

Rafal M. Los, HP Software’s Chief Security Evangelist, and Shane MacDougall, principal partner at Tactical Intelligence, give a presentation at Black Hat Europe 2012 to show a non-standard perspective of threat modeling as an offensive tool.
Rafal M. Los: Hi! I’m Raf, that’s Shane right over here. We’re going to be talking about the topic called: Offensive Threat Modeling for Attackers. Is everybody familiar with threat modeling, for a start? Who has not done any threat modeling before?
Threat Modeling Primer

The short version of what we’re doing is this. We’re going to take the traditional approaches of threat modeling: the asset, the system, and the attacker, rather than looking at it from the defensive perspective, because that’s what we all do here, right? We’re defensive. So, rather than the good guys kind of looking back out at the bad guys, we’re going to flip this a little bit around and give you the bad guys’ perspective on the way in.
So, what is threat modeling? Just very quickly, we’re not going to take too much time on this. It’s the analysis which exposes possible threat factors. And we traditionally look at it as the system, the asset and the attacker perspective from a defensive purpose. It’s primarily used as a tool to develop countermeasures. People use threat modeling to figure out how their system is vulnerable so they can put a fix in place so it’s not vulnerable anymore.
The idea is to understand the attack and design compensating defense. It’s one of those: “How would somebody want to break this, given all its exposure, and what can we do about it to make sure those exposures don’t exist anymore?”

So, how this is actually essentially completely different is we turn the focus back on the defenders; we intend to understand defenses and defenders, because the idea behind being a bad guy – or let’s pretend we’re doing something less nefarious, like a pentester – but the reality is most folks that we talk to, in my line of work and in Shane’s as well, see security the following way: the main kind of threats are the ones you can write patterns against. We can catch hackers by putting an antivirus signature out or putting an IPS filter or some firewall rules. The reality is: that’s not the way they’re going to get you if they really want to get you. As they say, the determined attacker can’t be stopped. Everybody familiar with that?
This is the determined attacker, so we’re going to seek to develop an offensive strategy based on what we know about the good guys; so, completely opposite way around here. Also, it’s useful for pentesting and assessments, and this is how someone like an APT, to use that buzzword, will get you, right? This is how you will be attacked, essentially.
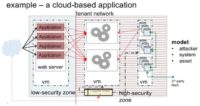
So, looking at this example up here (see image): this is our typical sort of web app out there, right? We model out where everything is: you’ve got low-security zones, high-security zones, a hypervisor, we’ve got some VMs, we’ve got some third-party feeds in there, and we can look at the attacker, the system and the asset, well, from an attacker perspective. We think that the attackers will probably go after that application side of things. Because that’s what you can see from the Internet, from the outside, unless you’re an insider threat and you get there from the other side, from the inside.
So, we can model the system by saying: “As a collective, where is this system vulnerable to attack?” We can also look at it from the asset perspective, and if you look at it from the asset perspective, if you want that data that is stored in that big red chunk on top in that database – how do we get to that? How is that best defended?
And so, looking at that perspective of things, we thought we’d go: “You know, that’s interesting; but where are the defenses weak?” Rather than looking at this and saying: “Where will the bad guys get us from?” – let’s look at it from the bad guys’ perspective and say: “Where are the defenses weak here? Where are they least likely to be fortified? And even if they have really good technical defense, where are they weak physically, where are they weak on the human side of things?” So, this is a holistic attack perspective.

And so, the perspective here is taking an approach as an attacker, learn how the defenders operate, where the defenses are fortified, where they have stacked themselves. Most networks are stacked really high at the perimeter, unfortunately. You guys must have heard the M&M comparison: you got a hard outer shell and soft, chewy middle? How many of you guys have met networks like that in the past year?
Most networks are still built around this perimeter idea, and they’re still built around the technology-based perimeter. So, the objective here is to exploit defenses or the defenders to attack the target. The whole idea here is to get in, to get what you need, and either establish a porthole permanently or get out without being detected. The idea is minimal risk to the attacker.

So, I thought we’d figure out how to express this from a very short perspective, and that’s: “Get into the defender’s head.” We’re going to exploit human behavior; we’re going to exploit defensive imperfections. You know how everybody says: the bad guy only has to be right once, and the defenders have to be right always. This is our advantage. We figure out the defender’s modus operandi: how they operate, when they are all at the bar, where the CEO lives, when his vacation is, when he is out of the office, so we can come in and be the new IT guy, that kind of stuff. We exploit the weaknesses in defenders and defenses. That’s kind of where we’re going.

So, how do we use weaknesses of defenders as a weapon? I found a really cool quote that I like to use a lot: “To lack intelligence is to be in the ring blindfolded.” And I think, from the white hat perspective, the folks that are defending corporate network are still relatively flying blind, because we’re well educated on how to put an IPS filter; we know what the attacks are going to be when we know what they’re going to be. When we know what to expect, we can prepare ourselves for it.

