandered Computer: Evaluating the Business Alignment of Information Technologies.
– Mr. Steele, is there anything you regret about or would have done differently if you could just go back to the 80s and start it over?
– I have agonized over this question. I and my family have paid a very heavy price, not just financially, for my staying on a righteous path for 20 years while being bitterly and crudely fought at every step by CIA’s Open Source Center (OSC) and the secret agencies that corrupted my vision by insisting that all OSINT be classified and that all contractors doing OSINT be US citizens with clearances (“butts in seats” surfing the web). OSINT is being treated as a technical discipline and this is flat out wrong. OSINT is a very broad extension of Human Intelligence (HUMINT) and needs to be done face to face and in 183 languages. That’s too hard for the CIA’s mix of bureaucracy, “security”, and insouciance , so it is not done. We need an Open Source Agency (OSA), as recommended in the 9/11 Commission Report on pages 23 and 413, but under diplomatic or commercial auspices, or perhaps even as part of the Office of Management and Budget (OMB), to inform all planning, programming, and budgeting decisions across Whole of Government. There are two books I recommend, Hamilton Bean’s “No More Secrets: Open Source Information and the Reshaping of U.S. Intelligence”, and Anthony Olcott’s “Open Source Intelligence in a Networked World” (2012).
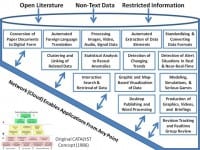
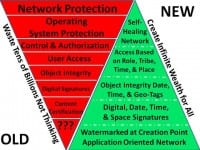
I do not for one minute regret my 20 year walk-about, and the many countries, organizations, and individuals it has been my privilege to encounter. It may well be that five years from today I will conclude that I had to do the walk-about in order to turn the Titanic into clear waters. However, if I had to do it over again today, instead of resigning I would seek a transfer to OMB, create an OSINT budget line, and ultimately consolidate all OSINT services of common concern in an Open Source Agency (OSA) that nurtures ALL of the opens across government and the nation and then the world, while teaching and funding internal decision-support capabilities within every government elements, and then pressing for various Smart Nation initiatives such as Congressman Rob Simmons (R-CT-02) and his staff and I put together in a draft Smart Nation Act. He lost his last election by 80 votes, and our movement toward the restoration of intelligence with integrity lost its only champion in Congress. The biggest change in my perspective has been the realization that OSINT means nothing if it is not accompanied by – enabled by and leveraged by – all the other opens, some of them depicted in the above graphic.
I have recently posted a graphic intended to help US government consumers of intelligence begin the process of documenting the failure of the secret world to satisfy them, the first step in submitting new budget requirements that propose a reallocation of funds from the secret world of largely useless collection (corporate vaporware, most of it not processed or analyzed), to the consumer world of necessary timely production. This is how we restore intelligence with integrity to Whole of Government.
Others are better suited than I to take the other path, that of collective intelligence and wisdom of the crowds. Although I published the first book on Collective Intelligence, with 55 contributing authors, right now the technology is not there yet but is coming along at a phenomenal pace. Google and Facebook are bloated; Twitter is lagging – right now I am looking at International Crisis Mapping and all of the open softwares that Dr. Patrick Meier is identifying – I expect a massive convergence with BitCoin, OpenBTS and Open Spectrum, and then the World Brain and Global Game will evolve at their own natural pace.
– How do you view the proportion of physical and cyber terrorism in the next 5 years? In your opinion – which type is worse?
– Neither. I believe two things: first, that many terrorists are false flag terrorists that have been funded, trained, or manipulated by rogue government or corporate sources who desperately need terrorism as a substitute for the Cold War; and second, that terrorism is a tactic, not a threat, and it is a tactic that is used by groups with legitimate grievances when they feel they have no other resort. The CIA is retarded when it comes to understanding cultural and tribal movements – in 1979 I gave them my first thesis on predicting revolution; in 1986 I sat in on CIA workshops on revolutions; today I look at what the National Intelligence Council is producing – “Global Trends 2030” for example – and I have to conclude that CIA lacks both intelligence and integrity. Good people trapped in a bad system, with the managers not held accountable for diverting thousands of people and billions of dollars to drones doing extrajudicial assassination, continued rendition and torture, and very little attention to what really matters – climate change, for example.
