
This is a revealing Defcon presentation by Backtrace Security representatives a5h3r4h and Hubris on history of the Anonymous, their methods and activities.
a5h3r4h: My name is a5h3r4h, I’m Director of Psychological Operations at Backtrace Security. Me and my colleague Hubris are gonna talk a little bit about the history of this whole Anonymous mess that’s happening.

We’ll talk a little bit about how Anonymous came into being, or supposedly came into being. Originally it’s a joke: you go to 4chan.com1 (or whatever ‘chan’) and somebody does something a little naughty or a lot naughty, and you go “Who did that?” – “Anonymous did that!” Anonymous posting, everybody is anonymous, therefore everything that happens is done by Anonymous – and Anonymous become sort of a living persona. At some point, this becomes a sort of a trolling movement – everybody goes out together and runs all over the place and messes with everybody and everything. For the most part, it’s fun, it’s lulz as every once in a while you’d have a little bit of enactivist attitude, so for the most part it was a joke, it was a fun thing, it was, you know, somebody acting up on you to have everybody go leave comments, harass them a little bit or whatever.

One day, somebody comes on and says “Look at this really funny YouTube of Tom Cruise acting like an idiot for Scientology, it’s really funny!” Everybody goes to see the video, and there’s no video, it’s gone. Why? The Church of Scientology pulled it down. Then someone put it back up – Scientology yanked it back down. It kept getting up, getting down, getting up, getting down – so down it went again. It was sort of snowballs, you’re not gonna get away with this, we’re gonna put it back up as many times as you take it down, and all of a sudden the next thing you know is it’s an international sensation: Tom Cruise, ‘Mission Impossible’ – “I am a scientologist”. And the next thing you know is the Church of Scientology getting the usual 4chan treatment – black faxes, 4000 pizzas (or over 9000), shipments of boxes from UPS (you know, bomb threats) etc.

So at this point, some of the people who have been kinda fighting Scientology for many-many years step forward and say “Hey, we’re really glad you guys showed up to join the party, but you’re kinda ruining it with all this illegal DDoS stuff and the faxing, and since there’s approximately ten thousand of you, why don’t you come out and meet the Church of Scientology in person and troll them there?”. And Anonymous said “Yeah, sounds like fun!”. And so ten thousand people all over the world showed upfront of the Church of Scientology and had a party, and Scientology wasn’t super-thrilled about that, but what could they do?
This was a pretty successful form of protest for a really long time, there was a lot of interest from more traditional protesters and protest groups because it was very effective, it was ongoing, it went on successfully for probably close to 3 years before it sort of fizzled out. Anyway, they called this the ‘adhocracy’ because this is a group of people that came together with common cause and zero organization, they just said “F..k it, we’re all pissed about the same thing, we’re all gonna go out there and do our thing”. Nobody knew anybody, keeping to the tenets of 4chan and the traditional idea of anonymity: everybody using anonymous handles, we’re not gonna talk about real names, we’re just gonna come out there and use handles.
And what turned out to be a very effective form of protest of course comes with a downside in that an Anonymous mob is an Anonymous mob and sometimes would act like a mob, so people who are targets are not always deserving targets, and people that anger the hive, so to speak, sometimes get an inappropriate amount of retaliation. So there’s definitely a dark side of all of this. There’s people who maybe disagree with the group, and as a result their children’s report cards are on the Internet.

So interest in Scientology afterwards started to wane a little bit, and then there appeared these issues with WikiLeaks and with Iran, and people started saying “Well, let’s just join this Iranian revolution idea”, and they recruited – and the whole thing swelled, and you have a lot more causes added, it starts getting a little bit more political, people start getting involved for personal political reasons. Unfortunately, as the media are speaking up on all of these things, they are calling Anonymous ‘hacktivists’. There’s no hackers in Anonymous, it’s just Internet people, they’re not explicitly hacktivits – they’re part of the crowd. But they’re going out, the media talking about the hackers because it’s a better sound bite to say all these hackers are coming out and protesting. Yeah, ‘mad hackers’ makes a better sound bite than people who hang out on the Internet.
And unfortunately, a little bit of the problem is that people started enjoying that idea – “Wow, we’re hacktivists, we’re dangerous hackers, everyone’s afraid of us”. And that actually starts attracting not always the good kinda hacktivists either – the people who are not necessarily pure of heart. So we get some people who by night are using their botnet for naughty-naughty things, and by day are coming forward and they get together and come up with this concept of Anonymous operations. They’re gonna go back to the old fashion Anonymous campaign, which is DDoS everything that moves, which is a debatable form of protest – obviously, everyone has an opinion. I tend to think that it doesn’t qualify because those guys have a problem with something, I wonder what they worry about.

