
Freelance pentest guy Dan Tentler, aka Viss, delivers a talk at Defcon 20 about different digital control and supervision systems that can be accessed online.

Welcome to “Drinking from the Caffeine Firehose We Know as Shodan”! Anybody recognizing that scene? (Image 1) Did everybody watch old “Weird Al” movie?
 So, a little bit about me. My name is Dan, people call me Viss. I’m a freelance pentest guy. This is not just another shodan talk; today we’re going to be turning shodan into a gateway drug.
So, a little bit about me. My name is Dan, people call me Viss. I’m a freelance pentest guy. This is not just another shodan talk; today we’re going to be turning shodan into a gateway drug.
Normally, what people put on the Internet is what shodan will find, and that’s kind of boring. We know you can find switches and routers, and servers, and cameras, and stuff like that. What else is there?
I don’t know if anybody is actually doing this yet, and I don’t think there is any kind of accountability, so I figured that I’d poke that bear.
So, a little bit on editorial policy. Anybody work for an organization that prevents you from scanning yourself? Like, under penalty of death, no Nmapping or they will drag you out to the parking lot and fire. So, the bad guys can scan us, but I can’t scan us? Great! If you don’t know your own attack surface, then you’re crippling yourself against the bad guys, right?
So, before we get started, this is entirely read-only. Yes, I was connecting to random stuff on the Internet, but it was for screen charts only, there were no changes made, nothing like that. No systems were altered, entirely read-only.
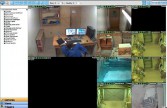
So, first and foremost, let’s get straight to the fun stuff. A lot of cameras – like, thousands, tens of thousands of cameras. These are March Networks cameras (Image 2), which is really funny.

And when I connected to this camera, I saw something that seemed pretty interesting. There’s a dude looking at monitors that appear to have exactly what I’m looking at on them. So, who watches the watchers? Me! I watch the watchers (Image 3).
Scada gear, that’s popular, right? Let’s beat up on that. So, Scada gear on webcams… well, you have Scada equipment, it’s bad for you to put Scada equipment on the Internet, we know it; so put a camera on it and put that on the Internet, great move! (Image 4)



Other random stuff on webcams. This is some German thing counting cubic meters of gas, ok (Image 5). But generally speaking, cameras are horrifically, horrifically boring. At the moment, I have about 3900 cameras, and when I look at them in the browser, it looks just like this: people’s garages, old dude in the living room – boring (Image 6).
And then I came across something like this (Image 7). What on earth is this thing? What is a T-2000? Who’s ReliOn? I’ve never heard of these guys. What’s the deal? So, Google to the rescue. It’s a hydrogen fuel cell that is used for industrial stuff (Image 8) that you can telnet into, no creds. That’s fun – now you can telnet into these things.
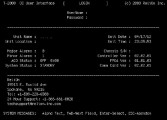


It looks pretty industrial, you can find a bunch of documentation about the thing online (Image 9). A lot of military installations tend to use this thing (Image 10), and they’re apparently happy with, you know, random PDFs on the Internet containing what military installations use this thing – great! Here is how you use it (Image 11); it’s a simple electrical connection diagram, right?


So, where would you normally find these things? Ok, now I know this thing and I know you can telnet into it, and I know you can find it randomly on the Internet by looking for 5 minutes. That’s where you find them (Image 12).
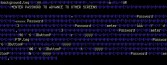
All the things that you connect to randomly on the Internet, that are not servers and switches, and routers – their security is horrifically, horrifically bad. Here is an example of a file that I pulled off of an energy meter of some kind (Image 13). The link to this file existed in the source code of the main index.html, and if you just hit this thing with Wget and you literally open it in VI, I won’t tell you what the password is, but it’s there, and that’s in clear text. Thanks dudes!
Wind farms, giant fans that generate power from wind – this one is generating 37 Amps, not bad (Image 14).
Lighting, HVAC, alarm systems: this is some Cathedral or something I found – no creds, you just hit it with a browser and it shows you: “Here is our stuff, and here is what the temperature of everything is.” (Image 15) Even down to the room, you can find out what temperatures in different rooms are, you can mess with them if you really want to (Image 16).
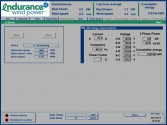
Power meters – some of these things are really cool. The graphs – I’ll come back to this later – but you can do trending based on the stuff you find here (Image 17). If you really want to be ultra creeper mode, you can watch these graphs and see when people turn the lights on and when people turn the lights off – it’s creepy.
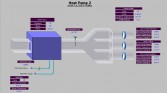
Heat pumps – this starts getting into the interesting side of things (Image 18). This is what you’d see in a building or in a large hotel, or something like that, where you have this giant thing and it’s feeding multiple rooms. No creds, point a browser at it, good to go. And they get bigger. This one (Image 19) has 3 water heaters, it’s got some sprinklers, it’s got a pump, it’s got some other stuff. Ok, this is getting interesting, right?
Private residences – really rich people tend to use these things, because it’s kind of a home automation thing, it’s kind of cool to heat your house with a web browser, or turn the lights on in your garage (Image 20). They exist, yes.
There’s trending data in a lot of these things, where you can identify at what times the power goes up and down, at what times lights go on and off, at what times air conditioning turns on, and things like that (Image 21).