CIA just closed its “Center” after years of its doing nothing of substance. For both the invasions of Afghanistan and Iraq, it was my company, not CIA, that provided the tribal maps and attitude surveys to the US Special Operations Command. CIA still does not have a model for predicting and remediating revolution such as I developed in 1976 and have applied on several occasions for commercial exploitation. Anyone who claims terrorism is the top threat to humanity is ignorant or lacks integrity and is lying for effect. One of my most popular graphics is Graphic: A Short Story-Terrorism as a Boil (see image), it puts all this nonsense in perspective.
Please let me take a moment to list, in priority order, the top ten threats to humanity. These are as identified by LtGen Dr. Brent Scowcroft, USAF (Ret) and the other members of the United Nations High-Level Panel on Threats, Challenges, and Change, in their report A More Secure World: Our Shared Responsibility, and they have been ignored by the USG and all other governments.
2) Infectious Disease
3) Environmental Degradation
4) Inter-State War
5) Civil War
7) Other Atrocities
8) Proliferation
9) Terrorism (Mass Catastrophes)
10) Transnational Crime
Poverty has doubled in the USA in the past twelve years. Around the world poverty does more to spawn all the other threats than all the corporations put together. In the USA the unemployment rate is 23%, with 40% being the rate for new college graduates and old guys like myself. The diseases that are being created and spread by our unhealthy agricultural, food, and industrial practices is beyond comprehension. What we allow in the way of genocide and trade in women and children – including a thriving slave industry in the USA, a mix of prisons that out-source labor and migrant workers held at gunpoint—is reprehensible—I strongly recommend John Bowe’s “Nobodies: Modern American Slave Labor and the Dark Side of the New Global Economy”. Not only is terrorism not a real threat, but transnational crime, previously defined by street families doing gambling, drugs, and other relatively minor illegal crimes, has now been eclipsed by Wall Street and its legalized destruction of entire economies through blatantly fraudulent derivatives, mortgages, and hedge fund transactions. What we have done to ourselves in accepting 935 now documented lies to go to war in Afghanistan and Iraq has not only cost us over $4 trillion dollars, but will be a cost to our society and those societies for a half century into the future. This is all insane, and so unnecessary. All we need to change it is to dismiss the two-party tyranny and re-establish an honest government Of, By, and For We the People.
– Please list the top 3 high-risk technologies and the possible consequences of them being utilized?
– Vaccines that produce infertility and other diseases; Genetically Modified Organisms (GMO) that are killing crops and people; and compound interest. I am stunned by the lack of integrity in global health as well as domestic health; by the lack of integrity in agricultural and food oversight; and by the fact that just one Koch brother is earning $3 million an hour in interest while too many citizens struggle at $2.13 an hour plus tips. Worse than any technology is a corrupt culture. I urge one and all to read Charles Perrow’s “The Next Catastrophe: Reducing Our Vulnerabilities to Natural, Industrial, and Terrorist Disasters” along with David Callahan’s “The Cheating Culture: Why More Americans Are Doing Wrong to Get Ahead”. Technology is not a substitute for thinking – or ethics. The latter was the whole point of E. O. Wilson’s complex and brilliant “Consilience: The Unity of Knowledge” and also John Ralston Saul’s “Voltaire’s Bastards: The Dictatorship of Reason in the West”. Ethics, not technology, is our 21st Century challenge. Engineers bend metal and crack code – they are challenged when it comes to the nuances of ethics. I am still fond on my invited rant to INTERVAL in 1993, “GOD, MAN, & INFORMATION: COMMENTS TO INTERVAL IN-HOUSE”. It could be given today to any of the big IT corporations, and they still would not get it.
– At The Fifth HOPE in 2004, you predicted an explosion in on-demand tailored intelligence during the following 5 years – to what extent were you right?
