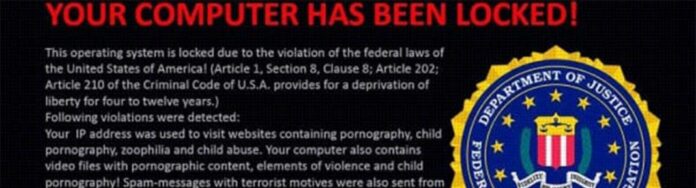
Content:
An aggressive ransomware campaign involving the so-called FBI MoneyPak virus (Reveton Trojan, Citadel, Trojan.Ransomlock.R) has been reportedly hitting computer users since 2012 and still appears to stick to a steady propagation pattern despite considerable international law enforcement effort to cease the black hat campaign behind it. On its official website, the Federal Bureau of Investigation strongly alerts users on this large-scale scam, providing basic precautions and urging victims to refrain from following cybercriminals’ recommendations reflected on the fake block page that the ransomware displays.
The malware prevalently targets Windows computers, although it was recently found to be affecting machines running Mac OS X as well. The fake FBI block screen states that the user’s PC is involved in illegal activity (such as copyright violations, viewing child pornography, etc.) and demands a fine ($100 or more) to be paid within the period of 48-72 hours for unblocking the system. The prompted payment option is Green Dot MoneyPak prepaid cards, the details on where to purchase those (Walmart, Ksmart, Walgreens, CVS Pharmacy, etc.) being provided on the spoof page itself.
If you are seeing an alleged FBI page identical or similar to the one above which demands you to pay a fine – do keep in mind this is a fake screen. The FBI does not practice this type of law enforcement. Therefore, instead of paying the “fine” it’s strongly recommended to eliminate the malicious software causing such activity.
FBI MoneyPak Virus: Variants and Screenshots
A retrospective insight into the advancement of this virus shows that there have been quite a few updates to its modus operandi and the external manifestation.
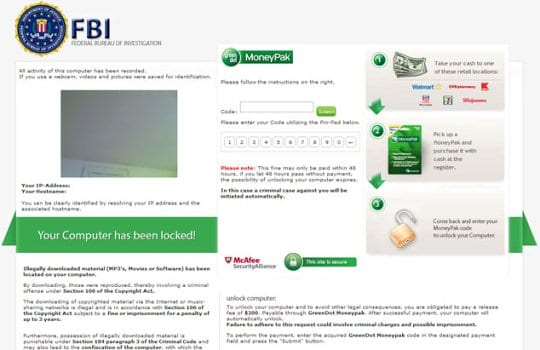
- The earliest known version (see screenshot below) proved to be the most widespread one out of the entire set. It demands a fine of $100 to unblock the computer and avoid possible prosecution for purported copyright violation and distribution of illegal content.
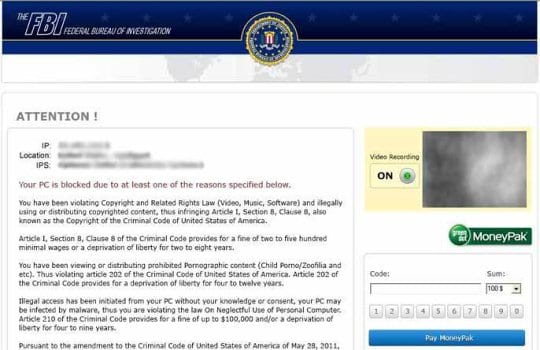
- The next update came out twice as “greedy” in terms of the fine amount, asking for $200. Also, compared to the preceding version, this one narrows the scope of alleged criminal offence, containing accusations of illegally downloaded material only (MP3’s, movies or software).
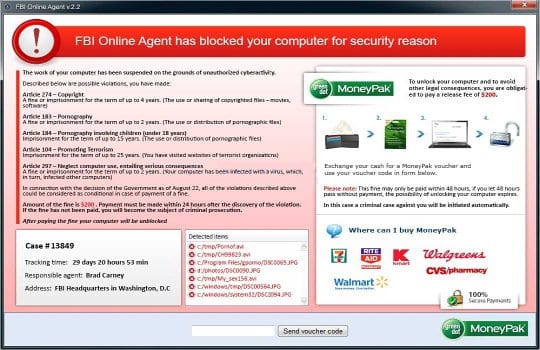
- The FBI Online Agent modification of the MoneyPak virus got somewhat more sophisticated, providing (for greater persuasiveness) even the FBI case number, responsible agent’s name, and listing the detected files that are stated to be evidence of unauthorized cyberactivity. This update attempts to extort $200 from the victims.
