Content:
Victim geolocation being today’s big trend in the cybercrime world, the ransomware version attacking Australian users came out in summer 2013. Similarly to its U.S.-based (the FBI Moneypak virus) and British counterparts (PCeU, Metropolitan British Police infections), the Australian Federal Police (AFP) ransom malware has been spreading by leveraging web exploit kits, primarily BlackHole, and botnet threats such as Trend DNSChanger. What this distribution routine means is that the malicious code proper, known as Reveton, gets dropped on a target PC after the system has been exploited without user consent and knowledge. The main trigger facilitating the contamination is unpatched or out-of-date software on one’s machine which yields to vulnerabilities being taken advantage of by the fraudsters.
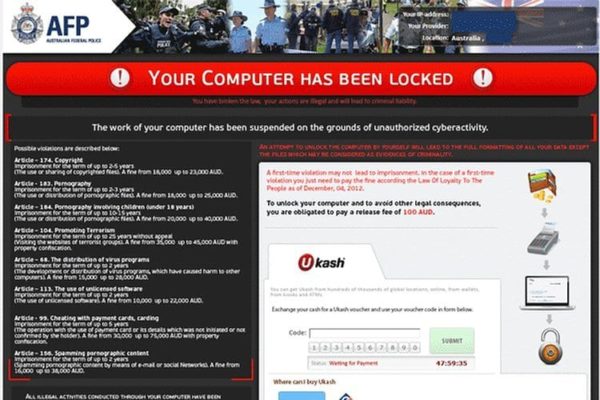
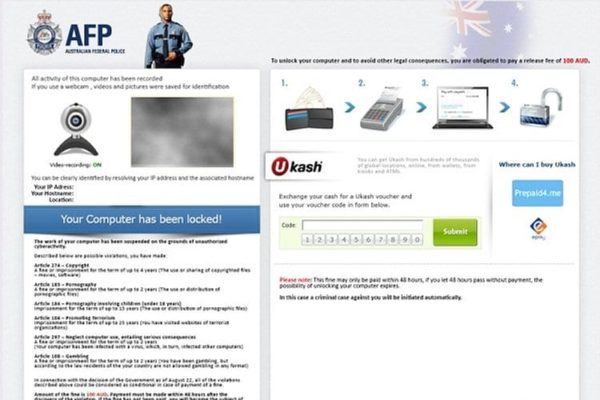
The main externally manifested attribute of the AFP virus is a lock screen, purportedly from the Australian Federal Police as a law enforcement agency, which completely disables logging into Windows. It reads “Your computer has been locked”, enumerating the causes that might have led to this blocking. Among those are Copyright violations, pornography distribution, promoting terrorism, spreading virus programs, the use of unlicensed software, cheating with payment cards, spamming, etc. At this point it’s important to acknowledge that such tactics are used for the sole purpose of intimidating the victim, and by no means reflect the reality. Moreover, this is definitely not a message coming from the Australian Federal Police – legitimate institutions do not employ methods like these.
Why would the criminals intimidate the user? Because what they want is money. As grounds for unlocking Windows, the AFP ransom infection extorts a monetary fine amounting to 100AUD. According to the block page, this sum needs to be paid via Ukash, i.e. a code from a prepaid card should be submitted through the embedded field within 48 hours otherwise the possibility of unlocking the computer expires.
Before we proceed, it should be emphasized that paying this ransom will not cause the virus to go away. It might lead to unlocking the PC, but as long as the Reveton Trojan stays inside, chances are you will be hit by another ransomware version or other type of malware later on, or your private information will be compromised. In this article we will show you how to get rid of the AFP virus without having to buy the Ukash card and without further worries that your system will stay at risk.