But, unfortunately, I think we’re sort of prepared for a very small subset of what we consider the determined attack, and the threat landscape, I think, is fundamentally changing. And so, what you’re getting is this gather-modeling-plan idea (see image).
Step 1 is to gather some intelligence, whether it’s passive or active. It’s an intelligence gathering exercise that prepares you, essentially, for the battle, I won’t say cyber battle. So, step 2, modeling the intelligence that you have, it’s kind of outside the scope of this, but if you’ve ever gotten a giant whiteboard and just started writing everything that you know about the system during, like, a pentest, you find an IP address and you figure out what’s at that IP address. If you got what’s that connected to and what’s on that system, and then who runs that system, and what they do, what their role is, and where their kids go to school, and who they vacationed with, all of a sudden you go: “You know, that’s interesting, I could probably do this, this and this to get all that data without having to actually lift a finger.”
This is kind of one of those perspectives, if you’ve ever heard of this in the news, and it’s happened pretty often, unfortunately. I think there is a movie called “Firewall”, a really bad movie. If all these awesome technical defenses are in place, impermeable firewall defenses and all these other kinds of stuff, what does a bad guy do? Shows up at the kid’s school, picks up the kid, calls the guy, the head of security, and says: “Hi, I’m the guy you’re going to give everything in your databases to,” and the guy says: “No, I’m not,” and he goes: “Say Hi to your kid for me.” Are you prepared for that? In most cases, most of the IT and most of the corporations out there have no idea what to do in a situation like that. Crisis management turns into, like, a circus. So, this is the plan part. We’re going to plan what we’re doing.

So, this is really about knowing the adversary, mapping out the attack surface, and it’s mapping out the digital attack surface, sort of the fingerprint of the network, the applications, the systems, where they get their data feeds from, whether they have people on iPads and mobile devices that also go to the same gym you do? Can you hang out with them on the train and exploit the fact that their wireless is always open or they’re using a portable hotspot you can get on and pull all your data from those kinds of things?
And then, profiling the defenses, really, is a look at how their defenses are built. Too many times in the past we’ve seen somebody that wants to get some asset, whether it’s a database or personally identifiable information, credit card data, whatever. It’s that spray and pray mentality, so the attack is trying to exploit the app and hopefully not get caught. This is not what we’re starting to see, this is not the kind of attacker that is going to be prevalent in the future. When we have good defenses, you’re not going to get to spray and pray types; the SQL injection eventually will run out. I keep saying that, maybe one day it will be true. I guess it’s still wishful thinking.

Gaining an advantage is about getting the upper-hand here. So, when we hit the attackers directly we’re going to actually hit them as they know it or as they don’t. We may just exploit them directly, go walk up to them and say: “Hey, I know this and this about you, but don’t panic, I don’t want to kill you, I just want some data from you.”
We can attack them without them knowing, and I’ll explain that in a little bit. And we can attack the target using the information about the defender. How do we get to a target, a hard target behind a well fortified system? Well, there have been at least 4 news articles in the past several years, where really well-designed defenses that go down for, like, 30 seconds a year, were exploited. You think that happened by accident? Probably not. If I know that the security infrastructure at ACME Widget Company is going to undergo a major upgrade or overhaul, because I know which vendor they use and I’ve talked to their vendor and I got them to tell me some information, I probably have a great way to get in, get out, and not get caught.

So, if we’re looking at attacking the defenders directly, this is hitting the defender, the asset, using the weakness that they have against them. It’s more of a bold attack, it’s kind of in-your-face, “we’re going to come right at you,” sometimes it works. The idea is this requires a lot of advanced intelligence on the asset.
You need to really, really be prepared, because it’s really hard to walk up to a person if you don’t know everything about them, and basically attack them. I don’t mean physically attack them, but I mean just telling them: “Hey, I’m going to come after you.” Because humans can be rather unpredictable, unless you understand them well. So, this requires some prep time, a lot of preparation; the likelihood of the success of this kind of attack is very heavily dependent on the asset, and at this point I just say you forsake the element of stealth. You’re just going to give up the whole stealth idea; you’re coming full frontal at this point.
You’re likely to burn the asset – you guys know what that means? They’re not going to be your friend anymore. The odds of them getting fired or somehow otherwise compromised are pretty high if you come at them straight on. But this is generally a short-lived attack: if you know you want something from a company, you are a state sponsored attacker, and you know that, I’m using a general example, but if you’ve already read this in the papers, please don’t tell anybody else, I don’t want to be referred to directly.
Say, you want to steal a design of a jet turbine for the next big tactical air fighter, and you need to get that design information, because the nation state that you are chartered by tells you to go get it, whatever the cost. Well, something like this is probably the fastest way to do it. This is the quick and easy, or rather quick and dirty, I’d say. You gather all the intelligence on somebody that’s likely able to be turning inside that company; you go right at them, get to them directly, personally, get them to give up information, and then bolt. Odds are you’ll probably never want to run into them again: they may be likely to lose their job. You could probably ruin somebody’s life pretty quickly this way, but it is a short-term attack.

So, attacking the defenders indirectly is exploiting the defender without their knowledge, and it basically assumes that the asset has access to the attack target, requires some prep time. This does hinge on you being stealth, so this is where, if you know somebody’s got the VP of engineering and has access to the engineering department, all the blueprints and stuff from their home because they have a permanent VPN from their house, and you know that they have a kid who plays the Xbox a lot, and the Xbox happens to use that same network – you can put 2 and 2 together, you can probably get in by not even having to ever talk to that VP. You know, you can make friends with their kid online playing whatever videogames people play online these days; send them a file, exploit either their kid’s laptop or something, or their system. Connect over, get all the data you want, write the network in, pull it out, and leave. Or you can leave something behind for yourself if you ever need to get back in there; but it’s nice and stealth.

