
 Diana Kelley (Partner, SecurityCurve) gives a presentation at InfoSec World Conference to outline the background of the iOS and speak on security of iOS devices
Diana Kelley (Partner, SecurityCurve) gives a presentation at InfoSec World Conference to outline the background of the iOS and speak on security of iOS devices
Hello and welcome! I’ll talk a little bit about hacking and securing the iPhone, and iPad, and the iPod Touch. Does anybody know why we can say that we are hacking all of them when we have a single device? Yes, they are all the same.
I actually have a question about what iOS is, but you guys already know the answer to that. We are gonna talk a little bit about the iOS which is actually used on some other devices as well. Any Apple TV users? Yes, got a couple.
We’re gonna talk about the headlines, the hacks, and the breaches. We will have a demo. The demo is going to be around jailbreaking. So we gonna show you jailbreaking with three different pieces of software.
Now, unfortunately an iPod cannot actually share its screen with you. Well, we can show off an iPod or iPad as either a static photo – so a screen capture photo – or movie. It’s great you can put your movie from your iPod on to. But what it is unfortunately not great for is for the kind of demo that I would like to do here. So for that portion of the program I have the screen captures off of this. I’ll be doing it live so you will be able to see things happening. But unfortunately because of the limitations we cannot get that nice beautiful side of seeing it in action.
But here is something that is fun. The really interesting side is on your PC as well, so you will be able to see live as I jailbreak this. You will be able to see that happening live from the PC side, because it’s the PC side where you control the jailbreak, just so you know what we will be seeing there. That’s gonna be the demo. We actually will be demoing with LimeRain1 and Redsnow2.
Is the iOS enterprise ready? Because there is hacking, there is a hacking school, it’s interesting, it’s fun. If you are a developer it’s a really good way to get control of your iOS device.
But for a lot of us, if our job is securing, we need to secure – what can we do to lock the devices down, and how can we secure them, are they ready for the enterprise? So we will spend time talking about that so that you can see how to actually do that. There is a general configuration demo that focuses specifically on the issues that you can control. You can do this over the air from a central management device. And you can do it right on the iOS device itself. We are going to show you doing it on the iOS, but obviously if you’re gonna deploy this in a large environment, you wanna put the same kind of controls for the enterprise itself.
What is the iOS?

We have answered this question: what do these devices have in common? These are all iOS devices. And ‘i’, I guess, is Internet. Steve Jobs seems to have loved the ‘i’, you can iChat with your iFriends on your iPhone. I guess that’s where we got iOS.
Is anybody here a Cisco router admin? You have a warm place in your heart for IOS3, don’t you? Because Cisco routers and switches run the IOS. And I believe there had to be some little communication between Cisco and Apple when Apple wanted to call it the iOS. They are completed unrelated other than that they have got the same names. But the iOS is what runs on iPhones, iPads, iPod Touches, Apple TV. The Cisco IOS is the operating system for their routers.

How many folks here have iPads, or iPods, or iPhones? You got a lot. How many of you have already jailbroken your stuff? You guys can come up and share the demo with us.
So, a little bit of background on the iOS itself. And this explains a little bit about why people want to jailbreak it. Jailbreak sounds kind of cool, like: “Oh, I am gonna do something really fun and funky with my phone, and get it out of ‘jail’ free”.
There is actually a real reason for this. This is a Unix based system. And in Unix, there is a concept of the Root, or the Super User. It’s similar to Admin on the Windows system. And the Root, or the Super User, can do a whole lot of stuff that the average user cannot do. iOS is built on top of that concept. Another thing that the iOS has – not necessarily security yet but I am interested in how researches are gonna go with this – is multi-touch. So you can actually, with your fingers, change and interact with the operating system, with the application itself.
You might say: “Hey, how is that security?” At this point, I don’t know of any interesting research on how that is security, but I think it is something to consider. This may be something to watch with if there is a way to exploit that.
The iOS was not fully multi-tasking, so it got multi-touch but not multi-tasking, until April 2010.
It is very friendly with third-party apps. Ted Mosby from ‘How I Met Your Mother’, he is the voice of Apple, there is an App for that. And we all know this now, his voice sometimes rings on people’s ears because Apple has reminded us again and again. There is an app for that. So we have a lot of developers that are creating things that they can either sell or give away free that can run on the iOS. It comes with native SDK. Right now, there are over 300,000 apps in the App Store.
But Apple has some checks and balances on the apps that go into that store. One thing that right now isn’t going into the App Store for example is antivirus, possibly because the iOS would never get a virus, or because of interaction that the antivirus would have to have that isn’t approved.
But there are certain things that you cannot be approved to be going to the App Store with, as an application. So that has created sort of a grey area where some developers want something that wouldn’t necessarily be approved. It doesn’t have to necessarily be malicious.