Australian Federal Police virus: variants and screenshots
The block pages generated by the Australian Federal Police ransomware have got a few common attributes, although they do differ from each other graphically. Both the older and newer versions are based on the exact same malicious code and share the following common traits: field displaying streaming video from the victim’s webcam, large payment section, and very similar excerpts from the legal articles that have been allegedly breached. The visual part has been updated a number of times. This is all reflected on the screenshots of the AFP virus lock pages below:
AFP ransomware: symptoms and dangers
- Phony lock screen:
This is the most apparent sign of the infection: before Windows gets the chance to load, the virus ceases the process and hijacks the screen with one of the pages shown in the previous section. This results in disabling access to anything installed or stored on your computer, including your files, programs, antivirus software, etc. - Webcam control:
For the purpose of greater persuasiveness of their technique, the scammers have integrated webcam access into the malware’s fraudulent arsenal. Consequently, the lock screen contains a section where the attacked users see themselves. This is obviously expected to focus the victim’s attention on the supposed fact that they are being constantly watched by the law enforcement authorities. - Promoting other malware:
Reveton is known to be capable of communicating with the external malicious servers controlled by the cybercriminals who run this whole campaign. As a result, your PC may become affected by other threats launched at you, not to mention that it may likely turn into a bot serving for spam or malware distribution activities.
Australian Federal Police virus removal
Due to peculiarities of this malware, standard cleanup through launching security software installed on the affected computer is not applicable. Likewise, manual removal is considerably aggravated because of inability to access system directories where the virus embeds its components.
Having thoroughly analyzed this malware, we came up with a number of removal methods that proved to work in terms of complete extermination of the AFP Ukash virus.
Australian Federal Police virus removal using HitmanPro.Kickstart
For carrying out this removal procedure, you will need a USB drive to further launch the cleanup software from. Please note that all the data on this USB drive will be lost, so make sure you back it up before proceeding.
- Download HitmanPro software to a computer that is not affected by the virus and save it to your Desktop. Before performing the download, be sure to select the version according to the bit-type of your Windows operating system (32- or 64-bit).
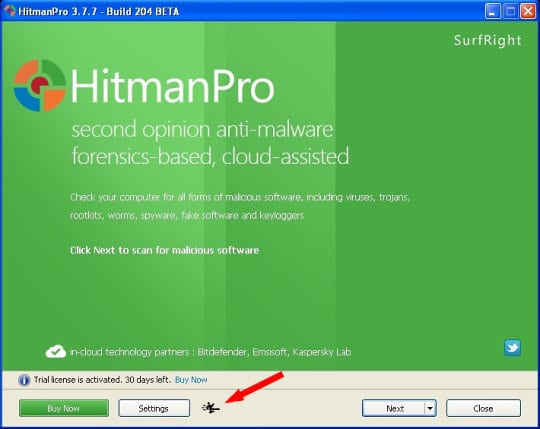
- Plug in the USB drive that you are going to use for installing HitmanPro.Kickstart. Having inserted the thumb drive, double-click on the HitmanPro icon on your Desktop. The program’s main Window will appear. Please click on the kicker button as indicated by the red arrow on the screenshot below.
-
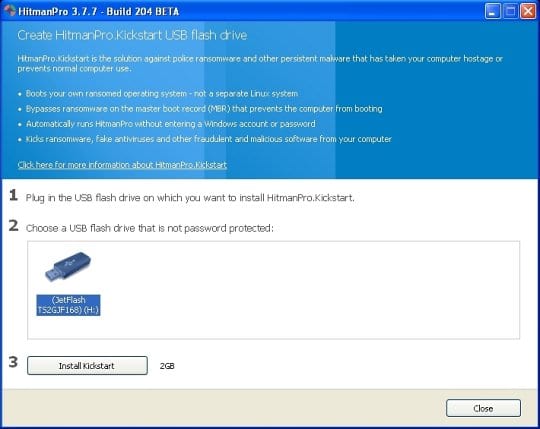
You will now see a window that will guide you all the way through creating the HitmanPro.Kickstart USB flash drive. Select the right USB drive by clicking on it in the corresponding field, and click the Install Kickstart button.
The software will ask you whether the USB drive contains any important files (all of them will be erased). If there are none, click Yes on the alert. This will automatically initiate the install process. When it completes, click Close button. - Remove the USB drive and insert it into the computer infected with the the AFP ransom virus.
-
When it is inserted, turn off the infested PC and switch it back on. As the computer is beginning launch, take a good look at the boot screen to find the key that should be pressed for accessing the Boot Menu or BIOS Setup. Please note that these keys may be different on different computer models. For entering the Boot Menu, those are mainly F10, F11, F12 or Esc buttons. The ones for BIOS Setup are usually Del or F2.