Attacking the target itself is less of a human-based attack, but it’s learning the weaknesses of defenders and defenses they have to plan the most strategic attack against the target. How many times have you guys looked through an IDS log or attack logs, and realized that somebody’s trying to run Oracle attacks against your SQL server, or there’s 10,000 requests a minute? So, we’re basically exploiting the weaknesses of a target.
When you’re looking at a system, you have to know what’s behind it, you have to know what the infrastructure is, so if you’ve got an Oracle server, you’ve got an Apache server, you’re not going to spend lots and lots of time throwing 0-day IIS attacks at it, this just doesn’t make a whole lot of sense. So, we’re going to talk about the 5 P’s of this.

The first one, really, is the purpose, it’s kind of like the silent P. And what we’re really looking at is what the purpose of the attack is. This sounds like a foregone conclusion at some points, but it’s really not. We need to figure out what you are trying to get to, what your purpose is. Are you trying to infiltrate the network? Are you just trying to gain a foothold? Are you trying to fully compromise an asset, a specific machine? Are you going after a particular target, a particular data point? What are you going after? And you have to keep that in mind, put it on a post-it note at some place, in the center of your whiteboard, so you know what exactly it is that you’re going after. Make sure you don’t stray too far from that path.

The first real P is pinpoint. You’ve got to create a high payoff target list; you’ve got to know what your targets are, the ones that are going to be the easiest to get a lot of value from. So, these are the assets that give what we’ll call the biggest bang for the buck. Assets in here include things like security personnel, senior executives, the IT staff etc. A while back, if any of you followed our SecBiz conversation on LinkedIn or on Twitter, we basically talked about whether security people follow their own policies. And the overwhelming, sort of scary response was: “No, because we know better”.
So, how many security people’s laptops out there are probably not running the corporate image, and running kind of custom software? Think about this for a second. How many DBAs think they know better? When asked these questions, a lot of people are smiling and nodding, that kind of worries me. So, looking at things like secondary targets, and how we are going to get into using an indirect attack vector: is there a web server out there some place that somebody forgot about that still has backchannel access into their main corporate network?
When people do asset defenses, in corporate IT you have a finite amount of resources, and you have to figure out what you’re going to defend. And generally people draw a nice little line around where dollar signs are, where your data is, they’re going to put a line of defenses around there. But because there’s a box out here that runs marketing or runs something that’s not exactly super important, but it does have a connection back to the network – those are really the least protected pieces. When we draw this map out, we threat-model this out, we can pinpoint the boxes they attack, because that’s the weakest point, and get our way in that direction. Pentesters do this all the time.
There’s also this list of opportunity, we call this a low-hanging fruit: the people that are still on Myspace from the company, those that are easily able to be friended, that accept everybody’s request on Facebook, that kind of stuff. And so, mapping out defensive capabilities is important because you’ve got to know where they’re going to be ready for you, to carefully avoid those or to overwhelm them, as we’ll go through further.

Points of attack refers to decomposing the assets into the absolute, most basic components. So, when you look at the perimeter, what’s at that perimeter? It’s not trivial to decide that there is a firewall with an IPS behind it, a set of proxies and load balancers, and then the actual set of web servers.
I’ve watched attacks – in fact, I was on the defensive end of this, and it was kind of funny to watch – we had a vulnerable Apache server that hadn’t been patched, I swear, for around five years. And the only saving grace for us against this one attacker, who is actually really crafty, is the fact that he couldn’t seem to grasp the fact that we had a load balancer in front of this, in five of these boxes on the back end. So he kept sending multipart attacks, where he’d send a part of the attack, wait a bit and assume he gets the same box again, but the way the load balancers were set up was they would give him different machine each time. So half of this attack went here, half of it went here, eventually he finally popped one of them, but fortunately he couldn’t figure out how to get back to it. So, this is one of those situations where you have to know what you’re going after, otherwise you become the subject of somebody’s slides a couple of years later.
So, breaking down the physical and human assets. The physical assets, I think, are a lot easier: technology is more predictable than humans. If you picked anybody in this room right now and said: “I have a gun to your spouse’s head, I need all your information, I need everything you can possibly give about your company; I know it will cost you your job, but I really don’t care,” people react in different ways: some people might try to fight back, others might just give you everything they have and hope that you leave them alone. But you have to know what you’re going after and you have to know how people are going to respond. And this is, again, also not trivial.
You can look at things like family affiliations: what kind of hobbies they have; look at behavior on psychological profiling; sentiment analysis is always interesting if they’re on Twitter and Facebook. Port scans, vulnerability inventory, system maps, application analysis: these kinds of things that help us pinpoint exactly where to hit.