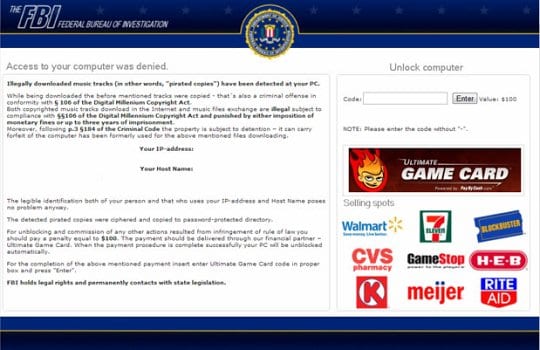
- One more version, the FBI Ultimate Game Card virus, incriminates violation of the Digital Millennium Copyright Act, namely illegally downloading music tracks “pirated copies”. This variation promises unlocking the computer for $100 which should be paid via Ultimate Game Card.
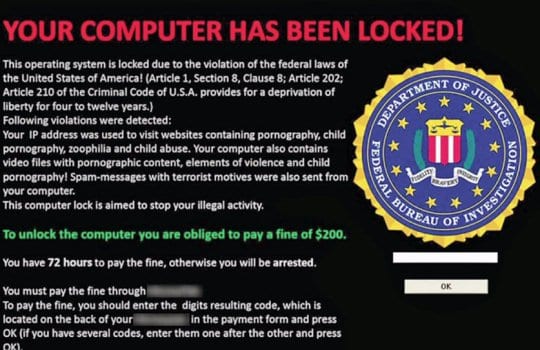
- Another modification, known as the Department of Justice virus (FBI Black Screen of Death virus), adds the alleged offence of sending “spam messages with terrorist motives”. The rest of the working algo remains basically unaltered: victims have 72 hours to pay a $200 fine.
- The so-called FBI Audio virus utilizes no graphics but a black screen – furthermore, it generates an audio message about system blocking, the accusations and the ways to pay the ransom.

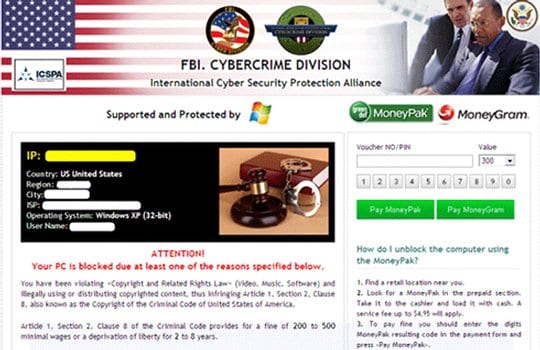
- The FBI Cybercrime Division virus is featuring a more diversified payment scheme, offering victims a choice between MoneyPak, MoneyGram, or PaySafeCard options. In addition, the ransom amount has grown here up to $300.
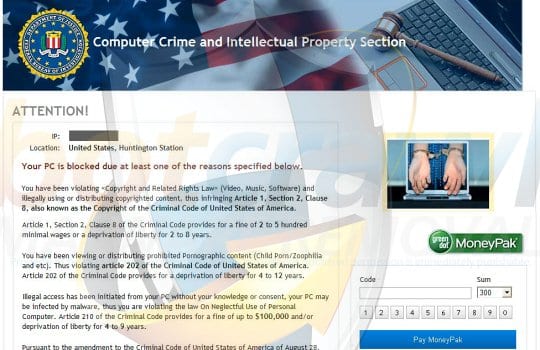
- The Computer Crime and Intellectual Property Section virus demand a fine of $300, accusing the user of violating “Copyright and Related Rights Law” and distributing copyrighted content.