The iOS makes strong use of Digital Rights Management as well. We’ve got that already it is supposed to actually stop mis-use. So there is strong support, it’s gonna control that mis-use when you tether back to your device. Some people feel that this actually is a problem because that really restricts your ability to use the applications, it makes it ‘defective by design’ rather than ‘secure by design’. So if you feel that way, this is gonna help you understand why some people want to jailbreak, why they want to get out of the sandbox. It is the way that the iOS is used now un-jailbroken.
If you are developing, what are some of the things that you have to do? You do have to have the application vetted by Apple, to see whether or not it can go into the store. Then you’re gonna have to have it signed. And it’s gonna get up there and it’s gonna run in its own little sandbox. So they control a certain amount of what does and doesn’t happen with that application. They also require that there is a distribution fee, a lot of developers don’t like that. And they can remote delete it.
So if you are a developer and you got an app in the App Store, this is okay with you. And I am not saying that there is anything wrong with this Apple’s approach. I’m just explaining what the parameters of their approach are, so you might understand a little bit more about what’s going on with why people want to jailbreak.

So what is jailbreaking? Jailbreaking is essentially breaking out, it’s becoming ‘root’, it’s the ability to super-use on your iOS. And it means that you can install applications that aren’t in the App Store.
It’s the same as if you super-use on Unix. It’s as if you were becoming an administrator if you ever used a Windows system. You set the full control of the operating system on the device. And all of the time that we are using an unbroken iOS device we are not the ‘root’, we are not the Administrator – we are users. Jailbreaking essentially gives you the ability to become the ‘root’.
It also means that you can get apps that aren’t approved, that aren’t code signed, that aren’t in the App Store. You can get them installed on there. So it is a number one reason for people to jailbreak. I also think the number one reason for a lot of people to jailbreak is to get the apps that are not in the App Store. Though I think for hackers (I mean hacking as a traditional engineering, you know from the 60s, 70s definition of it), I think their reason is just curiosity: “How do I take this apart? I cannot actually understand how to use this unless I take it apart, so let me go ahead and take this operating system apart”.
Also some people do this to unlock the SIM. So this is another thing. I think this is where this really hit the media the most. You don’t like AT&T for example. So how are you gonna be able to use it if you love the iPhone, how are you gonna be able to use it outside of AT&T? Well, you can actually get SIM unlock software. But Apple don’t really want to distribute SIM unlocking software in App Store, so where you can get it and use great device is in Cydia1. Cydia is where the alternative App Store is. And then, the last reason for jailbreaking is just for getting an increased control.

This question comes up a lot – is it legal? So if you’re gonna go ahead and jailbreak your device, and maybe somebody is coming here to find out how to jailbreak it at their home out of curiosity and jailbreak afterwards, probably you wanna know if what I am doing is against the law. Or what if you are an auditor or a security person and you wanna make a policy that your employees can’t jailbreak. Can you say we can’t do it because it’s illegal? No, you can’t, it’s perfectly legal to jailbreak your phone. And it is regarded as ‘fair use’ under the Digital Millennium Copyright Act2. It has been found to be ‘fair use’, so you are not gonna go to jail for this.
And you may have heard some stuff about jailbreaking with somebody who often gets associated with iOS. You can actually use one of his pieces of software. His name is George Hotz. He goes by the handle Geohot. And he was just in court against Sony because he likes to jailbreak stuff. So now that he has jailbroken the iOS, he has jailbroken the PSP. So Sony took him to court and they’ve settled. He is not going to jail. You may have heard his name in relation to Sony. Once again, the DMCA has protected the jailbreaking in general, it’s ‘fair use’ if you’re gonna jailbreak, specifically if you’re gonna jailbreak your iPod or your iPad.
But it’s gonna do that second bullet down there, which I am sure you’ve already read. So you spend a lot of money on your device. You get your targeted best buy, and you buy your Apple device, jailbreak it, it’s not gonna be under warranty anymore. So that’s something to consider.
It won’t break it, we don’t think. I’ve jailbroken this a number of times. Not sure I trust it to do anything on here because I keep jailbreaking and un-jailbreaking it, but it will not stop your device from working. I’ll show you how to restore, it’s completely doable. You got a phone, you’re still gonna be able to make your own phone calls. You can un-jailbreak it by going back and using your iTunes to actually do a full restore if you want to. And you can do a complete un-jailbreak, which really just takes it right back to the default, I mean complete restore, it’s not actually called un-jailbreaking. Or you can restore the things you have backed up like your photos and pictures.