This one (Image 22) was for a solar water heater, you can see how the hot water comes in and goes through the different water heaters, and goes up to the panels on the roof, and comes out; you can see the temperatures, you can see the pumps – that’s fun.

Familiar displays – you see that little thermostat there, in the bottom right-hand corner? (Image 23) Anybody ever seen one of those things? I was at Traffic Court last year doing traffic school, and we couldn’t figure out why the room was so incredibly cold and it had one of those inside. And every time we tried to bring the temperature up so that it wasn’t, like, 50 degrees, it went back down again. And after finding this I sat there on my coach saying: “Oh, I see, there’s probably some kid 2 rooms away manipulating it and going ‘ha-ha-ha’.” Glorious! So, you see those things, you know they are connected to a bigger system.
More power systems (Image 24) that will aggregate for apartment buildings; they’ll aggregate the readings from power meters: read-only, you can’t really do much with it, there’s no input, but it’s still interesting stuff, I guess.
Larger industrial systems, like the Siemens systems (Image 25). Who would look at that and say: “I’m going to put a web server on that; this seems like a good idea”? Well, somebody did. And now they’re on the Internet by tens of thousands.



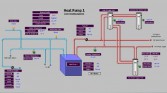
In some of these cases, when you start getting into these larger infrastructures, like you start getting into boilers that control hotels and giant industrial buildings, now you get to contents under pressure, so you start hesitating from the keyboard a bit, thinking: “I wish these water heaters had their own little security measures in them because, really, you could do some damage if you wanted to” (Image 26).
So, I found a whole bunch of stuff, but what can you actually do with this stuff? Well, OSINT is fashionable, let’s do that, right? So, level 1, simple recon; creeper mode, level zero.
You can install a tool that I was using, called Chrome Ultimate Flag which will tell you a little bit about the IP addresses you are visiting, the city, and stuff like that (Image 27). That’s crafty if you find 10,000 webcams and all you can see is just a square with a video, there is no extraneous information or anything like that. So, it’s cool to know at least what city it’s in.
So, if we look at a camera system like this, what details can we see? (Image 28) Well, it’s daylight, it looks outside, it’s somewhere within some time zone, near you maybe. You can maybe zoom in at the license plate so you could see what state they are in, something like that. But in the top right of the frame, the top right photo here, you can see that the camera is pointed at the door, and the door has the company logo on it. So, that was as easy as just taking a screenshot and flipping it.



And off to the right you can see that there is a desk with a computer on it, and that particular camera was pan-tilt-zoom. So, with no creds, you can log into this system and pan-tilt-zoom around the camera in the lobby of this company. So, I did (Image 29). I don’t want to get anybody in trouble, so I blacked out the name of the place, but you can see the text under the little black box there, it says: “Security integrators”. Good job guys!
So, based on the name of the company and what state I could see they are in, I did a little bit of homework, and this is how far Google Street View got me (Image 30). This is still creeper mode, level zero.
Let’s get to creeper mode, level 1: interactions. Now that you find stuff on cameras, find stuff on the Internet, what can you do if you just want to reach out and touch it just a little bit?

I didn’t do any of this. This came to me after I published my first blog post with my script and some of the code that I used to generate the stuff, and I thought it was pretty funny. There were people that found a pizza place somewhere, I am not sure how, and found out what the name of this pizza place was, and ended up on the phone with them doing a bit of social engineering. And they found some really bored people at around 2AM in the back to hold up signs for the security cameras in the pizza place that were exposed to the Internet (Image 31). And some randoms on the Internet found them, called the place and started having them hold up signs. That was hilarious. And they (the staff) were very open to this, like there’s the girl on the phone with the caller, watching the camera. It is simple and pretty benign, but you can see how social engineering in this situation can be pretty hardcore.

Next level. You guys ever seen “Die Hard 4”? It’s kind of silly; they were driving a truck and hacking stuff. This guy (Image 32) did it with several million dollars and a truck full of equipment, and a black ops team and all this fun stuff – I did it with my laptop and a bunch of coffee.