FBI MoneyPak Virus: Symptoms / Malicious Activity
Now that we have reviewed the facts generally known about the FBI MoneyPak virus, let’s get more down-to-earth and list additional symptoms of the infection in terms of the hazardous influence it may have on the targeted computer.
- Interference with the activity of legitimate security software:
This malware might partially or completely disable antivirus / antimalware software running on the infected system, which allows it to persist inside the PC without being removed. In some cases, booting into Safe Mode or restoring the system to an earlier time point helps address these effects. - Private information harvesting:
As long as the FBI virus is operating inside a machine, it is known to be capable of collecting personally-identifiable information about the victim that is stored on the hard drive. The malware can as well take control of the webcam (if any) on the infected PC and record you.
FBI Moneypak Virus Removal
There are several ways to clean up an infected machine. The most efficient method for the FBI MoneyPak virus removal is by utilizing some of the top rated security software (see our rating) which have proven successful in combating the FBI scareware.
Ways to remove FBI MoneyPak Virus:
- FBI Ransomware removal using Security Software
- System Restore
- Manual Removal by Killing Malicious Processes
Note: If none of these methods work for you – you can’t enter to Safe Mode or the ransomware blocks all your actions – try to create bootable USB drive (read the guide).
FBI Ransomware Removal using Security Software
Below we will show how to remove the FBI virus with the help of Malwarebytes Anti-Malware. Due to peculiarities of this infection, automated removal should in some cases be combined with certain manual interference, which we will outline in this section as well. The benefit of using this method is twofold: it allows temporarily bypassing obstruction of the virus and enables accessing the Internet for downloading removal software. Here is what you need to do:
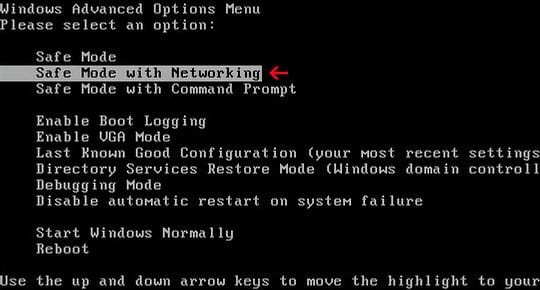
- Enter Safe Mode with Networking
- To enter Safe Mode with Networking, restart your machine and repeatedly hit or press and hold F8 key while the PC is booting. Once you see Windows Advanced Options Menu, use arrow keys on your keyboard to navigate to the Safe Mode with Networking item, and hit Enter.
- Use your mouse to open Start Menu, go to All Programs, then Startup folder. Locate “ctfmon” item and delete it. Please note the process name may be different yet similar.
- In case you are still unable to access the Internet after booting into Safe Mode with Networking, it’s advised to reset your Internet Explorer proxy settings:
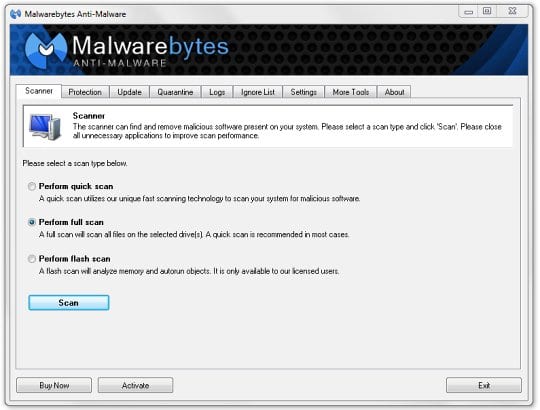
- Download and install Malwarebytes Anti-Malware (Pro or Free version).
- Open the application, locate the Scanner tab, select Perform full scan radio button, and click Scan
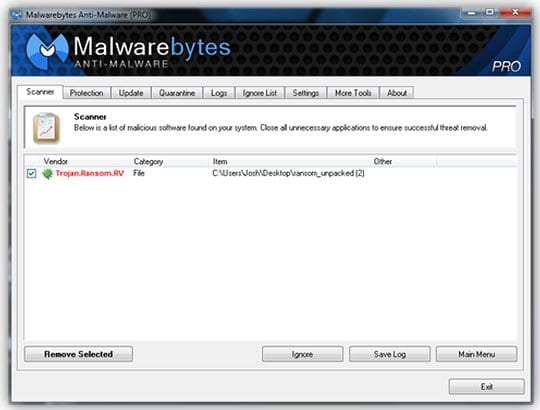
- Having scanned your system, Malwarebytes will display a report listing the detected Trojan. Select the spotted malicious item and hit Remove Selected in the bottom left-hand part of the GUI. The malware is now gone.