So how do you do this? Well, there are some freely available tools that you can get to actually go ahead and do the jailbreaking. They are free, George Hotz’s stuff is one of them. Most of this stuff is built on other researchers’ information.
But this is an ‘arms race’. So the software I am gonna show you today is not listed in your slides, and I actually don’t have screen captures of the software, one of the pieces of the software I am gonna show you today. The reason is that it came out this week, so I didn’t have time to capture it for you guys, as you can imagine these slides were done much earlier.
Why did it come out on Monday? Because there is a complete ‘arms race’. Every time a developer figures out how to jailbreak – and it’s really a few developers that are actively in race – but every time they release a new version of the jailbreak tool, Apple releases a new version of the phoneware. And so it goes back and forth. I actually have a slide, I’ll show you, where you can see this back and forth going on really. When I actually did all these screenshots I used an older version, it was George Hotz’s LimeRain. And now you see the newer solutions, the RedSnow is being wrapped around the LimeRain break because this is just very, very fast.
Tethered versus untethered – this is another thing. Sometimes the jailbreakers would figure out how to jailbreak but they cannot get it in untethered mode, so you might hear that, you know: “Yes, they got it broken but it’s tethered”. First time I heard that I was like: “Whatever”. So tethered versus untethered goes down to whether you can reboot the device when it is attached to the PC or not. If it is an untethered jailbreak, you can go ahead and reboot it without having to be connected.
As the breaks come, sometimes it is easier to get the jailbreak for the new version of the iOS but it is tethered, and then you’ll see a few days later, oh they’ve developed one which is untethered. So you may hear a lot of chatter about it like – is it tethered or untethered.
Is it hard to jailbreak? No. It is really not, but it depends on your iOS version, how easy it is gonna be, and it also depends on whether or not you’ve got the latest version, whether you’ve tested it, whether it is working, because some of these work a little bit better than others. When I wrote this I set the jailbreak for iOS 4.2, this was accurate at the time that I wrote it. This is out of date now. So it’s all moving very fast. There were all tethered now. They were all tethered up to 4.3.2 version, and they are untethered as of Monday.

So again, depends on the iOS version. If you really got an old version you might think: “I don’t want to update my iOS, I’m fine, it’s like version 4 and it is good”. If you are back away with your iOS on your device, you’ve got one of the easiest ways to jailbreak of all, because there were a lot of holes that allow jailbreaking back in the day. So if you are 4.0.1 or earlier and you’ve got your device with you, let me show you what you have to do. Go to this website – www.jailbreakme.com from your device if you want (see image). Warning, warning – you know you’re gonna void the warranty and everything I said about.
So if you are not the kind of person that’s been updating frequently, then you can go ahead and do it easily. So that’s what you get. This is how easy it is.

These are kind of big, well known, popular jailbreaking solutions (see image). I don’t understand the Snow. Does anybody understand why Snow? Snow, Rain? I don’t, I haven’t found out what the secret is, but if you noticed a lot of these have Snow or Rain in them, and they have kind of switched letters for numbers sometimes. So if it looks like it is not actually a word, just transpose in your head that they actually probably put a number in. So Sn0wBreeze – that’s a zero up there, LimeRa1n, and then we got GreenPois0n, Pwnage Tool, and RedSn0w; as you see, some of these might have numbers instead of some letters there. RedSnow right now wraps around LimeRain, and the Jailbreakme original flaws are actually part of LimeRain. So they are all working with each other. RedSnow is right now doing the fastest development.
So a little bit of a chart. I took this off of Wikipedia and you can see it up to April 18th. This is a quick rundown of how quickly some of this stuff is changed and why it is going so, and bottom line, again – it is just gonna keep going. It is just gonna continue to be very, very fast.

