The New Zealand Police virus, also known as “Nga Pirihimana o Aotearoa” or New Zealand E-crime Lab ransomware, is targeting users physically located in New Zealand and does it in a fairly vicious way. This malicious code causes the affected operating system to display a scary-looking lock screen each time the users starts their PCs. Not only is it impossible to bypass this fake block page in any regular way – the malware intimidates its victims through accusing them of committing cybercrime.
For the user to avoid actual prosecution and get the hijacked system unlocked, the virus persistently demands a fee to be paid via Ukash, a well-known payment system based on the use of vouchers one can buy at multiple stores all of over the country. However, there are numerous apparent downfalls of following the ransomware’s requirements, which is, by the way, a very wrong thing to do because the whole system lockup thing has absolutely nothing to do with the actual institution of the New Zealand Police. Purchasing a Ukash card for paying the criminals means you go the easy way that will not lead you into getting rid of the malware at all. Whereas the noxious lock page may go away in this case, the PC will remain contaminated, which may upset you in various ways in the future.
The malicious entity underlying this entire campaign is called Reveton – a hazardous infection distributed via powerful exploit kits such as the infamous Blackhole. For infestation purposes, this cyber threat takes advantage of outdated software on a targeted computer, mostly Java or PDF. The malicious scenario usually takes place in the background, so neither the user’s consent or even awareness is necessary.
In this article we will provide a sole alternative to paying the ransom if you are infected with the New Zealand Police ransomware, namely proven advice for removing this virus.
New Zealand Police virus: versions and screenshots
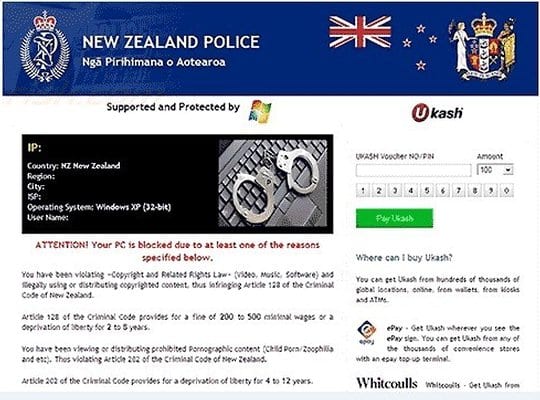
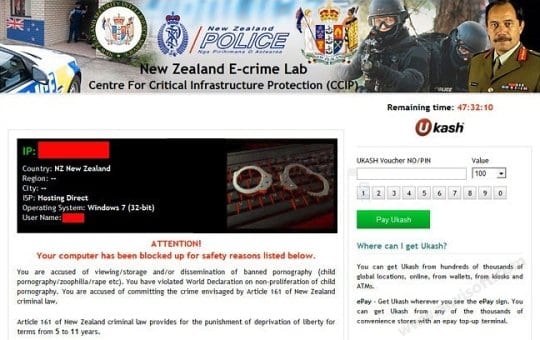
The cybercriminals have been moderately inventive in terms of this particular malware. The ransomware code appears to be the same in all cases, and the system lock screen has not undergone significant updates since campaign launch. Differing components are the graphics of the page’s header as well as the main warning text proper. In some instances the inscription is “Attention! Your PC is blocked due to at least one of the reasons specified below”, while in others it says: “Attention! Your computer has been blocked up for safety reasons listed below”. Basically, there’s nothing but a play on words that makes one scenario different from the other. To get a better idea of what this spooky thing looks like, see snapshots below:
Symptoms of the New Zealand Police infection
In addition to the above-mentioned inoperability of the contaminated PC due to the bogus police alert appearing immediately after system startup, the malware is known to also do the following:
- Determining the IP, OS, ISP and location of the victim’s PC: Within a dedicated field located in the left-hand section of the block page, the New Zealand Police virus displays user data that the ransomware obtained through the routine hard-coded into its functionality set. Providing such down-to-earth details is obviously intended to make the whole criminal plan appear as credible to the victim as possible.
- Disabling security software: The malware prevents any system processes associated with legit antivirus, antispyware, Internet security software, etc. installed on the targeted machine from getting executed.
New Zealand Police virus removal
Due to specificity of this infection, standard cleanup through the use of security software is barely applicable. Likewise, manual removal is considerably aggravated because of inability to access system directories where the virus embeds its components.
Thus, having thoroughly analyzed this malware, we came up with a number of removal methods that proved to be the most efficient for complete extermination of the New Zealand Police Ukash virus.
New Zealand Police ransomware cleanup using HitmanPro.Kickstart
For carrying out this removal procedure, you will need a USB drive to further launch the cleanup software from. Please note that all the data on this USB drive will be lost, so make sure you back it up before proceeding.