I hope you guys get the irony of hanging a piece of Swiss cheese in the Posture slide (see image). Identifying asset’s defensive posture: how well are they fortified and where? Just because they have a lot of defenses doesn’t mean they’re well fortified. Just because you have a lot of cool technical stuff in front of something, doesn’t mean any of it is working properly or that anybody’s going to watch the big flashing red light that says: “Hey, we’re under attack, help!”
A lot of these are critical and time-based components to this. Technical schedules: when are firewalls rebooted? When are systems rebooted? When are things down for maintenance? When does the data center have its next major mechanical repair time? When are they going to switch over to their next Internet provider? When can you get in under the guise of something else happening? Odds are if there’s an elevator that’s out in the building, you can pretty much get to any floor by saying: “Hey, I’m the elevator repair guy, look, that’s what it says on my shirt, trust me,” and people will let you in. “There is HVAC problem in your server room, I swear, look, it says Johnson&Johnson HVAC, I need to get in.” Sometimes people will let you in.
Does the enterprise understand security? Well, unfortunately, often the answer is No, but is there a proactive security posture or is it simply reactive? Does the company or the asset you’re trying to gain access to react to the way they get attacked, or they try to figure out what’s coming next? Very few organizations have a proactive security posture. They look at what happened in the news yesterday and they go: “Oh crap, we need to defend against that too.” This is, unfortunately, how a lot of our air safety is done.
Is incident response implemented? This is a really good thing to know, because odds are you’re going to run into incident response at some point: you’re going to do something that will trigger the defensive mechanism to get spring to life. You’re going to trip a firewall at some place, you’re going to trip an IPS, you’re going to blue-screen the machine somewhere, and they’re going to go: “Something’s up.” How do they respond?
If they have outsourced their frontline incident paneling, which means all their IDS and IPS and firewalls go to some outsource company, odds are they’re not going to be very responsive. What that probably means to me is either a) they’re overwhelmed; or b) they don’t have the in-house expertise to do it themselves. That’s an interesting place to start from because odds are, between the time you launch the attack and the time their call comes in to the client and they actually do something about it, there’s a window of opportunity there.

So, Pwn is execute the attack, go after it, go do it, compromise multiple assets using varied attacks. This is an interesting way of getting at multiple assets: you want to make sure that you get more than one, because sometimes the good guys will find it, they’ll defuse the bomb, whatever attack you’re throwing at them. There’s logical attacks here – attack the logic of processes or applications. Hacking doesn’t just involve sending 0-day. Being able to exploit processes within technology or people is also very, very important.
Social engineering is a huge part of this: if you’ve ever watched anybody work a social engineering angle, it’s scary and terrifying how effective this stuff is. Leverage known weaknesses to compromise assets – again, stealth is extremely key when executing here. You don’t want to make a lot of noise, unless you do want to make a lot of noise.
There are times where it’s ok to create a lot of noise, sort of wake them up, get them going: “Look over there, lots of stuff going on,” as you pick the pocket from behind, makes sense? This is a tactic that’s used on busy streets, like in Times Square and downtown here a lot, when somebody wants to pick your pocket they’ll bump into you on this side while they reach out for your wallet on the back end because you’re focused on something else, the other immediate impact.
Don’t forget the whole bribery, blackmail and simple incentives. How many people have been polled to give out their password for a candy bar? A staggering amount! Kind of worries you.

The last one is Poll. I use Poll here because it’s about continuously monitoring the things that you have attacked, compromised and successfully infiltrated. The idea here most of the time is to establish a long-term foothold, so if you’re going to get into a box and you want to get the data they have today, but odds are they’re going to get more data tomorrow and you want that too – keep at those assets that you have in there and established. We do a lot of this with BeEF, browser exploitation framework. It’s not just popping that browser and getting some data, it’s also being able to establish a longer-term foothold. Metasploit is really good for this.
Perform damage assessment on lost assets: when you have an asset that you’ve established inside of an organization and somebody figures it out and they go: “Hey, holy crap, my laptop’s compromised, I should reimage,” – well, you’ve lost that asset and you have to compensate, come up with something else. Odds are you don’t want to exploit another asset the exact same way, because then you develop a pattern, and they can figure patterns out.
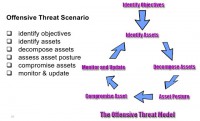
So, the threat scenario here is kind of like a little diagram of how to work through this (see image): Identify the asset, decompose, get the asset posture, compromise, monitor and update, rinse and repeat. And with that, I’m turning it over to my partner.

Shane MacDougall: Now we’re going to get into the meat of the matter of how we’re actually going to break this down. So, modeling the defender (see image): assessing the people component, like I said, this is broken record type stuff. But we assess the footprint of the organization structure and their defensive talent. I mean, it’s really important that we identify who is doing what within the organization.
We scan the corporate website, press releases, conference presentations. Conference presentations are fantastic: it’s amazing how many people actually put out stuff that is considered company sensitive at conferences, because for some reason they think: “Well, it’s not going to leave this room of the conference,” as if they’d never heard of the Internet, or email. But we’ve seen that happen many, many times.
Identify secondary attack factors, such as suppliers, vendors and customers; again, can’t say enough about attacking vendors, it’s one of my favorite attack vectors, and it just works over and over. Dialing through voicemail and phone directories: I’m always amazed at how few people do an exhaustive poll of company phone directories; you call up and get dialed by name or dialed by department. But think what some of the information is that you get when you dial these services. You often get people to answer usually with their position and their name, and that’s information that you definitely need to know, because we’re trying to map out who the actors are. But often you will hear them say: “I’m out of the office from this date to this date, if you need me you can get me on my cell at this number, and if it’s really urgent, you can contact this person.”
All of that is actual intelligence that you can use for a social engineering attack or just establish your window of attack, because as Raf said, time is really essential on a ton of these attacks, so we really want to extract as much information as we can. Always be sure to traverse the entire phone directory. It’s amazing how many people kind of ignore that.
But suppliers and vendors and customers – I mean, a frazzled customer line always works. A perfect line also is: “I’m such and such from the target company and I’m replacing the guy that’s really your point of contact.” It doesn’t hurt to throw a little bit of sales pitch in there: “We’re interested in buying more stuff,” and the fall for it. I mean, it’s scary how few people pass and take that idea of security for the other person. Everyone’s secure about themselves, but they don’t really stop and think about securing the other people you might be attacking. That’s kind of frightening.