So you get this huge outspread of things that are going on – all kinds of targets now. Well, let’s take on anybody who’s against free speech, let’s go after the Australian government. This is another problem when you have a crowd source protest – people sort of do what they do, and so one minute they’re going “Yeah, we like these guys, we’re gonna support them”, and the next minute they’re like “No, f..k that, DDoS those guys”. So you have the LOIC2 which is being kinda overblown by the media saying that all of these people have come together and downloaded this program, and they’re all individually DoSing these sites altogether as a form of protest, but in reality they recruited some rather threateningly large botnets into play. The first time that they really came out in force was the ‘Operation Payback’ when the funding was cut for WikiLeaks. The LOIC is not enough to take down a PayPal or MasterCard site though, so they found some friends of botnets and recruited them, so now we have half a dozen botnets, including some hundreds of thousands that can do an awful lot of damage with that. And of course at this point we’re entering into a strictly illegal territory. You can’t argue that a botnet is a legitimate form of protest – that’s my opinion anyway.
Anyway, this group is becoming larger and they’re using and utilizing more and more propagandistic techniques. And the funny thing is that when this stuff started around 2008, the propaganda was a joke: we were having fun with it, people were making goofy posters. And then, coming around 2010 it’s being promoted as a serious thing. All of the things that were said in just 2008 were a joke, and it’s not a joke now, it’s serious. Now the propaganda is real and you got this large group with lots of weapons and collective mindset. They’re like “That’s good”, “Oh, those guys – we don’t like those guys, go after those guys”. They did a lot of good things, I think. You have the Tunisian protest support and the Iranian protest support, and they were actually pretty focused on that for a long time, and then after the ‘Operation Payback’ it all seems to have sort of fallen apart. They’re literally idling with nothing productive to do.