Let’s actually take a look, we’re gonna look at LimeRain – it’s at limera1n.com (see screenshot). And this one was for the 4.1 that I showed you, so’re we gonna start LimeRain. With some of this, you kind of have to dance a little bit with your Power and your Home buttons as you hold them. So if got to do the device firmware update, the DFU mode1, that’s the Power and the Home; these jailbreaks depend on that because that gives them access to do what they need to do on the device. You will see there is a little bit of dancing. And if you get it wrong, don’t worry, it is a little bit hard to keep up with.
We’re gonna start that, right now what we’ve got over here is just a regular screen because we haven’t started talking to it yet. Okay, I am tethered, so now I am gonna go and make it ‘Rain’. So hold the Home and Power and wait a bit. Now release the Power button. I often release the Home button but I got it right this time. Now it is in DFU mode, that’s brought our device firmware update mode, and it’s doing its thing, and we wait. Now, this is actually gonna fail because LimeRain hasn’t been updated for this version. So it’s the next version.
If this wasn’t the newer version of the iOS, this would be true, what you are reading now is that it doesn’t know it failed. My iPad knows it failed but this doesn’t actually know it failed. So it says here: “You are ready, turn it on, untethered, thanks to the guy who did jailbreakme, and you are good to go”. So again, if this was an older version it would be good to go, and when I first did this it actually worked. So not too hard, except for me little bit of holding the Power down.
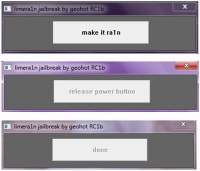
So this is the Download for the site if you go to LimeRa1n.com, that’s what you would actually see. You can see the ‘make it ra1n’ option up there (see image). So you got the LimeRa1n. You got rain in the background there. Cydia is where they keep the apps that are not in the App Store. Now you can get the apps that are in Cydia, and you can go ahead and you can install Cydia as the package if you want to try it out and see what it’s got in store. And I did, I went ahead and installed it. And I came up with what you can see on the iPod right now, what I had was LimeRa1n and Cydia were now installed on the device (see image below).
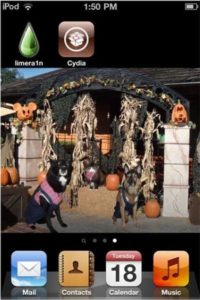
That’s about all you can see. Now you can actually go forward, with the new Cydia you can download the apps that are there. Cydia installs a remote ability to connect to the machine remotely, a Shell. Something to think about. I’ll give you a little bit of warning about that and why you care about that. But as far as what you see on your actual device, you don’t see a lot. This is what you would see. It didn’t break my photos, it didn’t break how my iPod was working. It just put those two on there and enabled me to do things I couldn’t do before I was jailbroken.
Alright, let’s do something else here. Let’s talk about the new one that just came out on Monday. This is RedSnow. Now, before you run RedSnow, you need to know a couple of things. You need to know where your IPSW2 is. You also need to set the permissions on this to run in Windows XP Service Pack 3 mode as it won’t run otherwise. At least I haven’t been able to get it to run, and that’s the recommendation, and I know I can get it to run now.
The other thing is that you do have to know where your backup file is. Has anybody ever gone to look at their backup file? I’ll show you where it is. It won’t find it automatically if you are trying to do this. So here is RedSnow running. It says: “Hi, I am RedSn0w, I like spelling things with a zero instead of an O”. And then it goes: “Do you wanna go ahead and install?” And it does actually warn you right here that it needs the IPSW. Alright, I’ve already told it where it was, so that you guys wouldn’t have to sit here and watch me fuss around trying to figure out where it is.
But let me show you where it is. So it’s in the Users, you go into your computer, you go into Users. If anybody has gone in there and poked around you might say: “You know, I’ve never seen the app data”. Anybody ever tried looking in your User directory? It’s hidden. So in order to use this you’re gonna have to unhide these folders as well. So you unhide them, then you can find them and then you can point RedSnow at that particular file. I have a copy just in case, testing it earlier today to make sure it should run for you guys.
Now, let’s go ahead and process. So it’s getting ready to jailbreak this. It’s gonna ask me whether I want to install Cydia as well. And again, what is Cydia? Cydia is the apps that you can get that aren’t in the App Store, so most people wanna say ‘OK’ and click Next. Now it is saying what I need to do. It says: “Your device needs to be off and plugged in”. So let’s go ahead and turn this off. So it’s off. Now we need to hold down the Power button and then hold down the Home. You have to be fast if you are a jailbreaker. Alright, so now it is waiting. You see LimeRain is coming up, it is wrapping around LimeRain and exploits. So now it’s gonna go ahead and reboot.
I’ve got on here that it is downloading the jailbreak. And we’ve got a message up here saying what it is doing as well. Now let’s go ahead and reboot. There is a whole lot of stuff going on the screen, and right now it has been jailbroken. This actually is now gonna take a while to finish. So I am going to let it go off and do its thing. Again, I am gonna have Cydia. So that’s what are you doing. The core of this is that you are able to go ahead and be Root on the iOS.
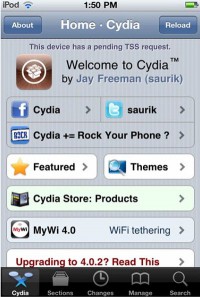
What does Cydia look like? Here is the Cydia if you go to Cydia from your device (see image). Here is what you can see. You can see, you know, they have WiFi tethering for your device. They got a store with different products. People do actually develop for fee applications that they sell on Cydia. So you got information about what you can get, like you can get cool themes and things like that.
Several more things. Again, you can still have your songs over there and you can send them back and forth. And you can update the iOS but then you probably will have to jailbreak it again. And it is a good question if it matters which jailbreaking software you use. You know what usually matters, like ease of use and, again, whether it works on your particular version of the iOS. Those would be the main ones. That’s really the big differentiator. But they do essentially the same; and then – tethered/untethered. I mean, at this point RedSnow is all that, and they are really keeping that tool up and it’s good with 4.3.2, which is a newer version of the iOS. So it’s more about getting the tool that works at the time.
I don’t know if Apple is watching you and if they are keeping a record of whether you’ve jailbroken or not. They know when you reset, I am gonna show you guys the reset, so they do know when you go ahead and reset, but I don’t know if they also at this time get a little notice, you know, there is some meta data that says it was jailbroken.
You can reset for a lot of reasons. And just the reset will not tell them anything. You can just put in an app that doesn’t get along with your version of the iOS, and the best way to solve it is just go and reset. But remember it’s not illegal, it’s just gonna break your warranty.
As to exploits that can jailbreak your phone without your knowledge, to my own knowledge there are no such exploits because you need to do that DFU. So you actively have to participate in the jailbreak. However, by jailbreaking your phone you are opening yourself up to specific attacks. So that’s the really key thing. Right now I don’t think anybody can jailbreak your phone without your knowledge, but if you jailbreak you can get exploited. But if you don’t have it password protected and somebody steals your phone, he can jailbreak your phone. If you can’t unlock it – you can’t jailbreak.
With the jailbreak you can get SIM unlocked and you can break your phone and use another provider, but not a radio network, it’s not compatible. But I would strongly recommend not jailbreaking your phone for any reason and specifically just to get to another provider. But that is one use case, and as to the radio portion of it you need to also be compatible because we all have different, you know we have GSM, we have 3G, 4G, so you have to think about that too.
Once you’ve jailbroken your phone, how can you be sure that the apps you download from Cydia do not contain malware? And this is one of the reasons that Apple says: “Don’t jailbreak your phone and use what’s in our store”. They are saying that they are going to vet it for malware. How closely they vet it – we don’t see, but they do some vetting. Who is vetting what’s in Cydia? The public? So you don’t know that you are not getting a piece of malware if you are downloading from Cydia. I am not saying everything in the Apple Store we know for fact is a 100% good but you got a layer, you got a check and the bounds, but you could get trojan-based malware.
You know, RedSnow itself could even be a piece of malware. That’s possible too. Think about it – when you use a hacking tool, and it’s true, you are actually opening yourself up to some potential threat; sure, this could be actually a big botnet tool. And again, I repeat I’m making no indemnification about using any of these tools either, so use them at your own risk, and yes, there could be malware in them.
Let’s now think of the motivation of creating jailbreaking tools. So George Hotz is the guy behind LimeRain, and this guy is also behind jailbreaking the Sony Play Station. Why does he do this? You know, it’s like the old engineering hack, I mean there really is the desire to understand and be able to learn more. And there is some anger. When you install Cydia package it is called a monopoly in a way. Some engineers feel very constrained or controlled by the limitations in the DRM1, with an iTunes Store and App Store. And they wanna use the device but they don’t wanna have to be limited by that.
So that’s some of the motivation, as far as financial aspect is concerned. Is this a going business? No, right now it’s a freeware tool. But could there be other motivations to these gentlemen’s point? Could they really just be trying to make a giant botnet with everybody who is willing to put a jailbreaking tool on their PC or their Mac? That’s possible. But at this point, from what they’ve said and what we’ve seen, these are mostly engineers who really want to get more control of the device itself – you know, for engineering purposes, to be able to investigate and write whatever they want.
You might also wonder whether there is anything residual after you’ve jailbroken it and restored. For the average user, no. I mean, it all goes away. But you are limited now by what you can look at on your machine because you cannot actually be Root on your machine and look at all of the different bits of information. So it looks to you as the user, and the folks that create these tools say: “Yes, it’s gone”. And the experience that is off there, is it possible to keep something on there if you do a full factory reset? It really shouldn’t be because you can really do that full factory reset, Apple is gonna take you right back to what you got when it was shipped. So it really should not be there.
I am going to talk about securing it too. I think it is important to understand how to break this stuff but we need to know how to secure and protect this stuff too.
So let me just run through deleting this. If you go ahead and you delete it, what you would see if you are deleting LimeRain is it just gives you a little signal that it’s deleting it. And where you’re going through to delete it – you delete it through the iTunes store (see image). Let me just fire up the iTunes Store. Here is the check for the update, I actually have the latest. And you have the option to go ahead and click Restore. Let’s send my iPod back to where it was. The next thing that would happen is it would actually go and it would talk to Apple. And it would say: “Okay, I’m gonna go to initial point” Not necessarily is it jailbroken, it’s just doing a reset. So it goes out to Apple, it does the reset, and it will actually bring this back either full factory or back to where you were with your photos and your songs.
Let’s talk about some other reasons that people want to do this. There is the SIM, it’s your subscriber identity module, it connects to your carrier. It restricts the devices based on mobile network code, country code. And some people want to be able to use it in a different way, like what if I want to use another carrier? That’s one of the things that people do, you do need to actually break the phone to do that.
I said before, the iOS is device, device, device, it is all the same. A little bit different. The iPad has a new kind of SIM, it’s got the micro SIM. So although it is using the iOS, you’re gonna have a different SIM card in there. And with the SIMs and the type of SIM, it is why people want to do it. I don’t like AT&T, I want to get off.