So, when you go through social media, it’s really important that you mine the living daylights of it. I mean, everyone goes to Twitter, Facebook and LinkedIn, and they’re all goldmines for sure. But look at some of the more esoteric sides as well, like Flickr and SmugMug; it’s crazy what amount of information you can get: ID cards, badges, employee names, numbers, building layouts, etc. (see image to the right). People just like to put stuff on the web.
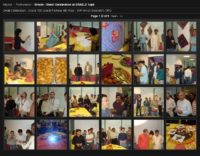
Here’s an example: this was Oracle Corporation, one of their employees put a whole bunch of events online, but this one kind of grabbed my eye because it was about the Diwali celebration (see left-hand image). If you look at that link, you will see that she says the address, including the floor number, the SVP, his name, his org group that’s working there, and she took all these pictures with a DSLR.
And thank god to Canon, because these high-res pictures are fantastic. So you can basically zoom in and find people’s ID badges on their hips, you can zoom in, you can grab their name, grab the barcode, you can grab the whole layout of the cards. You can essentially make a fake card that you can tailgate into the facilities with. And, of course, tons of information that you can use: the pretexting, talk about the delicious Gulab Jamun that they took several pictures of, must have been fantastic.
They also allow us to get fantastic information that we can use as a social engineer: the names on the badges were nice to know, but even more nice was once we took these names and ran them through several different social networking sites, we saw that two of the guys on their social media profiles said that they’re currently open to job offers. So, those are the two guys we are going to go after, right?
It’s really not hard to pull ID badges off. This was SmugMug, the first two pages I pulled off – several pretty badges that are pretty nice: the Google one, the Apple one was nice. The Google Guest one, as you can see, got the time sensitive thing; the Encom one – there were actually several of these, some people masked theirs out, but you were able to get enough so that you could, seriously, very easily reconstruct an entire badge with these guys. So, you know, people just don’t think before they go to social media for whatever reason, it’s kind of scary.
Doing the social media mining, we can cultivate tons of background information: phone numbers, email addresses, you name it. Sites like beenverified.com; I love spokeo.com, emailfinder.com and many others – you can really get a ton of verifiable information. Never go on one of these sites, so grab several of them and confirm, especially if these guys are doing email verification and kind of data mining or data providing, I guess. It really helps to go through several of them, because you’ll see there’s a lot of junk in the cloud.

Another thing that we want to do is we want to really identify the organizational hierarchy of a company. By that I don’t just mean hierarchy as who’s got what title, but who the influencers are. Because within every group you’re going to have the people that really drive decision making, and even if they don’t have a title, they are usually the people you really want to target.
And it’s kind of hard to do sometimes if you don’t have the org chart, or of it’s one of a few companies that doesn’t let their people post on LinkedIn. But Eric Gilbert at Georgia Institute of Technology has really developed some interesting stuff. He basically developed all these phrases in electronic messaging that will have a very high correlation to a person’s social status within a company. It’s very interesting, I really suggest you check it out. He basically created a data set of 7200+ phrases that will give you a really good, accurate idea of that person’s social status within a company. So, if the email has: “Thought you would,” it means that the recipient outranks the sender. But “Let’s discuss,” – you know, the famous words you always hear in a company; if you see that in an email, the guy sending that is the big cheese.

As we have said before, the high payoff target list, HPTL – that’s really what we want to focus on, to begin with. The tangential target list, TTL, is our secondary targets. They still have the potential for access, they might not be your IT guys or infosec guys, but if you compromise them you’re at least going to get some proprietary information or access that could be logical or physical to a facility.
And then there’s the targets of opportunity, or ToL, because it’s a low-hanging fruit. These are mainly for throwaway operations, one-time phishing attacks, that sort of thing. Whenever I do a social engineering attack, I always make sure I have one good persistent connection, and then I’ll develop a bunch of ToLs, and those are the ones that I use for the one-time phishing attacks or the one time social engineering attacks: “Do this password change,” and they change it; because I don’t want to impact my one guy that’s going to be my persistent connection.