- Download HitmanPro software to a computer that is not affected by the virus and save it to your Desktop. Before performing the download, be sure to select the version according to the bit-type of your Windows operating system (32- or 64-bit).
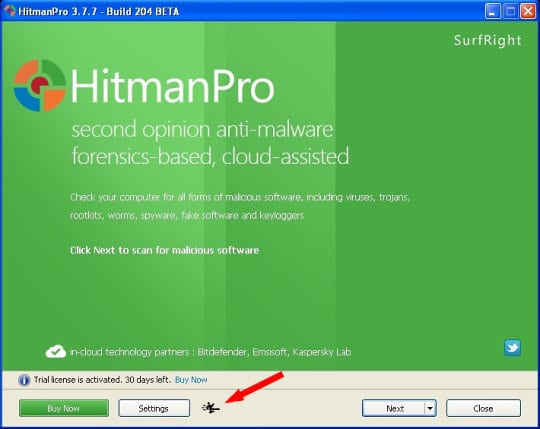
- Plug in the USB drive that you are going to use for installing HitmanPro.Kickstart. Having inserted the thumb drive, double-click on the HitmanPro icon on your Desktop. The program’s main Window will appear. Please click on the kicker button as indicated by the red arrow on the screenshot below.
-
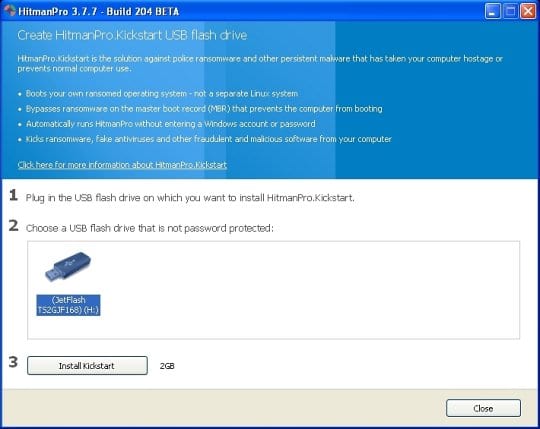
You will now see a window that will guide you all the way through creating the HitmanPro.Kickstart USB flash drive. Select the right USB drive by clicking on it in the corresponding field, and click the Install Kickstart button.
The software will ask you whether the USB drive contains any important files (all of them will be erased). If there are none, click Yes on the alert. This will automatically initiate the install process. When it completes, click Close button. - Remove the USB drive and insert it into the computer infected with the New Zealand Police virus.
-
When it is inserted, turn off the infested PC and switch it back on. As the computer is beginning launch, take a good look at the boot screen to find the key that should be pressed for accessing the Boot Menu or BIOS Setup. Please note that these keys may be different on different computer models. For entering the Boot Menu, those are mainly F10, F11, F12 or Esc buttons. The ones for BIOS Setup are usually Del or F2.
Having determined the appropriate key for Boot Menu access, reboot and start hitting that key repeatedly as the PC is beginning to load. When in the Boot Menu, use its prompts to select the drive you want to boot your computer from, i.e. USB drive. -
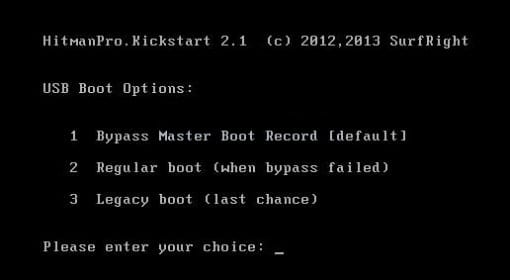
Now your PC will boot from the USB drive and load the HitmanPro.Kickstart saved to the memory stick. You will see a screen requesting you to choose USB Boot Options.
You should press 1 as your choice. Doing so will be followed by Windows starting to load. -
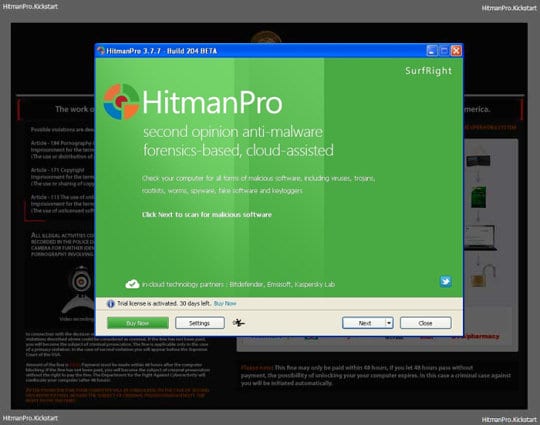
Right after Windows launches, the fake New Zealand Police block screen will appear as it did before, however in 15-20 seconds the HitmanPro main console will pop up on top of that.