This was essentially, if you remember the movie, just a gigantic social engineering campaign at the end. But the minute you find a device that has telnet open that will let you shoot down a helicopter with a car (Image 33), I will pen-test that system for free.
So, next – massive cooling equipment. This is a warehouse I found somewhere in Central America that had 14 gigantic evaporative coolers connected to it (Image 34). This is a food storage facility somewhere, it could have been a medical storage facility but each one of these evaporative coolers presumably could cool a room like this.
Its panel has details (Image 35), and you can connect to them and get specific data on what their names are and what buildings they are talking to, and things like that. So, if you are doing pen tests and you wanna do recon on a target, and maybe it is a retail organization, this is interesting stuff to get into.


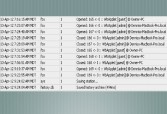
Some of these things actually keep logs (Image 36). This is really funny because once you get in and it is completely open, there are the names of the laptops of the people that run that thing. So, entirely without trying or by happenstance, there is intelligence leakage happening through this Scada equipment.
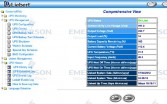
This one was a pretty hilarious find. Anybody familiar with the company Liebert that make giant UPS things at data centers? (Image 37) You can put them in test mode from the Internet. Test mode turns off the battery. What happens when you do that to a data center? People get angry! I didn’t do it but…

Some of these, like I mentioned earlier, have VNC Touchpanels. This one has some sort of liquid control flow valve operation, and you can pause and change the flow of the chart (Image 38). I didn’t really go much farther than this thing, but presumably you can change the flow rate of the valves that operate this thing. The numbers here read out something between 2000 and 2500 on the top end; I don’t know if that’s feet, or meters, or what, but a water pump that has these kind of figures might be doing something interesting.
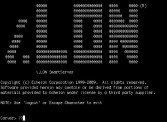
Ok, it’s interesting but it’s not like a ‘firesale,’ like a movie, right? Well, meet i.LON (Image 39). i.LON is kind of neat; it is a piece of hardware that was made to control LonWorks networks. Now, LonWorks was something where you have industrial equipment that needs to talk but people didn’t feel right putting it to the Internet, so they made their own network. They made their own network topography for these sorts of things, and they called it LonWorks. And then with anything else, somebody took a web server and Ethernet and put that on top of the thing that wasn’t supposed to be on the network.
And these, hilariously, are stackable, just like devo hats. You can have one of these controllers talking to 500 more, or, in this case, 3 dozen more (Image 40). This is a controller that I stumbled upon randomly, and they show several IP addresses which I blanked-out as I don’t want to get anybody in trouble, but when you open this little plus symbol there and the submenu items come in, they look kind of interesting.

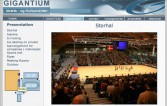

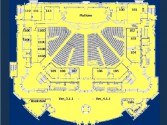
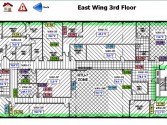
One of them I saw was Gigantium. Well, that looks cool, let’s google that, what’s Gigantium? Oh, it’s a stadium thing (Image 41), and under that wood there is an ice rink that you can defrost if you want. They host big events, and all of their alarms, all their lights, and the garage doors, and all of these things that you hear about in the movies are connected to this system – no creds, no passwords, nothing. Conveniently, they have a floor plan for you should you decide to target a particular area (Image 42).

So, I went back to the list and kept looking what else could be there. There is this strand camping place (Image 43) that has water slides and a lot of solar equipment, and I can’t imagine that their i.LON systems are controlling the water slides, maybe the valves there, maybe some of the solar power stuff, but that’s interesting.

Another one, that’s another sort of camping place that has cabins that you can rent, and the website of this place looks kind of cool (Image 44). It’s a facility that is somewhere out in Europe, and they market this to Americans too. You can go take a vacation there.
That’s fun: I can control ice skating rink, the lights, the HVAC, the power, garage doors, water pressure, boilers of something like 36 businesses in some downtown part of some city in Europe. So, we are getting a little closer to the movie. But in the movie (“Die Hard 4”), they were able to control stoplights and signs, and things like that.
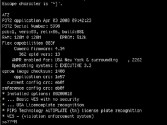
Ok, how about listening on telnet? These are intersections, like, stoplights, you can telnet into them and put them in test mode, and the warning says: “Don’t do this, you can kill people!” (Image 45)
Autoplate is another fun one (Image 46), these are red light cameras that photograph your car, OCR license plates and send it to cops. These are glorious because you can telnet into them and tell them to send the pictures elsewhere, no creds. And what’s really funny is if you look at the screenshot it says: “Basic VES with no security”. Awesome!