– I was completely wrong, underestimating both the idiocy of the public in re-electing George Bush and his nakedly amoral Vice President Dick Cheney, and also underestimating the degree to which Google, Facebook, and Twitter would all refuse to get serious about sense-making. And of course we had a collapse of the economy. As you know, in 2007 I gave the capstone briefing at Amazon, and also spoke at Gnomedex, and had high hopes for Amazon becoming the hub of the world brain, but it was not to be. However, coming back to Crisis Mapping and the pioneering work of Dr. Patrick Meier, while also bringing forward the true costs economics theory and practice that I hope earns a Nobel Prize for Dr. Herman Daly one day, I believe we are getting very close to being able to link all minds in all places with all data at all times – and then do flash mobs and smart swarms on any topic. Put enough eyeballs on it, and no corruption is invisible. CIA had a chance in 1986-1988 to change the world, and chose to blow off its internal iconoclasts. All of the innovation now is on the margins, far from both CIA and Google and IBM – a few exceptions not-withstanding.
– Should hackers go into government to speed up the transition to the new order, or should they perhaps stay who they are so as not to lose positive traits and be more useful to society as they are now?
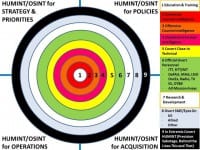
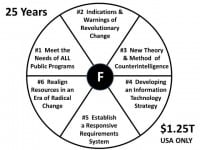
– Hackers tend to be self-taught individuals who lack the educational credentials the government demands. As I and others have found, government tends to grind down or expel the innovators, and is still managed to the lowest common denominator, usually managers whose last bit of education was 20-30 years ago, motel courses not-with-standing. I still believe in government, but I fear that government is not going to change until we abolish it and start over. At this time I believe hackers are best served by inventing new ways for We the People to connect – including an Autonomous Internet that cannot be shut down, see also Freedom Tower and Freedom Box – and to think, meaning raw true cost data as well as tools for analysis and visualization. The secret world has spent over $1.5 trillion in the past 20 years, and it still does not have an all-source desktop analytic tool-kit or a government-wide secure information-sharing and sense-making network, nor has it achieved the >six basic challenges I identified in 1990 (see image above). This is not a technology challenge, this is a cultural and mind-set challenge. Between political bums at the top and bureaucratic followers at the bottom, there is no middle ground where radical change can take place.
– What are your personal goals for 2013-2014 in the context of building collective intelligence?
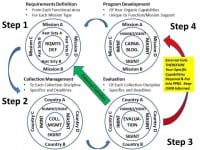
– First off, I am a pebble on the beach. Collective Intelligence has taken on a life of its own, and the more we can get people to go “all in” on Open Source Everything (OSE), the faster that is going to go. My primary service appears to be as a proponent for a comprehensive architecture, a term coined by Buckminster Fuller. Without analytic models and agreed upon priorities for data collection and data sharing, it will be harder to arrive at collective decisions about anything. This is why I funded the Earth Intelligence Network in 2006, and why I believe the Strategic Analytic Model it developed should be adopted as a starting point for public intelligence from the zip code level on up to global.
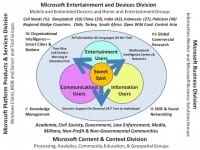
I am applying for a Yahoo! Fellowship at Georgetown University, and have also applied for a number of jobs in both government and the private sector. On the one hand, having been unemployed for four years while I had no clearances, my first priority is to get a job that helps support my three kids in college and the house – we have been living on savings and my wife’s salary as a government employee. I am globally mobile and have also provided the Microsoft CTO and Sir Richard Branson with some ideas (see right-hand image), I have been blown off by the Microsoft CTO and am told that I should get an answer from Sir Richard sometime in April.