We also do the reconnaissance, you know, identifying, fingerprinting systems and applications to find vulnerable assets. This is the standard fare for most pentesters. Doing active reconnaissance is the same thing: Nmap, that sort of thing.
Physical asset assessment is something that a lot of people kind of fall down on. That’s where you actually perform the physical surveillance of your facilities, and I’m always kind of amazed at how many guys that do pentest never actually set foot on-site. They always do it entirely remotely. And that just misses so much of the company.
Physical surveillance, having a physical presence is absolutely essential to identifying the company’s overall security posture, and if your pentest doesn’t have that in it, it’s not a useful pentest. Obviously, lacking physical security is probably an indicator of lacking overall security; not always the case, but usually. It lets you identify things such as closed-circuit TV, whether the cameras do PTZ or they’re fixed. Even just hanging around in the lobby, grab titles of the magazines that are sitting in the lobby, where you look at the label and it has person’s name, their position and often home address or work address. Just sitting in the lobby will help you pick up things like that.
The welcome boards – almost every company has a welcome board in the lobby; if you’ve seen those, they would say: “Welcome, here’s the chump of the day that’s visiting us,” – that gives me points of data right there. And even a sign-in book – it shocks me how many companies still have basically just a clipboard that has you sign in your name, the person you’re visiting, the company you’re with and the time you’re on-site. For your competitor that’s just a goldmine, because it tells me everything. If you’ve got a guy who’s coming in from IBM tech support, you probably have IBM hardware within your facility. But it also lets you map out vendors, customers, that sort of thing.

To model the points of attack, obviously, our key objective is to break everything down into the tiniest pieces possible. If you’re familiar with the STRIDE threat model, this is a lot of what they do, too. You break everything down into the tiniest possible granules that you can, and then you break those granules down. Basically, we are looking for what part of this component can be broken down; and if it can’t be broken down, what needs to be done to break it down.
Same kind of thing we do with the human assets: we break them down into family members, friends, roommates; where they go, if they have a shared home network, whether they commonly visit public network sites. Indirect targeting of asset via targeted spear phishing, piggyback hacking; even going to the house and breaking in – dumpster diving is the most effective at their homes, not at the office. They have basic shredders, if they have a shredder at all. How many people actually do the dumpster diving at their target’s home? Not too many, because that’s not usually in the rules of engagement for your pentest. And, obviously, target via social engineering to elicit information.

So, we want to model and identify the human behavior, and this is very important, because these are the people we want to identify, who we attack. We should look at their personal activities, their hobbies, routines, favorite hangouts, religious preferences – all this stuff is very useful in helping to develop pretexts for social engineering attacks, and also allows us to track individuals physically.
How many people here use Foursquare? I see lots of guys on my Twitter feed that use Foursquare and it shocks me, because you’re giving real-time pretexting information to an attacker: “Hey, I’m here and this is a place I go to all the time.” And it’s kind of shocking how many big companies have sensitive sites that somebody has made as a check-in point. I mean, it’s really frightening.
Now, negative behaviors are my favorite part. This is kind of the chewy chocolate goodness part. If you can identify behavioral issues, such us substance abuse, gambling, extramarital affairs, etc., that opens up the target to a possibility of blackmail or extortion. It sometimes requires more digging, because there are a lot of protections out there, but some sites are easily exploited.
For instance, prostitution sites are fantastic if you’ll ever try to find a person that’s easily attacked. And the reason for that is, usually, in most countries, not all of them, prostitution is illegal, so you have these websites that are set up; the girls or the providers that can be guys, obviously they don’t want to be providing their real names, etc., and they’re kind of the commodity that the website is selling, so they usually get on these sites for free. It’s very easy to create a prostitute profile on these sites.
On the other hand, if you want to be a customer and you’re paying for access to these girls, you’re verified, because that’s part of the allure to the providers coming to this site, so they can kind of make a creep list. Therefore you really need to use legitimate credit cards and verifiable data, and the girls or guys have access to that data. So, it’s very easy to mine that data and do cross-referencing via social networking to find potential victims.
If they don’t go to one of these sites, obviously it takes more digging, but you’ll be amazed at how many times this comes up. And also, if you want to, try to remember the name of the guy who did the Internet trolling. Do you guys remember that when he put out the horrible, horrible ads? Some guy put out this ad for a very odd kind of sexual activity and he got tons and tons of people flooding him with emails saying: “I am very interested in hooking up,” and then he posted all the private information online, but it was shocking how many people were responding from, like, Microsoft.com or Boeing.com or whatever, obviously not understanding how the corporate email works. I’m sure that violates some sort of HR model.

Modeling the points of attack is obviously about psychology and privacy as well. Psychological profiling from social networking is a growing field: Tweetpsych.com, there’s a bunch of other tools out there; to be honest, not a fan yet, I think automated profiling is just not there yet. However, you can still do it manually.
If you look at some of the stuff that the Online Privacy Foundation has done, they’ve started to say that there are some correlations, but they’re not as strong as previously believed. The best way to do a psychological profile from social media is basically look at the profile and see what they do, who they hang out with, their political beliefs. If you can’t really get anything from them, look at who they hang out with, because usually that can build some information about them.