And then there’s HBGary3, Aaron Barr4… He is the guy who says “I have a security product that I’m thinking of creating. And how about these guys? These guys think that they are really anonymous but I bet they’re not as anonymous as they think they are, I bet we could correlate their relationships and find out who they are”. I think the idea maybe was that it was going to be an educational exercise for everyone involved, and Anonymous actually kind of learned a little bit from this, because they were NOT truly anonymous – in fact, none of them were really anonymous, most of the were hanging all out in the open and sort of trusted in the use of loose handles and the power of numbers to sort of protect them from consequences. And unfortunately, that’s not how it goes. So I think we know what happened next. Anonymous say “Hey, you can’t screw with us and get away with it. This guy is gonna do evil and nefarious things with our information, so let’s go get him”. And everyone knows what happened there, so I won’t spend a lot of time on that. I think they got very drunk and giddy with power. If you are legitimately upset with somebody, I don’t think taking their email, the email of everyone they know, their friends’ private love letters and so forth, and smearing it all over the Internet is appropriate. So Hubris and I were watching the aftermath of this disaster.
Hubris (Director of Strategic Operations for Backtrace Security): Everyone, now, this is the cyber warfare part. I really can’t get into how I f..cked over Anonymous. I mean, look at this sh.t, f..k you guys, f..k you! And guess what – I’m up here right now because I trolled the f..k out of Anonymous, I took them down and I got to where I am right now. Thank you!.. (conflict in the audience)
a5h3r4h: Some of those people think “We’re Anonymous, so we’re going to be jackasses because nobody knows who we are”. And fortunately, not many of them are truly anonymous, and about the time we’re watching people in the IRC try to extort people at HBGary and say “Well, we won’t publish your private love letters if you give lots and lots of money to Bradley Manning1, donate the funds” – it’s extortion. We had some conversation about this and we say, you know, maybe going around on Facebook and looking at people talking to people on Facebook is not the best way to find them, but they’re findable, and maybe we can pick up where he left off, because we’re not afraid of consequences, because we’ve already tangled with these idiots. And we thought also it would be a good demonstration of why, you know, getting on the Internet and yelling about your right to privacy, and all the people that try to take your privacy away is a little hypocritical when you leave everything hanging out all over the Internet.
 We don’t have special equipment, we don’t use paid accounts or any of the tools that they traditionally use – no. Google, a few other database tools that are open to the public, and there’s quite a few things that you tend to notice in this group, and that is they use handles everywhere. Somebody is using a handle on AnonOps2 to talk about DDoS, they’re using the identical handle on Yelp to talk about the local Chinese restaurant that they check in at every week. They’re using it on Facebook where they’re also friends with their sisters, their brothers, their mother, their cousins and all the people in their local activist group.
We don’t have special equipment, we don’t use paid accounts or any of the tools that they traditionally use – no. Google, a few other database tools that are open to the public, and there’s quite a few things that you tend to notice in this group, and that is they use handles everywhere. Somebody is using a handle on AnonOps2 to talk about DDoS, they’re using the identical handle on Yelp to talk about the local Chinese restaurant that they check in at every week. They’re using it on Facebook where they’re also friends with their sisters, their brothers, their mother, their cousins and all the people in their local activist group.
Hubris: Oh, you should talk about the Tinychat they go into.
a5h3r4h: Yeah, if you wanna be anonymous, don’t get on an open Tinychat using your anonymous handle, especially when 4 different law enforcement agencies are looking for you.
The issue of duplicate handles is largely mythological, there’s not been a lot of duplication of handles, there’s been some. People talk about their location, people talk about what they have for dinner, they tell you what time it is where they are – we’re not going into IRC and looking for somebody to tell us what color their socks are. So Anons are like everyone else, they’re creatures of habit. People get attached to their identities, they get attached to their handles and use their handles everywhere they go – like I said, they’re using the handles in other social networking platforms where it makes it very easy to pinpoint who and where they are. Facebook accounts, YouTube accounts, Reddit accounts, Yelp accounts even – you know, review the local Chinese restaurant using your anonymous handle saying “I’m in Chicago, I like hot dogs”.
One of the things we’re not interested in is tracking down every single anonymous poster and finding them all. We’re not even really interested in doxing Anonymous in general, that was never the point. It’s not the point.

We have lots of conversations with lots of people on the IRC, we won’t get into specifics who we talk to. Lots and lots of people are perfectly willing to open up and give information to a complete stranger. This is why we’re doing it, this is why I’m doing it, this is where I used to hang out, these guys are my friends and so on and so forth. We were doing this despite the death threats, physical threats (see image) and whatever you can imagine, and the reason that we’re standing here today is because of the mob behavior, because if they don’t like what they’re hearing, they throw a fit and they come after you. You know, you’re gonna get harassed, you’re gonna get pictures of your children put on the Internet. This guy Gregg was part of the little mob that published pictures of my children on the Internet, that threatened to kidnap children from parents. Then he came to me personally and apologized and said “I was full of crap when they asked me to have you swatted”.
The thing is the Anonymous like the information to be free, but not when it’s their information. They want the privacy to harass other people, but they don’t want the spotlight to swing the other way. We were very upfront that we’ve been working with law enforcement – always very-very upfront.
Hubris: The reason why I got involved is they f..ked with the U.S. Marine Corps, and if you f..k with the f..king Marines, you f..k with me. America, f..k yeah!