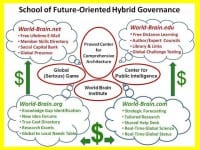
The Secretary General of the United Nations and the President of the United States have received proposals from me that I am quite certain they have not seen – the ability of the bureaucracy to block out new ideas is quite strong, in part because today the government – and the UN – operate at the policy level on the basis of who pays to be heard. I continue to believe that we should create a single World Brain Institute that serves as the architect for the World Brain and Global Game as well as the proliferation of Centers for Public Intelligence – hackerspaces for bringing minds and data and tools together – while also championing an Autonomous Internet, open money – I am glad to see BitCoin joining with Expensify, something Richard Falkvinge pointed out to all of us this morning. I tried and failed to get George Washington University to adopt the World-Brain cloud concept and related centers shown here (see left-hand image above) – if there is any university anywhere in the world that would like to do this, I own three of the four URLs and will donate them to a term effort – my briefing to the Washington Academy of Sciences is online.
– Regarding collective intelligence, what criteria will help people evaluate the information they seek? Will security tools for evaluating trustworthiness be essential or will perhaps each individual or community decide on their own, utilizing newly developed skills?
– Long ago, at the Hackers Conference in Silicon Valley, we had this discussion. I vividly remember one of the others saying that the future of information would be closely linked to the reputation of the originator. We are moving into an era where credentials are suspect and the smartest person in the future may be a 15-year-old girl in India that earned her PhD free online… And as David Weinberger has articulated so elegantly in his last two books, Everything is Miscellaneous, and Too Big to Know, not only is all information in the mix, but no one individual can “know” anything. The future of collective intelligence is in the subtitle of my next to last book, INTELLIGENCE for EARTH: Clarity, Diversity, Integrity, & Sustainability.
Tools can certainly help – I have been impressed by the advances made in bounded crowdsourcing – trust source can recommend 1-more other trusted sources (e.g. GDACSmobile) as well as redundant crowd-sourcing – 2 or more must agree (e.g. Zooniverse). In the end I believe that individuals will have different levels of trustworthiness across various domains – low on money management, high on hobby specialization, middling on work focus, etcetera. Right now our educational system sucks, employers are decades behind in adapting to changes in everything, and the government is in enemy hands (the two-party corrupt tyranny). For me the bottom line is that human intelligence and human ethics can be augmented and assisted by tools, but as Jim Bamford has put it so ably (see image above), for all its trillions NSA still cannot match a single human brain.
– What type of search engines do we need? Will Google stay or go?

– One of the great things about nurturing OSINT has been the quality people I have met all over the world. Many of them are right here in the USA. Stephen E. Arnold of Arnold IT is the person I most rely on to understand where the industry is going. Below is his answer, followed by my own thoughts.
“Search will evolve in two directions. Predictive systems. These will provide search based on user behaviors, location, and past actions. Faceted systems. These will display suggestions and timely content and offer a search box. The “good old days” of Boolean queries, parameters, and advanced syntax are not usable on some mobile devices and run counter to what those under the age of 40 prefer. Google will stay. It is an ad delivery system. Search is one means of hooking ads to users’ information needs.” Stephen E. Arnold.
While I admire all that Google has done, Google disappoints on multiple fronts. Google is a threat to virtually every industry that has any form of content, and I consider Google predatory and unethical – predatory in trying to copyright stuff it digitizes, and unethical in how it treats private information including Google Enterprise data. Google is doing nothing to help people share information in context or make sense about anything in relation to time and space. Of course I like Google mashups, and I consider Google Maps one of the most extraordinary contributions of all time, but in the end Google lacks the comprehensive architecture and the common services needed to create the World Brain and Global Game – not because it cannot do this much-needed common structure and service, but because its leadership refuses to go to the next level.
My personal priority for search – recognizing that less than 10% of all knowledge is online and that only 2% of that 10% is searchable – is multilingual text search and geospatially and time-based search. When I helped create the concepts for advanced workstations and the Marine Corps Intelligence Center, my number one requirement was to be able to type in “Tell me everything there is to know, in any language,any medium (audio, video, image both overhead and hand-held, text, kanji) about this one spot on the face of the Earth.” Not only can we not do that, but the $75 billion a year US intelligence Community cannot do it either – they are still suffering 80 different databases, each with their own search, their own security, their own protocols, their own bureaucracies.