Does it make it less secure? If you are not careful – absolutely, it does. Does anybody know what ‘alpine’ is? It is root password on all of the devices. So you just jailbroke your phone. And we know root is really important to count. So you jailbreak your phone – you make it accessible remotely. And if you don’t change your root password, everybody in the world knows what the password to be in complete control of your phone is. That to me makes it a little bit less secure. You can change your root password. You can actually get a command line interface and go ahead and you can change your root password on your iPod after you’ve jailbroken it. But remember you’re gonna have to do that. So in my mind, I think it is less secure unless you really know what you are doing.
We have seen a worm come out. This isn’t necessarily related to the jailbreaking but there was a worm, a proof of concept.
And I’ve got a quick question – what if I don’t install the SSH2 terminal? Yes, you can still have the same problem, in terms of it being remotely accessible. And also it’s gonna limit what you can do with the jailbroken phone. Again, if you are installing these packages, you really need to know what you do.
Let’s go back to the Ikee worm3, November 2009, sort of the first known one. Like any kind of attack, it started up as proof of concept. Remember the Morris worm? He just wanted to see if he could spread email through the university system. Nobody expected it to be as bad as it was. So this is also a proof of concept. It wasn’t malicious, no damage. It just rickrolled your screen. So there was a singer Rick Astley, it was his song from 80s, infectious and catching and good too. And rickrolling is when you send people over to that. Because to this gentleman’s point, it cannot be psychologically damaging if you have to hear this.
But what did it prove, it proved we ccould do something with it. And about two weeks later, somebody somewhere decided: “Okay, let me pick up on the exploit that was in there”. And they did so it was like it came from ING. And it is not that ING being insecure, this just happens to be what the attackers like. They like names that people trust. I was just at the local branch of my bank, and I felt very, very sad. I heard this gentleman talking to the person at the desk, and all I heard was: “But it had the Bank of America logo. I wouldn’t have clicked otherwise”. Attackers love banks because we tend to trust them. It was a fake login page. And this particular exploit did in fact install command and control, the kind of agent that you need for a botnet.