a5h3r4h: …Which brings us to the next part, which was the ultimately retarded ‘Operation Manning’, which is where some half-wit person decided it would be a good idea to take retaliation against some allegations of mistreatment of Bradley Manning by digging out the personal information of all of the people that worked at Quantico1: their families, their children – the whole nine yards; post it on the Internet and harass the families of these Marines who are doing their jobs and do not have any say whatsoever and what happens to Bradley Manning or anybody else. And personally, I found that repugnant.
So this was followed by another incredibly stupid idea which is “Let’s DDoS Quantico and get the military mad at us”. And they did, despite the fact that CIDs2 at that point were out there actively looking for some people who were doxing Marines using a phonebook they acquired to their own active service.
 Regarding Anonymous’ personal action against us, they did what they could do. They tried figuring out who we were, they DDoSed our WordPress, they botted everything they thought was ours or might be ours or belonged to somebody who might know us or somebody we might have bought something from at the 7-Eleven. Their tricks are the same: harass, harass, harass – lots of harassment. The average people that face that kind of behavior don’t know what to do, when 500 people are calling you at home calling you names, stuff is showing up in your mailbox, people are calling your work and saying “Did you know so and so is a pedofile?” That’s not something that most people are used to dealing with, and it’s very intimidating to most people, it’s bully behavior, it’s obnoxious. We’re not really talking about destruction of property, but calling people at home and threatening to kill their children is not activism, you know. And this is one of the reasons that we came out here and put ourselves on the line to do this.
Regarding Anonymous’ personal action against us, they did what they could do. They tried figuring out who we were, they DDoSed our WordPress, they botted everything they thought was ours or might be ours or belonged to somebody who might know us or somebody we might have bought something from at the 7-Eleven. Their tricks are the same: harass, harass, harass – lots of harassment. The average people that face that kind of behavior don’t know what to do, when 500 people are calling you at home calling you names, stuff is showing up in your mailbox, people are calling your work and saying “Did you know so and so is a pedofile?” That’s not something that most people are used to dealing with, and it’s very intimidating to most people, it’s bully behavior, it’s obnoxious. We’re not really talking about destruction of property, but calling people at home and threatening to kill their children is not activism, you know. And this is one of the reasons that we came out here and put ourselves on the line to do this.

So there was a bit of a huffle-fuffle after this, and then things got quiet for a while. One of them closed his account and wandered away, some people went missing and things got pretty quiet on the IRC. Basically, nothing’s going on. In the intervening time, some of the folks that hang around on there who have other habitual misbehavior were fooling around in some database of a company beginning with ‘S’ and ending with ‘Y’ that we won’t talk about, found some things they thought were useful and tried to sell them and found out that they were generally worthless. So they were sitting on something they felt was a pretty major accomplishment and had nothing to do with it: can’t brag, can’t make money – we gotta do something, we gotta tell the world somehow. So they come up with this idea of LulzSec. So Kayla’s bored, Sabu has some political ambitions, Topiary has a list of media contacts – they say “The hell with it, let’s go”, you know. Now the game is {enter key}, they dump everything they got saved up, they got combing through the databases they’ve been collecting and selling for years and start looking for .gov addresses they can fiddle with. The PBS3 thing that had nothing to do with WikiLeaks – somebody came in and said “Hey, I found an SQLI4 on PBS – you guys want it?” – “Yeah, we want it!”. They didn’t even break in themselves, somebody else gave them the keys. So they got in there, they f..ked around, they spent about six weeks screwing with everybody. Then they got a little bit of an attack of conscience, all of a sudden everybody hated them, everybody was going “What are these assholes doing? They’re breaking into everything, they’re dumping people’s private information”.
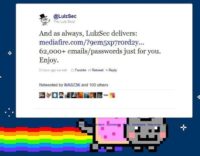
So they played this game for a little while, they were basically just combing through a lot of stuff they’ve already got and what people were giving them, and they were dumping it and having a good ol’ time, they were getting lots of attention – and then suddenly they realize that everybody hates them now. They are no longer popular in the world because they’re dumping people’s private information, credentials; they’re going on Twitter and going “Hey guys, here’s 65,000 passwords and information we got on innocent users of a site that had a security vulnerability these users were not aware of. Go see what you can do with it, go see if they got a PayPal account you can get into, get into their eBay, go on their Facebook and dump their boyfriend for them”. Anonymous had nothing to do with it, but the two core members of LulzSec did, and LulzSec was born because they wanted somewhere to dump and brag about an economically unfeasible job. They spent a lot of time getting into Sony, found nothing and they went bragging anyway. That’s what the genesis of LulzSec was. The people that broke into each big area are the same people that are members of the LulzSec, it’s the same people. So you can say they’re Anonymous, they’re not Anonymous, they’re sitting on AnonOps right now – Sabus work there on AnonOps, telling everyone “You wanna come see me? Come talk to me here”. It’s the same people, it’s the same crowd, it’s the same supporters, and they’ve been cheered on. If Anonymous and LulzSec are not the same people, why the hell are they still sitting there? Why haven’t they been escorted off the premises? They’ve all got ops on AnonOps, they’re all sitting in the IRC, they all have ops, they’ve not been disinvited, nobody said “We disavow these folks”, they’ve been welcome with open arms back into the fold. Everybody is not welcome with open arms, if you come in there with an opinion that’s contrary to one of the ten or fifteen people who have real power in that group, you will find yourself on the outskirts, or – in my experience – people will offer to dox you for free because they don’t like you. In fact, more than a dozen Anons have come to me and said “I don’t like this guy, here’s his dox”. When they don’t like you, they throw you under the bus.
I think that if Anonymous wants to be taken as a legitimate activist group, they need to excise the bullies, the jerks, the people who are dumping the personal information of thousands.
So, moving on…We start to get political again, and LulzSec realizes that nobody’s lulzing over their grandma’s email and password being spread over the Internet. They’re not thrilled with the private information of police officers and people who are risking their lives informing against Mexican cartels whose names have been splattered all over the Internet because they’re ‘snitching’.