My next priority is originator’s persistent ownership and control. One of the coolest things I ever experienced, in the late 1980’s, was the ability to follow an official email and see where it had been copied, forwarded, etc. Information is art – it has a provenance. In order to get all information searchable, we have to dramatically enhance end-user authenticity and Creative Commons rights including the right to follow one’s information everywhere it might be used, translated, etc. This is where I think CISCO has blown it. John Chambers probably never got the letters I sent him. I like CISCO – but if it will not listen, it will not scale.
As for where Google will go, I would certainly refer everyone to Stephen E. Arnold’s “Google Trilogy”. I had very high hopes for Google when Vint Cerf signed with them, and started losing hope when Larry Brilliant left them. Google has been surviving on investor cash and I do not think advertising will carry them much further. Where Google has gone wrong, in my humble view as an unemployed person, is in falling prey to the paradigms of secrecy instead of sharing, and copyright/patent dominance instead of setting open standards. Their computational mathemaitics is from another planet, but they are not lifting all boats. If I were empowered I would combine 2012 Steele for Branson: The Virgin Truth 2.6 (see image) with an Open Source Agency (OSA), sponsor a global competition for an affordable OpenBTS smart phone, and give Twitter and Amazon as well as Google and CISCO and IBM, one chance to come to the table and play well together. My bottom line is that proprietary is unaffordable and does not scale – the center of gravity for the future of IT is the five billion poor, not the one billion rich. India gets that, the US-based companies do not.
– What recent events or trends in OSINT do you think were most commendable?

– Let me begin my answer to this question by pointing to the recent judgment, BGen James Cox, CA (Ret) On the Record on Open Source Information versus Open Source Intelligence versus Secret Intelligence. He is the flag officer that got over 66 countries to adopt OSINT as a separate discipline, and also sponsored the three NATO documents on OSINT.
“I can say that even during what was done and the establishment of an ‘OSINT’ cell in the SHAPE Int staff, I never thought that anyone had it fully ‘right’. By that I mean, when the OSINT cell was raised in SHAPE, all they did was collect open source information, mainly from print media like Jane’s, the Economist Intelligence Unit and Stratfor, and feed it to the small analytical staff. There was no analyizing the open source information in its own right and producing ‘real’ OSINT from it. … The process, to my mind, simply stopped at “OSINFO” and never got to “OSINT”.”
I agree with that. With the exception of InfoSphere AB in Sweden (which uses the SILOBREAKER information toolkit), I know of no one that actually produces OSINT, and I certainly include the CIA OSC and all of the contractors supporting all of the USG elements paying lip service to OSINT in the non-performance group. They do OSINF, not OSINT.
There are stellar performers in specific niches – Bob Heibel in academia, Crisis Mappers in civil society, Mary Ellen Bates and Ran Hock in teaching information brokerage, Mats Bjore (InfoSphere CEO) in commerce, the US Special Operations Command (J-23), Scotland Yard SO-11, Janes and then Oxford Analytica under Alfred Rolington, and the Red Cross (34 wars at a time) – but generally, OSINT is simply not done. Jim goes on to say: “If I was king of the world, I would build an OSINT organization to rival existing national SIGINT organizations (CSEC in Canada, NSA in US) and HUMINT organizations (CSIS in Canada, CIA in US). This OSINT organization would be in a number of big buildings around the country, tapped into all the sources you have long written about (media, experts, academia … all tribes) AND they would produce magnificent ‘single source’ OSINT products that could be added to SIGINT, HUMINT, IMINT etc. products at the national level.”
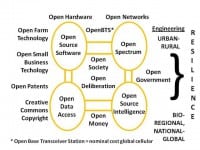
This is of course precisely what I have been trying to get started for 20 years, with the major change being that in the past ten years I have come to realize that OSINT without OpenBTS, Open Cloud, Open Data, Open Hardware, Open Spectrum, Open Standards…all the opens, is too subject to the corruption that pervades our entire society. OPEN is the antidote, but OSINT alone will not do it.