And this one, AT&T wouldn’t want this to come up. But it came out in the headlines a lot as: “iPads are insecure”. And if you really unpack what happened in this AT&T breach, I think that we could more accurately say the application, the web-server the AT&T was using – was insecure, and it did lead to a breach of information which was on the backend. There was a problem with that application, and it did expose username information for iPad owners. And it was email addresses in the ICCID, which is the integrated circuit card identifier, so information about the hardware and information about the user.
But again, in security we’re always claiming the attack letter because the attackers are claiming the attack letter. Maybe linking an email to the ICCID is gonna be something that can be exploited later. And like in another attack like this, where they put stress on: “Yes, but it is only your email address, but that’s basically public”. That’s true, but it was your email address, and there was the fact that you were getting emails from, say, Disney World – you know Disney communicated with you. Now, Epsilon breach means the attackers know that Disney communicates with you. So it could lead to spear phishing.
So this could lead to deeper kinds of attacks, I think absolutely it is quite possible. But it was really more AT&T, it did come out a lot with the iPad, but it wasn’t strictly an iPad problem.

Okay, so the big question here is: can we bring these devices into the enterprise, or do we have a choice? I am not sure, at least from the companies that I worked with and the customers of SecurityCurve, I am hearing back that most security professionals, most security teams no longer have a choice. This is something that we were told: “Here comes the iPhone, here comes the iPad, deal with it”. I think we’re gonna have to just deal with that and move forward.
So it depends though on the needs of the organization. Sometimes there are business needs, sometimes we forget there may be a really specific business need, and it may not be as secure as we want. But the business may need it to move forward. I don’t know if there is an application on the iPad that is mission critical for your business or not, but I can’t say there isn’t. But you can still make your own ‘My Big Retail Store’ app for your internal corporate use.
But again, this is Root – jailbreaking gives you Root control. So when we look at the controls for iOS, they are depending on the User. And if User doesn’t have complete control over the device, Root does. So jailbreaking from the management perspective, there are reasons to not want it.
Jailbreaking certainly opens up the device in a way that you don’t have it opened up otherwise. But your device is plenty open if it is not protected. So the iOS itself is kind of free and happy and open, and there are a lot of vulnerabilities, for example things like password protection. You need to enable that, either centrally or on the device itself, you have those options. If you don’t enable that you’re not gonna have password protection on the device. And to the point about – could somebody just get my device and then jailbreak it? Yes, they could.
So password is going help you with encrypting the data on your device. You have the ability to control that or not, and it’s native. You can do this with the device. I am going to show you how to actually turn that on. But you have to turn that on, or you’re not gonna have it. So the devices are not entirely secure on their own, but jailbreaking certainly opens up a lot of paths to other nefarious things that can be done to the phone that weren’t opened up otherwise.
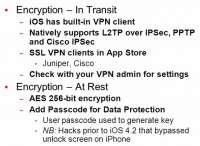
Let’s talk about some positives on the iOS (see image). It has built-in VPN clients that come with iOS. So for remote access, how many people allow remote access from just a regular laptop? Most of us. But how about from an iPad or an iPhone, are you requiring the VPN on that? I’ve got some Yes’s, I’ve got less Yes’s. But you can, you can turn on the VPN if that something that you want to do, it’s in there. And it does support Cisco IPSec and do L2TP1 over IPSec. SSL VPN clients – if you wanna do that, they’ve got Juniper and Cisco. Those are in the App Store, no need to jailbreak to get those, and again, it’s like setting up a VPN. So you can do that. This is going to increase the security. If you are going to start doing business from the iPad, this will help.
Now, a lot of us weren’t necessarily thinking about VPNs on iPhones, or even on iPods. Because these are great for watching movies on a plane, but you know what they are no fun to do on – type. So we just haven’t been typing a whole lot on these. So we’ve had the issues around, somebody downloaded it, they read the email, but iPads kicked it up a notch because now we got people typing a lot on these devices, and trying to do a lot of business on them. So that’s something to think about, and you can do it because there is the VPN encryption In Transit.
And then encryption At Rest, they do support AES2 256-bit encryption. Yes they do, but you have to turn it on. And that’s something that you’ve got to take the responsibility to do it, and you can add the Passcode for the data protection.
So before this there were hacks prior to the iOS 4.2 that bypassed the unlock screen on iPhone. There are probably gonna be hacks again. It’s always gonna be an arms race.
And if you have an application that doesn’t work with a native encryption API and doesn’t have any other level of encryption related to it, it wouldn’t be included in this. So with this native, you need to be linked-in, I mean connected to the API. You should always be careful because when I say stuff like that, people are like: “I heard somebody saying I need to join LinkedIn in order to get encryption”.