Let’s move on to the bomb threat and let everyone see this (see image). It’s not fake, everyone can be Anonymous, right? This was re-tweeted by 75 other people who claimed to be members of Anonymous, so either there’s 75 disinformation agents out there trying to make you look bad, or 75 people thought that putting a bomb in the Orlando Airport was a good f..king idea to support food, not bombs. And yes, that’s what this was supposed to be in support of, and this guy is still out there, still tweeting insanity, and these folks are still re-tweeting everything that comes out of him. He’s not been asked to tone it down.
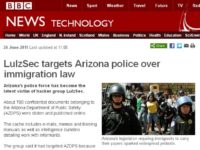
So, you know, the Arizona police weren’t terribly thrilled to find all their email and their names and addresses posted on a list that said ‘Off the pigs’ across the top. Now they decide to go back to politics but they’re not sure what they’re gonna do, because basically they’re just grabbing what they can grab, they’re dumping what they can dump and then they’re coming up with an excuse afterwards. And this isn’t activism, they’re not getting together and saying “What’s the issue du jour? What are we upset about and what can we do about it?”. They’re saying “We gripped this database. What political message can we put forward?” – literally, they’re having these conversations. So they basically are using every vulnerability that comes their way. People are coming in the IRC, going “Here, I found this – here’s access to the health records of health workers in Brazil”. No possible way they’ve got a problem with Brazilian health workers, but yet it gets dumped anyway, and the excuse is “Well, the Brazilian government are assholes. Everybody’s an asshole, let’s have a revolution. What are we gonna do? What kind of revolution? I don’t know, dump some more names”. At this point, we’re up to about half a million people’s credentials being spread over the Internet. If you stare too long in the abyss, the abyss looks into you. They’ve become the monsters that they were claiming to fight against. The same tactics that they decried in the Church of Scientology they apply to their own enemies – people who make them angry, people who cross them in the parking lot.
Basically what we got now is a sort of a formless mob that does what it feels like doing and just defies it after the fact. You get these guys in front of the media, and they’re boy scouts: “We love Bradley Manning, we’re all for free speech, we don’t like that Bradley Manning doesn’t have a blanket, we want to free the Tunisians”. In reality – “We’re frustrated there’s people we don’t like. We feel powerless, so let’s hurt some people to make ourselves feel better”.
Since we wrote this talk originally about three months ago, a lot of other things have come to life. We can’t really talk about a lot of what’s going on, but it looks like a lot of the movement behind the scenes began a long time ago that a lot of the things that they are couching is free speech activism is not in fact free speech activism; there are active members of the group that are looking to pull down critical infrastructure systems, they’re wanting to get into banks and drop passwords, credit card numbers, personal information.




