So, DakTronics (Image 47) – I got to give these guys a thumbs-up because everything was protected, but these guys make signs that do this sort of stuff over freeways, and they are also listening on port 88 and you can also telnet into these. So now I got red light, cameras, road signs, stoplights – check it (Image 48).
What else? Let’s do some current events. Anybody remember Ruggedcom? Ruggedcom was a fun one, right? So, if you hit a Ruggedcom box with a web browser you see something like this (Image 49: see left-hand part). Anybody want to take guesses on what those passwords might be? Because they send them to you and then they obfuscate them. So, if you view the source, or if you have any browser plug-ins that can de-obfuscate passwords, there you go (Image 49: right-hand part).
And the next one actually was an interesting one, the next one was sort of like: anybody familiar with those movies where some hacker dude does something, and then his phone blows up, and the government says: “Hey, hacker guy”. It actually happens.

I hit this (Image 50), and I thought it was not malware or anything. Maybe some kid defaced something. Look at all of these Java applets that I am not gonna let run. I took a screenshot and put it on Twitter. I had a discussion with a gentleman that pinged me afterwards and said that was actually safe, and I could run that.

So, I get my VM, take a snapshot, pop this thing open – and it looks like this (Image 51). Oh, megawatts? Yes, those are megawatts. This is a hydroelectric plant in Fumel, France, with their Scada equipment open to the Internet. They have 2 turbines and each turbine is generating something about 3 megawatts each. Oh, that’s kind of a big deal.
I didn’t put this screenshot on Twitter but the gentleman I was talking to said: “You’re gonna get a call from some interesting people”. I thought, yeah, some dude saying that to me on Twitter randomly, whatever. At 8:45 the next morning, I get a phone call: “Hi, my name is Anthony, I am calling from DHS”. So, that was interesting, that was one of those occasions when you hear about feds calling the hacker guys.
Satellite systems also listen on these things and, hilariously, they are a lot more boring than you think (Image 52); like, I remember as a kid I was like – yeah, I’m gonna get one of those satellites. Well, this is lame. They are open and they are listening, and you can see how many frames go back and forth. This, I think, is a television setup somewhere in Europe that is completely open.


This one is new – NAS storage arrays (Image 53), this came out recently, like several weeks ago. You get one of those storage arrays, and it’s a network device, and you can plug it in and do NAS and SMB to it. Awesome, go ahead and put that on the Internet too.
This one was glorious, I was in tears laughing: you can telnet into a car wash (Image 54). What the hell? That was interesting. The first time I saw this I thought it was Mission Impossible stuff, like you have your foreign diplomat go to the car wash, and you put the barriers up and spray the soap.
This one was double hilarious, this is massive humidifier systems that are in hospitals and industrial settings (Image 55). These things are the size of about 3-4 refrigerators side by side: 6 feet tall, 10 feet wide, 3 feet deep, and they make vapor. You think, ok, that’s not so interesting. They have a marketing video where you can connect directly to the board (Image 56). They have no idea what they are doing. Their marketing material boasts that their equipment is in the White House. Ok, good to know!



Emergency Telco gear (Image 57) is like VoIP stuff that first responders use; and it’s open and listening on the Internet. Ok, you wanna put some fake 911 calls in? You can do that.

Occasionally, some really old forerunner kind of stuff comes around and you see stuff like this, which I can give you a second to read (Image 58); and if anybody can spot the hilarity in here please point and yell. Yeah, support for Netscape 6, guys! This code was taken from geocities.
Did you know speakers have web servers? (Image 59) This one – you can send it an .mp3 and it will play it!


A wine cooler, a gigantic ridiculous wine cooler that has a champagne alarm in a giant hotel somewhere (Image 60). This is great stuff, often it is just funny during pen tests, and I can’t wait till I can put this kind of stuff in my report (Image 61).
So, thinking longer term, I mentioned the trending stuff earlier; there are tools in the battery equipment that will let you trend over months and weeks. You can start building profiles based on these things, like when people come in and when people leave, when the alarms go off, when the alarms are turned on, when the gates open and shut – all that stuff, doing profiles in long-term investigations.

Scanning the whole Internet is getting a lot easier, we can do this stuff, we can measure it now. If anybody saw any of my previous talks I presented a few months ago, I saw a whole bunch of ridiculous TrendNet cameras (Image 62) and I have some numbers.

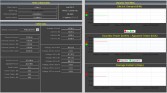
The first time I did this I found 560 cameras. There was a BBC article scaring everybody, talking how creepy it is that people can see cameras on the Internet. And then I did a re-test and found 25% less cameras or so. Then U.S. Media picked that up and the number went up. And then I did the test again just a little while ago and the numbers went up almost to what they were before, so scaring the crap out of people is a great tactic but it’s temporary (Image 63).
It does scale well and I’m working on it, so when I have some more interesting information with these numbers, I intend to come back and present some more. And if you want to stalk me this is how you can find me: atenlabs.com/blog | @viss.






