I’ll give you an example, but there’s a downfall to this type. If you’re looking at people on Twitter and they’ve got a Guy Fawkes mask, they follow command and control accounts from Anonymous, you can probably profile them as a follower of Anonymous with fairly strong likelihood. They’re probably going to be more open to be susceptible to be recruited into a hacktivist operation than most other people.
But, that said, I’ve seen a lot of junkie data mining that goes out there, and basically they say: “If you’ve got a Guy Fawkes mask, you’re an actor, you’re a guy that we need to monitor,” and that’s not necessarily the case. You can’t just go by an avatar and say: “Well, he’s a baddie.” So, do some due diligence, but if you see enough connections.
Rafal M. Los: Just to throw one thing into that, one of the things that are sitting on certain agency briefs and security organizations briefs about the whole Anonymous thing: companies are so paranoid about who is or who isn’t within their walls one of the Anons that this is becoming a very real threat. You can actually very easily recruit somebody to do something pretty bad within a company simply by purporting to be somebody in command or in power structure of a hacktivist group like this. Now, with the recent arrests, I’m sure that becomes a little bit harder, but there’re still lots of young impressionable minds out there; just something to keep in mind.

Shane MacDougall: A big tool in determining your targets within a company is company sentiment. You really want to identify as many users at risk of being compromised within a company as you can. You should use negative employee morale to stage attacks, so basically we go through the different sites like glassdoor.com, insidebuzz.com, jobitorial.com – fantastic sites, to gauge sentiment within a company.
You’ll be shocked at how many people give up the goods on companies in these forums, where they believe they’re anonymous. Obviously you can identify any negative widespread sentiment against the employer on these forums, they don’t hide it. And obviously you can peg users with social media profiles that are very liberal as being a low-hanging fruit.
All these guys identify their posture for attack as very easy to do. We can use social media to gather company lingos, like off-site data center slang, I mean, they usually have nicknames for sites, that sort of thing; all very valuable for social engineering attacks. You can run sentiment analysis on data sets that you get from targets. I prefer manual analysis to automation; I’ll show you why.
Here are some examples from the tools that I use. The sentence that you grabbed from an email is: “I really can’t wait to quit this job, I’m seriously fed up with the bs in this company, and will jump ship the first chance I get.” And the automated tools said that this was positive.
The next example was: “I’m going to burn this company to the ground,” which was also flagged as neutral, a positive score of 0.65. And then the final example was: “Good god, I’m not fond of this f…ing place, if I don’t get a go…ed raise, I’m going to gun down every manager I see,” and it still came out as a neutral.

Like I said, you really have to do manual assessment. We have a list of words that are used to go through, I mean, you have to manually do it, the tools are just not in their prime time. This one was ToneCheck, there is actually another piece of software that’s done by Stanford, it’s called Muse, it’s quite a bit better. It lets you go through chat logs and everything rather than just email. But people say: “Well, if you got their email you’re already in the company, what’s the big deal?”
Remember, we don’t know whose email we have, we’re trying to identify people within the company that we can exploit and target, whose posture is ripe for exploitation. And remember, we want to create as many diverse entrance points at this company as possible, we’re not just looking for one point in. The goal of an APT is not simply to get root. This is important. Your target is to create as many different vectors of persistent attack as possible.

Let’s continue on modeling the asset’s posture: planning time-based physical attacks, as we said many times, is very important. We got physical plant, social engineering, which basically rely on the target not being around, while time-based attacks rely on knowing schedules. So, if you’re going to a conference, that’s going to be a good place we can either gain access to the physical machine, employ a honey trap, social engineering, etc. And if they’ve indicated on their profile that they’re open looking for new positions, that’s perfect: we approach them as a recruiter, and we pick their brains on some of the work they’re doing and a little bit of misdirection – who knows what we can get them to click on.
We’ve noticed if the target is a speaker, that really helps you identify, when and where they’re going to be, and gives you different avenues for connecting to the speaker.

Maintenance windows, again, are perfect times for low-risk access, can be gleaned either from social engineering or monitoring behavior. Identifying a window is the difference between success and failure in so many of these attacks. New systems being delivered – perfect; construction projects at corporate facilities, a lot of chaos in companies – those sort of activities. Mass hirings or layoffs exploit human confusion: when companies do mass layoffs, there are a lot of people that are ticked off and they are ripe for the picking.

And then we obviously get to our Pwn, this is where we target our asset list; we send trojaned AV, software branded as if it were coming from an organization. We mail branded USB thumb drives as tokens of appreciation from the company. We attack an employee’s home network, especially if the user is utilizing wireless networking. We even do physical break-ins into employee’s house in order to install malware, keyloggers, etc., we can just clone drives. Like I said before, dumpster diving at the employee home is usually more effective than at the corporate site.
If we know the IT team from our target will be out at the bar somewhere, that’s where we ingratiate ourselves: we start buying rounds, and by the closing time we’re also around and we’ve got them appropriately lubricated.
Rafal M. Los: Anybody ever have a vendor buy them a few drinks at a conference or anything? You tend to start telling people more than you ordinarily would. Before you know it, you’ve sort of given out too much. It’s happened.
Shane MacDougall: It happens all the time, and there’s actually a mayor in the States that just signed a multi-million dollar contract, and it came out after the fact that they just took him out and got him hammered, and then he signed this multi-million dollar contact. It happens all the time, and nobody does it to me, unfortunately. I am open for drinks if you want to come buy me some.
Obviously, you should utilize social media to track down the assets, engage them directly where they’re weakest: bars, clubs, wherever their guard is down. Use Foursquare, my favorite; use Facebook, Twitter, all these real-time data points are fantastic for the attacker. Exploit and incapacitate them so they can’t respond to incident, and exploit the items on that asset’s person: if they have a smartphone, a laptop, access badge – grab it and exploit it.