So some of the enterprise considerations about what you can do to protect. You can do a native Over-The-Air enrollment, you send users to a URL, where they authenticate. They then install a certificate on to their iOS device whichever one it is. And then there’s gonna be an XML based config profile (see image). This is native, this is supported with your iOS devices, so you don’t need to buy anything.
And there are MDMs, these are mobile device management solutions. They are commercial third-party solutions that you can buy to give you some additional support and protection on your machine. They work with other than iOS devices, so there are other alternatives but I am sharing with you what you have got natively. So if the issue has been about having no money, these are gonna be native, these are available.

What can you control? A lot that actually really manages your security. Password-protecting – do it. I mean why would you not have that device password-protected? Because it is a pain to take it off, this is the big problem, especially on these devices. Who is good at typing on that little keyboard on there? I am constantly fat-fingering trying to get my password in. So you’re gonna get pushed back: “We don’t want to do the password, we don’t want to actually have it on there because it’s a pain to unlock it”. But it’s gonna give you some security.
But when the question comes up: “Is it ready for enterprise?” – it could be a lot stronger than we tend to deploy it in. So absolutely, you got to have a password policy. You can actually set whether you have a good password or a bad password, or a stronger password rather than a less strong password. You can lock out after a certain amount of failed logins. Because if you don’t lock out, what can happen is somebody’s gonna sit there. If you got a fairly weak password, maybe they will be able to figure it out at some point.
The VPN configurations, WiFi settings when you connect to what you can connect to. And then you can do some mail and calendar account settings as well.

For some centralized management, there is native support for EAS. I get some smiles when I mention Exchange ActiveSync. So it is a protocol, but it does work with Exchange. It’s actually a protocol that can be used for mobile device management, actually for other kinds of device management too, but it’s mostly in mobile. You do need to have Exchange Server for it, but it does give you some level of control. To those of you in exchange shop this is put on the iOS; you can use this as well, if you are in exchange shop.
You can also get certification based authentication back to the Exchange Server and remote wipe of device. That’s pretty good. What happens if you lose the device and all the data that is on it? So you can set up the remote wipe. You can also wipe on password failures. If this is a highly sensitive device and it’s got a lot of highly sensitive data on there, this may be worth considering because if you got somebody who has stolen it and trying to unlock it, you can know for a fact it’s gonna actually wipe if they get it wrong. And you can do things like blocking the camera.