– Cameras and sensors are monitoring us already, and there is a growing tendency of utilizing these systems to punish people for various types of offense. To what extent do we need technical law enforcement? What should be left in human hands?
– Zero tolerance is ultimately fascism. Who makes the rules? Micro-management is what Gary North and the Libertarians call an Administrative State. These technologies result from bribes to Congress that move money to the Department of Homeland Security (DHS) and thence to local law enforcement. Federal money has in my view destroyed law enforcement across America the Beautiful. Today we have constant surveillance that is not processed, and SWAT teams, instead of cops on the beat and community-based policing. It’s insane. I pray for some form of revolution in the USA, one that shuts down all federal waste, all federal borrowing, and all federal intrusion below the state level into social issues.
– How would you characterize the current state of things around computer and Internet security? Are you seeing any good new tendencies? Do you think it will get worse or better within the next 3 years?

– Here is what my esteemed colleague Winn Schwartau has to say, followed by my own comments.
“As abysmal as ever. Sure, we have improved defense (CND) in some areas, but lowlan APTs are virtually undetectable with current technology and undetected penetrations go on for an average of 416 days. We have continuously spent billions on technology when the majority of the problems are the human components. The best new tendency is the ability to blame China for everything, but that only deflects the true problems so endemic throughout enterprises. Re next three years, we are hosed. It’s going to keep getting worser and worser… and it will be much worser if Congress attempts to legislate what they cannot begin to fathom.”
Anything less than code-level security and data at rest encryption that does NOT have a negotiated back door with NSA, which has totally hosed the security of US commercial communications for its own convenience, will not do the job. I do not follow this area but I can say with certainty that nothing is going to get better in the next three years – the Obama Administration gave Open Government lip service, and then ignored the #1 demand made by a majority of the 4,000 people that participated – the legalization of marijuana. As goes the Republic, so goes security. We’re over the cliff and in free-fall. Congress is corrupt to the bone, such laws and regulations as we have are bought and paid for, not in the public interest.
– In terms of computer security, what are the short-range tactical solutions for each individual or business, like what should a company do in 2013 to not be breached?
– Winn’s answer: “There is NO perfect answer. Establishing more controls over what humans can do and access is critical. Buidling in my TBS formulas to processes would be a big step. Use superglue on all USB ports. DO NOT use mobile devices for business, especially BYOD, unless your security implementation includes everything you currently use in the fixed enterprise. Only use HTTPS on servers; use AES256 on all non-enterprise comm and all wireless. Vet and profile your mission critical folks on a regular basis to avoid the Hanson/Ames issue.”
For companies that really want to be secure, they have to get off the electrical grid. As NSA has discovered to its great dismay in recent years, the Chinese have perfected (scaled) what you can buy at Best Buy for extending Ethernet via any two sockets – riding the electrical wires into any computer. Personally, I don’t think our companies have many legitimate secrets – what they all seem to be eager to hide is their criminal misbehavior against their employees and their pension plans. Since the FBI is not doing its job, I’m all for public counterintelligence against all targets.
– What do you think of biohacking, haptic implants, subdermal electronics?
– We cannot understand our own government, much less Mother Earth. While I am a huge believer in bio-mimicry, I am scared to death of anything that presumes to manipulate or mutate natural processes centuries in the making. Until we can finally achieve free quality education for everyone, I would hold off on any “interventions”. Show me free energy and free desalinated clean water and free cell phones and free Internet access for everyone on the planet, and I will be less worried. The “Precautionary Principle” applies, and is ignored by everyone with enough money to buy liability exemptions from Congress.
– Commenting on Bruce Schneier’s book “Liars and Outliers”, in particular his words that the Stuxnet cyberattack by the U.S. was a destabilizing and dangerous course of action, you wrote: “Bruce Schneier is wrong. This is not something that cannot be micro-managed.” Could you further elaborate on this perspective of yours?