Please click Next on the program’s GUI. -
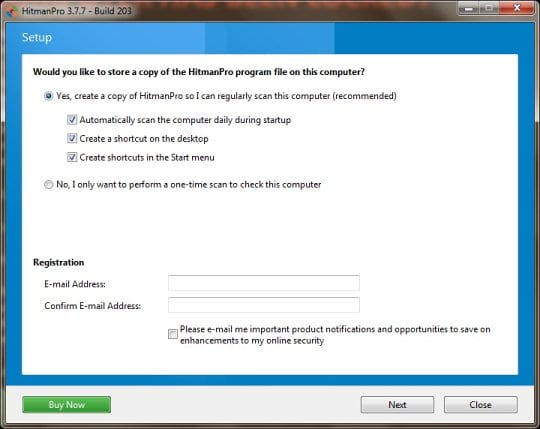
On HitmanPro’s setup screen that appears, we recommend leaving the default installation settings as shown on the following screenshot:
Please click Next.

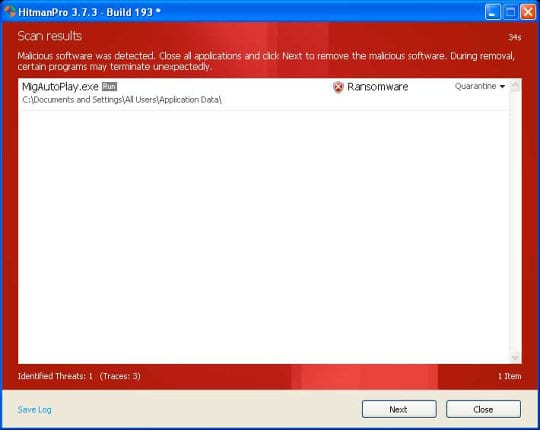
- SurfRight HitmanPro will now start a virus scan. Having completed the scan, the utility will come up with a report listing the detected threats.
- To get the spotted infections eliminated from your system, click Next. After the removal routine is complete, choose the Reboot option on the subsequent screen. Your computer will restart as usual. The New Zealand Police Ukash malware is no longer affecting your system. If you are not certain your current antivirus can prevent such infections from getting through in the future, you might want to consider upgrading to HitmanPro licensed version.
New Zealand Police virus removal via System Restore
This cleanup method allows restoring your operating system to the time period when it was not contaminated with the New Zealand Police ransomware. This procedure will not lead to loss of any files. To perform system restore, please stick to the following steps:
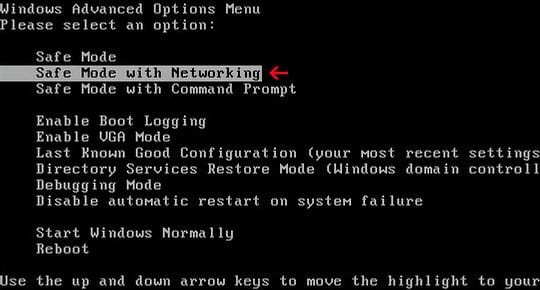
- When the infected computer is starting to load, tap F8 on your keyboard repeatedly to open up Windows Advanced Options Menu. When on this screen, use the arrow keys to highlight Safe Mode with Command Prompt, and hit Enter.
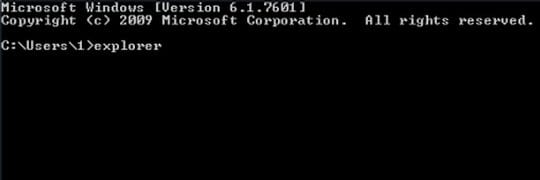
- Once the Command Prompt screen opens, type explorer and press Enter. Be advised this needs to be done quickly (within 2-3 seconds) or else the New Zealand Police bug will not allow you to type anymore and you will have to start the process over.
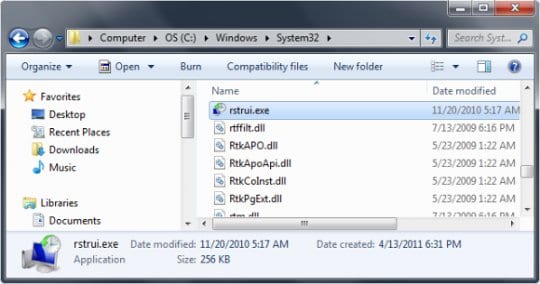
- In Windows Explorer, browse to the following path:
On Windows XP: C:\windows\system32\restore\rstrui.exe and hit Enter
On Windows Vista / 7: C:\windows\system32\rstrui.exe and hit Enter.
- Using the System Restore prompts, get your system restored to the date when it was unaffected by the ransomware virus.
Download, install and run reliable security software to get efficient protection from malicious software further on.