So the MDMs, there are third parties (see image), why would you want this over when I was just talking about ‘natively’. In general, it is because you have a heterogeneous company. You may have just the iOS there, but most companies have to deal with Android. In fact, Android is growing very, very quickly. It’s growing faster than the iOS at this point. So if you got to manage a whole bunch of different types of platforms in your mobile world, then you are probably going to want to branch out a little from the native stuff.
So what can you get if you get these third parties? Many of them are now operational as well as security oriented. And I think if you are wasting money, that’s a risk. So operational actually has, I think, a real security component, which is what if your quality of service isn’t up to speed with your provider? So some of these MDM solutions can look at things like how many dropped calls you are getting. Like the Verizon Wireless: “Oh, our house has been in a dead zone for years”. You can say: “Look, you said I was covered here and I am not”.
So you can have that kind of reporting with these tools. This is another reason to think about spending the extra money to get an actual management tool rather than just going forward with what’s native. So some of the vendors in this space, we’ve got Motorola Good, now it is Visto; also Sybase Afaria; also TrustDigital; and then Zenprise as another option for MDM solutions. So you can manage these devices centrally. That’s not a reason to say that they are not enterprise ready.
If you’re gonna go ahead and jailbreak, please know about the Secure Shell (SSH)1 tool, and know about the remote access. And if you have to have to jailbreak – change the Root password. I would also say: “Really think about what you are going to do in terms of why you want to jailbreak and why it is so important”. You are not a researcher, you are not in the lab, you are not a developer. Do ask yourself why you need to jailbreak that device. If you’ve got employees that are saying: “But I have got to do it”, make them justify really strongly why they need to jailbreak this device. It’s adding a layer of complexity to your job and you are losing some of the control.
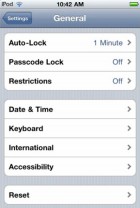
Securing the iOS itself, you turn on the Passcode Lock and turn off the Simple Passcode. For the Auto-Lock – you tell it when it’s gonna time-out. And we can do all of this if you got your iOS devices, we can go ahead, I’ve actually got screenshots for all of these. And then the restrictions as well. So applications and functions, you can do this remotely and centrally, but I am gonna show you what that means.
So the Auto-Lock – you have the option to go ahead and change that. Your Password Lock again, you wanna have this. And you wanna turn on some of the restrictions.
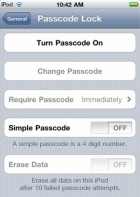
If you got your Passcode on, this will unlock this screen and then you can say if you want the Passcode on or off (see image). And here, remember we were saying we could have a stronger or less strong Passcode. This is what they mean. Back originally, it was like the PIN, it was like a 4-digit PIN to login, so you didn’t have the option to do a stronger Passcode. You can now do a stronger Passcode but you need to force that. So you set that. And again, this can be done centrally over-the-air too.
Let’s check if we could set, say, a one character password. Okay, let’s go. Alright, Passcode, Simple Password OFF, turn Passcode ON. Alright, just any character, we will use an ‘I’ – done. So strong Password will allow you to have this. That’s good to know. So strong Password, again, is 4 digits, but it apparently lets you circumvent. So we just set the Passcode, we set it to ‘I’, it turns out we did find the way to work around of being very strongly secure.
Auto-Lock – the question here is really how quickly it locks when somebody’s got this out in the back. People leave their phones by accident, people get up, they leave them, like at the meeting, right, you just got to run out. So, you know, trying to get it on the least annoying – one minute can be pretty annoying for your users.
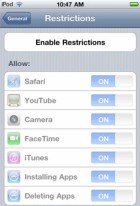
Your restrictions here: you can actually say: “You can’t install apps”. So that can be very helpful. You can also set it so you can’t delete apps, so deleting apps is not a possibility. So you have some level of control over what your users can and can’t do in terms of the applications (see image to the left).
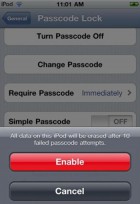
The Passcode attempts – if you want you can have you data auto erased (see image). The reason I am showing you this based on the screen like this is so that you can see where on the iPod or other iOS device this kind of control exists, but if you are in an enterprise please do not do this on every machine individually. What you want to use is you want to do the centralized management and you push it out to the machines. And this is just to give you an example of the kinds of things you would put into your policy.
And here is another one, this is on the erased data, so when you want and go ahead and say: “After a number of failed logins I want you to erase this”, and this is just an example, I set the restrictions. And again, you can set this from a central point and push it out to your users.
Just some last final thoughts, thinking about what we’re doing with the iOS. I’ve heard the jailbreaking was getting harder. But the last round, in the last couple of weeks, it looks like it’s been a little bit easier to get the jailbreaks out. So it is an arms race. It is moving pretty quickly, but Apple is very intent on not making the phones jailbreakable, and researches and attackers are intent on making them jailbreakable.
So we will see what keeps going on in the iOS and also if they will have better control over the apps in the App Store. One more thing you can think about as you are looking at this in the iOS and I think it is about all mobile, which is do you really need to store that much data on the backend? Sure, let them have their movies and let them have their music. But do you really need to allow your users to download sensitive documents on to their phones? How about just viewing it? They can view it on the server when they are connected to the network. Who is not connected to the network anymore? But they cannot download it.
So think about that. Because that is one way of tethering our data. It is not tethering the phone, tethering our data is a really good way to start to protect that data. I think it is usable. They get it through a VPN, so they’re reading it. Not visible when they close the connection? It is not on their device anymore.
So some of the new research, there is a lot of research that is coming out. At Black Hat DC 2011 some of the more notable stuff was breaking out of the sandbox itself, which was Dionysus Blazakis’ presentation. And then some over-the-air attacks, we are talking about that remote access, and this one was actually against the processor itself of the phone. So some interesting areas of research, especially if we start getting some sort of hardware remote type attacks. So there is active research in the protection. There is active research in the attack side of it as well.

Some final take-aways. Really please think about jailbreaking and if you need to jailbreak. It looks fun but what is the end state, what is the purpose of it? Have a good business reason. Make sure anybody in your company who wants to do this justifies to you that they really have a good business reason to do it. And if you’re gonna do it – know what you are doing.
There are exposures, we’ve got carrie exposures, network exposures, they’re gonna be outside of your control. If AT&T or T-mobile has a problem with their network, that’s not necessarily something that you can do yourselves. There are security features in the iOS – turn them on, although we’ve found an interesting workaround to one of them. So don’t not keep this turned on. You may get some push back from your executives, especially with the passwords, but you are doing a lot in terms of protection, because these devices, if they get lost or missing, they are not protected at all. It’s gonna be a lot easier to hack the data out of them. So you wanna do that. And definitely look for something central, whether it is native or something that you are buying, that’s third party.
At the end I have some links for you guys to use. RedSnow comes after Pwnage Tool2, it is the same development team. So if you are interested in the tool I used today it is that. If you want to take a look at Cydia without actually jailbreaking, you can look at Cydia, Cydia is that jailbreaking after the fact app store, so you can go ahead and take a look at it. And if you want to read more about that native Over-The-Air Enrollment and control with the iOS, you also have this link at www.apple.com.




