– I certainly agree that Stuxnet, which was an Israeli initiative not a US initiative, was destabilizing. It has bled over to other countries. What was written at Phi Beta Iota by the editor on duty was:
To this I would add myself that Robert Garigue’s pioneering work before he died all too young at 50, put the emphasis where it needs to be put: security is about trust, not control and security must be decentralized and cannot be centralized. It is not possible to micro-manage agility, insight, and trust. Will Durant’s 1916 thesis, Philosophy and the Social Problem, is still “Ref A:” we have to educate the entire population to the highest possible standards – for life.
– Security researcher Moxie Marlinspike argues that the current online authenticity model based on Certificate Authorities is inefficient. As an alternative, he advocates the “Trust Agility” concept and such models as “Perspectives” and “Convergence”. What do you think of that?
– I totally agree that Certificate Authorities are inefficient and I would incompetent. They do not do the job. Here to the side is a graphic that I developed with Robert Garigue, whose memory I cherish. He did more for 21st century information security in a decade than anyone now living that I know of. I urge one and all to seek out his work and build on it. I tried at least twice to get John Chambers to rethink routers so that they could not only be recyclable, but so that individuals would have the rule-making and content control that CISCO’s Application Oriented Network (AON) offered major financial and other global institutions. In a world of infinite bandwidth, which is what you get when you go to Open Spectrum, every datum will have its own provenance of authenticity, at the same time that every individual will have multiple authenticated identities and also multiple anonymnity cloaking measures.
– Who do you consider the best influencers in information security and also in OSINT? Do you look up to anyone?
– Winn Schwartau is the only person I follow in information security, I’m sure you can provide a better sidebar on information security. In OSINT, I look up to the pioneers I mentioned above, and to all those that have made historic contributions — all 253 of them.
– Security industry uses full disclosure to develop scare-tactics and thus convince people into buying their services. What is your attitude towards the Anti-Sec Movement which is against full disclosure of information relating to vulnerabilities, exploits, attacks, etc.?
– The truth at any cost lowers all other costs.
– How would you characterize the present-day security software? How will it develop in future?
– Not a good question for me other than to say I consider Norton and McCafee to be burdensome crap. ESET keeps me very happy. I consider Microsoft totally compromised, along with all the telecommunications companies. The loss of integrity across society is for me the cancer that may prove fatal to the dream what was America.
– In your opinion, what are the ways of implementing collective intelligence in the antivirus industry?
– Open Source Everything (OSE), end all back-door security compromises with all governments, publicize every known virus and its source, and create a new global sport – open season on spammers and virus authors. Viruses are a classic case where top-down micro-management cannot possibly do well – we have to put the agility and the intelligence and the integrity at the edges of the network. I would also reiterate that nothing the government is doing now is effective in this arena, I really liked Mark Bowden’s book WORM as a concrete illumination of who is actually relevant in this arena.
– Are you personally worried about identity theft? What are you doing to prevent it?
– Being unemployed has its advantages. My family has been shredding all documents for over a decade, and I certainly recommend blocking all credit inquiries. I do feel that if Social Security Numbers (SSN) are going to be the common denominator, that we have a right to be informed of EVERY transaction that contains our SSN. That requires a government with integrity, so I am not holding my breath.
We are about to go into a further collapse in the USA, if my wife were not employed by the government I would be selling everything, buying a boat, and preparing to cast off and be mobile afloat. There is a great deal to be said about John Robb and his many ideas on resilience including community self-financing of social power and Internet micro-grids, getting off the grid. The US electrincal grid is a hair away from national collapse and sustained outages. We have much bigger problems than identity theft.
– When commenting on hacktivists’ campaigns, you stated once that anything that is preventing censorship is good. This is a serious ethical issue – is it really a good thing to fight for freedom using bad methods? To what extent can BAD be justified – as we have millions in financial losses and tons of personal info revealed?