So, now we want to directly engage the defenses. A very effective thing is false flag operations. Does everybody knows what a false flag is? False flag operations are basically where you do something and it looks like somebody else did it. We execute multiple attacks to heighten the sense of danger, and we force the defenders to tune down their defensive posture because they’re getting hit from several different areas. We trick the defenders into questioning their defensive posture.
Opportunistically attack systems or physical assets: you know, we can do it during change windows, upgrade periods, off-hours, when defenses are the weakest, when defenders are incapacitated as we got them drunk or they are otherwise unable to defend. We exploit information overload or misdirection: noisy attacks against front-end systems while the back-end is quietly exploited are a good way to go. Create confusion and misdirection with overload of systems from high-noise or fake attacks. Exploit human mental frustration or fatigue.
For instance, a false flag attack: you can basically leave fake trails, fake bits that lead back to somebody within a company; attribute an attack to someone who’s within their own IT group – not enough to get them fired, but enough to get them questioned. And all of a sudden this guy is now isolated within the IT group and within the security group. And he’s going to get pissed off, because nobody trusts him, because there’s that reasonable doubt that’s been gained, that’s being raised. So, now he’s someone you can probably flip, and this has happened a few times.

We identify defenders with negative behavioral patterns: an employee that fears their employer would fire them if they knew, that sort of thing. It’s a very dangerous avenue, it should be last resort, because you don’t know if it’s going to blow up in your face. Involving employees at the risk of being extorted or blackmailed – the vector often involves luck; like I said, you can target using some of those websites, the prostitution websites, the drug websites.
A lot of drug websites operate exactly the same way as prostitution websites: being a vendor versus being a customer. Some of them you need to pay down but, again, a burner credit card is more than acceptable to these guys. By utilizing websites specializing in illegal activities or alternative lifestyles you can really identify these guys. It’s highly illegal and really can blow up in your face. And attacks like this really require long times, long periods of planning, observation of the defenders, and sometimes deep pockets. This is something that nation states really work on.

Again, exploiting employee’s sentiment: disgruntled employees are really easy to find; they don’t hide themselves, they post everywhere. Happy employees are often eager to help their employer or you, so if you are acting as an agent of the employer, they’ll certainly help you.
Social media makes it simple to find corporate employees and learn their sentiment: lots of websites to troll and find unhappy employees, like I said before. And these guys are easily manipulated into revenge.

And again, exploiting misdirection: creating a situation of over-stimulation, confusion – we want to attack quietly when no one’s looking while making noise on the other side. So, DDoS forces the adversary to tune down. If you’re launching several different noisy attacks on one side, and your real goal is to get the silent attacks on the other side – that’s a way to go. The thing is most organizations cannot find one deadly needle in a stack of needles. So, if you overwhelm them, human fatigue sets in quickly and the defenders give up.

And then the final stage, of course, is poll: we just keep monitoring and updating the asset list. Monitoring the compromised assets that we have is critical. I mean, you need to know what’s happening with those things. Has the asset changed? Has a compromised asset been fixed? If so, can it be re-compromised? If an asset is lost, we want to perform a basic damage assessment to ensure that no information leakage has occurred. In this context, we want to know whether a security bulletin was sent out, whether this was fixed as part of a routine remediation effort, or it was part of another process. That’s important.
You want to identify any possible replacement assets that will replace the compromised asset’s function in the attack. Then you want to perform what’s called an asset effectiveness assessment, and that basically tells you what assets are performing the best. You want to identify the risk to the asset that could lead to the asset being compromised. And if it’s critical, then you want to re-rank the effectiveness in a quantifiable manner, as applicable to the project.
So, you basically identify any underperforming or non-performing assets and decide: “Does the asset have any chance of coming around? Can we flip it into a good asset? If so, what is it going to take cost-wise and effort-wise?” Do a cost-benefit analysis and determine whether or not you should just cut the asset loose or just keep it on the line. I never really recommend cutting an asset loose unless it’s been compromised, because you never know down the road when it might come back in.
Finally, you want to identify what postures have changed of a previously non-compromised asset, because what you often find is assets that weren’t compromised are now actually compromisable. This happens frequently with employees, especially when the company is right size. The larger your team’s resources are, obviously the more assets you can manage, so deep pockets will determine the effectiveness of your attack.

Online resources: we have a list of recommended OSINT aggregators and information gathering tools, also a list of sentiment analysis keywords (see image). These are the ones that I use rather than using the automated tools because, quite frankly, they suck. And ToneCheck, I mean if you really want to play with it, just to see how god-awful it is – feel free, but Muse from Stanford is the tool that I really prefer, it allows you to do chat, mbox email formats, mailing lists, and it’s got a much higher frequency rate than the Lybmix ToneCheck. Like I said, you still want to do it manually because manually you will see a lot of stuff that slips through these things.
That’s it for our presentation. Thank you!





























“We can catch hackers by putting an antivirus signature out or putting an IPS filter or some firewall rules. The reality is: that’s not the way they’re going to get you if they really want to get you. As they say, the determined attacker can’t be stopped. Everybody familiar with that?”
Good statement..!!
There a guy buy juine charles talkin bad to me threating coded messages he gave me his no 5413755680 what do i do