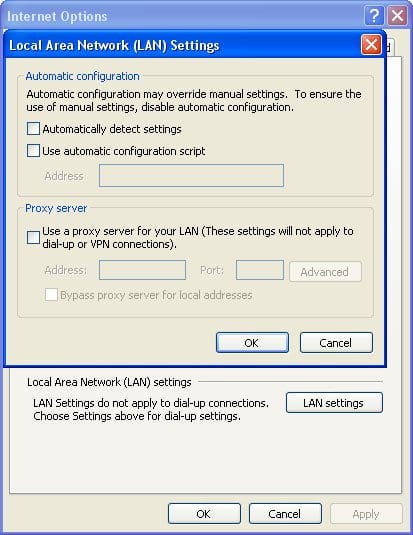
– When Internet Explorer is launched, go to Tools – Internet Options – Connections. Click LAN settings and uncheck the box next to Use a proxy server for your LAN item.
If you are unable to establish an Internet connection but your Desktop appears to be accessible in Safe Mode so that you can install Malwarebytes (download the installer using another clean computer, write it to a USB drive and install on the infected machine), then launch a virus scan and get the FBI MoneyPak threat removed.
System Restore
This option will enable you to recover your system to an earlier point, i.e. before the virus actually started affecting it. When restoring your OS, no saved personal files will be lost. Here is what needs to be done:
- Boot into Safe Mode with Command Prompt. To do this, press F8 key repeatedly while Windows is starting. This will bring up the Windows Advanced Options Menu, where you should use the arrow keys in order to navigate to Safe Mode with Command Prompt. Once this item is highlighted, hit Enter.
Please note you need to log into your PC as administrator.
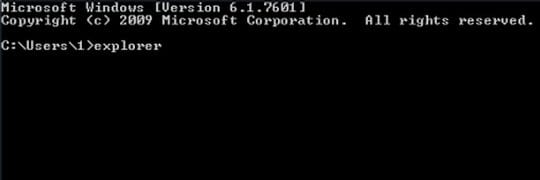
- As soon as the Command Prompt screen opens up, you need to type “explorer” (without quotes) and press Enter. This needs to be done within a few (2-3) seconds otherwise the FBI MoneyPak ransomware will prevent you from typing anything. So, be sure to do it fast.
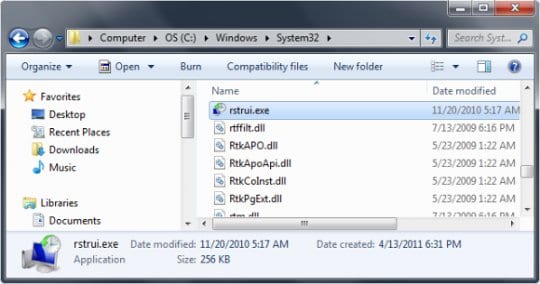
- In Windows Explorer that opened up, browse to the following location:
On Windows XP: C:\windows\system32\restore\rstrui.exe and hit Enter
On Windows Vista / 7: C:\windows\system32\rstrui.exe and hit Enter
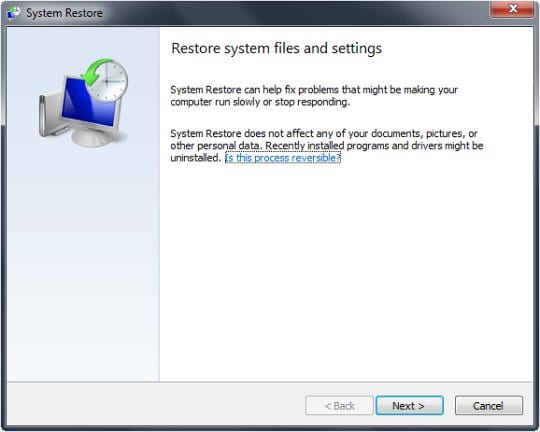
- Restore your system to an earlier point corresponding to the date before the ransomware hit it by following the steps within System Restore menu.