– Well, let’s start with the fact that Goldman Sachs, AIG, Morgan, Citi-Bank, Bank of America, and Countrywide Mortgage have done vastly more damage to the world, not just the USA, I would say that any damages from hactivists pale in comparison. I would also observe that if the government were to live up to its obligations to the public interest, I would not support hacktivists doing any damage at all, but as long as the government remains unwilling to maintain the rule of law including good corporate citizenship, one has to sympathize with anyone that is avowedly working in the public interest.
The truth at any cost lowers all other costs. Until we have a government that embodies intelligence with integrity, I salute all citizen hacktivists, with the observation that I encourage them to expose – share information – rather than harm or destroy. The more we educate our public, the less financial waste and unwarranted violence we should suffer.
– There are strong concerns over privacy and security when information is shared indiscriminately – how do you plan to address this?
– I don’t address this. Every individual should be able to address this themselves. The critical point that Robert Garigue makes is that trust has to be on the edges of the network, it is not something that can be imposed or defined from a central or higher authority. What is really happening is that just as the Industrial Era commoditized human beings, now human information is being commoditized. The government has shown little regard for human rights to their own information.
– You suggest that we decide for ourselves what to share, but if we share only part of what we have – it will not really be “Open Everything”? Do you think people will share 50%? How much is enough?
– Open Everything is a platform within which anyone should have the right to choose between sharing and not sharing. Open Source includes Open Security, and assures privacy and compartmented living to the fullest extent desired by each individual.
– More sharing pushes less privacy; how to solve ethical problems of being open to the whole world? How do we adopt this concept in our minds? Currently all privacy reducing initiatives, e.g. Instagram’s recent Terms of Service, are being strongly confronted by the public.
– I strongly support multiple trusted identities that cannot be connected. Sharing must be an option that comes with protection. One size does not fit all.
– What do you think of the suggested idea of introducing Internet passports? And overall, how do you see the future of IDs/passports – will we need them?
– I like the idea but its implementation should be decentralized – no central authority is immune from corruption.
– Is it the only way for us – to live in a world that never forgets? Do you personally want to live in such a world?
– David Brin and Bruce Sterling would say asked and answered. I have no problem with a world that never forgets, I have a problem with a world that does not learn. I had the future of intelligence well defined in 1988-1994, and only now, 20 years later, are people beginning to get a glimmer, and only because we are in a financial crisis and their questionable practices are coming under greater scrutiny. Right now we are in Groundhog Day – everyone is reliving the same day over and over, but unlike Groundhog Day, the organizations are not learning, they are treading water and refusing to learn.
– You have done 1880 book reviews on Amazon. You said you joined Amazon in 2000, it means one review every 2-3 days! How do you find the time to read and review all of them? Do you read them to the end, have you re-read any books? Any time management or reading advice?
– First off, the numbers are skewed by the fact that my first 300 reviews came from the annotated bibliographies of my first two books, meaning that I had read them in years prior. I loaded all of those around 4 April 2000 and was instantly in the top 1,500 reviewers. I actually read at least one book a week, often two books a week, and when I fly over the Atlantic or Pacific, as many as ten books in a week.
Secondly, if I review a book at all, I found something worthwhile, but in a handful of cases, will take the trouble to slam a book I find especially noxious.
I never re-read books, but when I still had my library of 3,000 volumes, I would often pull down books to refresh my memory or pull a quote for a new article or chapter. When I served the UN briefly in 2010 I gave my entire library to George Mason University (GMU), and was quite pleased to see that it took three specialist librarians to evaluate it. Now I donate all books to the Oakton Public Library after I read them, which makes my summary reviews more important as my storage device.
– Final thoughts?
– 2012 is the beginning of Epoch B – the end of top-down hierarchical central control and rule by secrecy. Every crime against humanity that I can think of has stemmed from corruption and closed systems combined with an apathetic and ignorant public. I believe that we cannot create a prosperous world at peace without first scaling free cell phones and free Internet access and free education to the five billion poor. As best I can tell, Open Source Everything (OSE) is the only affordable scalable solution – and that includes all the open source code for privacy that anyone might wish to enjoy. St.