- Download, install, update and run Malwarebytes Anti-Malware. Get all the detected malware removed and restart your computer.
Manual Removal by Killing Malicious Processes
If you are an advanced user you can do it manually by performing multiple consecutive actions with your system. Although fairly burdensome and not always as effective as anticipated, performing removal of the FBI MoneyPak virus manually might do the trick as well. This method is intended to delete the bad processes and files in order to eradicate the infection. Downsides of this option may include difficulties locating the malicious files process names (they may vary) as well as severe interference of the malware with your attempts. Stick to the step-by-step guide as follows:
- Boot into Safe Mode or Safe Mode with Networking (see section above)
- Go to Start Menu in the bottom left-hand corner of the screen, type %appdata% in the Search box and hit Enter
- Browse to \Windows\Start Menu\Programs\Startup
- Find “ctfmon” (or similar-looking item) and delete it. This process is the one launching the virus at Windows startup. Save the changes
- Go back to Start Menu, type %userprofile% in the Search bar and hit Enter
- Proceed to Appdata\Local\Temp
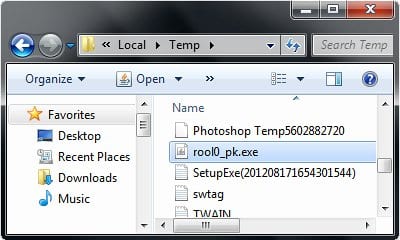
- Delete the following process: rool0_pk.exe (or similar)
- Remove the random-named file with .mof extension
- Remove V.class file
In different occurrences of the virus, it is known to have used a broad set of files and process names. Below is a complete listing of those. If spotted inside the directories above, these objects should be deleted:
%AppData%\Protector-[random].exe
%AppData%\Inspector-[random].exe
%AppData%\vsdsrv32.exe
%AppData%\result.db
%AppData%\jork_0_typ_col.exe
%Temp%\0_0u_l.exe
%StartupFolder%\wpbt0.dll
%StartupFolder%\ctfmon.lnk
%StartupFolder%\ch810.exe
WARNING.txt
V.class
cconf.txt.enc
tpl_0_c.exe
irb700.exe
dtresfflsceez.exe
tpl_0_c.exe
ch810.exe
0_0u_l.exe
• It’s now recommended to proceed to downloading and installing Malwarebytes or any other reliable antivirus software. Run a scan and get the detected malicious objects removed (see Security Software cleanup instruction above).
If none of these methods work
Finally, if you are unable to enter to any type of Safe Mode or the ransomware blocks all your actions – proceed to our guide on How to remove the FBI MoneyPak Virus if Safe Mode doesn’t work.































Hi! I was recently surprised with this virus. When it first appeared, before I did anything at all. I proceeded to close all other windows until only the warning page remained. I then turned off the laptop at the main power button, not the recommended shutdown process.
I let it sit for 5 minutes, then rebooted. The FBI warning did not return.
Two days later, I received notice that my antivirus updates could not be performed due to expiration. But I renewed for a year within the last 3 months. Is there a connection?
I have an Acer laptop protected with WebSweeper (Sophos through BestBuy). Geek squad had me uninstall then reinstall. No change – can’t update definitions for antivirus. I called Best Buy – they say I am protected and that there is a known tech issue and are working on a work around.
Did my antivirus kill the virus — or is the virus there, unknown to me? How can I tell/find out.
The warning said my files are locked – but I have not had any problems with any of my files.
John,
To check whether the FBI MoneyPak virus is gone, I recommend you run a scan with Malwarebytes Anti-Malware. You can download its free version via the link provided in this article, install it and have your system scanned – then you’ll know for sure.
Thanks
I powered down, rebooted.
Logged on to different user (with admin)
Ran Malwarebytes quick scan. Removed six objects.
Restored system to yesterday successfully.
Did normal reboot and logged on as user with the problem.
Ran Malwarebytes full scan.
thank u for posting this i just got this message today