Having determined the appropriate key for Boot Menu access, reboot and start hitting that key repeatedly as the PC is beginning to load. When in the Boot Menu, use its prompts to select the drive you want to boot your computer from, i.e. USB drive. -
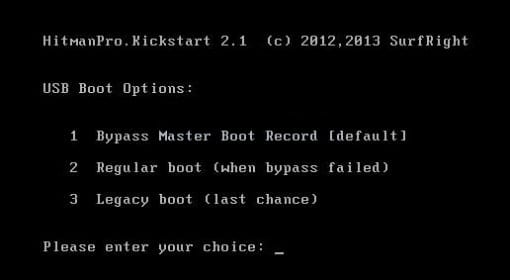
Now your PC will boot from the USB drive and load the HitmanPro.Kickstart saved to the memory stick. You will see a screen requesting you to choose USB Boot Options.
You should press 1 as your choice. Doing so will be followed by Windows starting to load. -
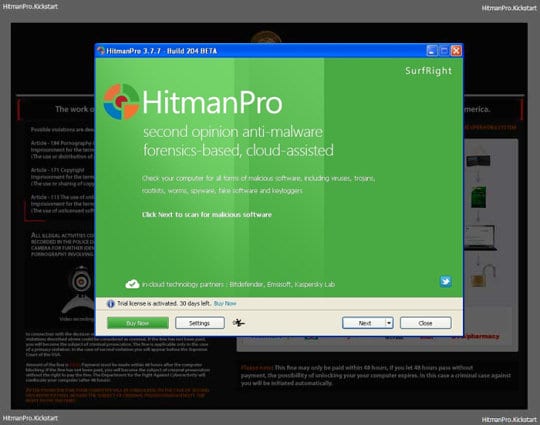
Right after Windows launches, the fake Royal Canadian Mounted Police block screen will appear as it did before, however in 15-20 seconds the HitmanPro main console will pop up on top of that.
Please click Next on the program’s GUI. -
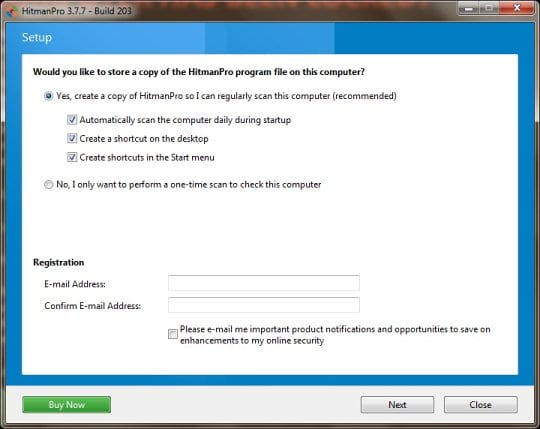
On HitmanPro’s setup screen that appears, we recommend leaving the default installation settings as shown on the following screenshot:
Please click Next.

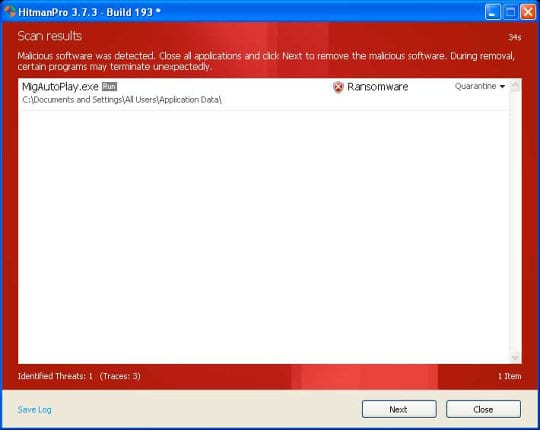
- SurfRight HitmanPro will now start a virus scan. Having completed the scan, the utility will come up with a report listing the detected threats.
- To get the spotted infections eliminated from your system, click Next. After the removal routine is complete, choose the Reboot option on the subsequent screen. Your computer will restart as usual. The Australian Federal Police Ukash virus is no longer affecting your system. If you are not certain your current antivirus can prevent such threats from infiltrating your system in the future, you might want to consider upgrading to HitmanPro licensed version.
Australian Federal Police virus removal using System Restore
This cleanup method allows restoring your operating system to the time period when it was not contaminated with the AFP ransomware. This procedure will not lead to loss of any files. To perform system restore, please stick to the following steps:
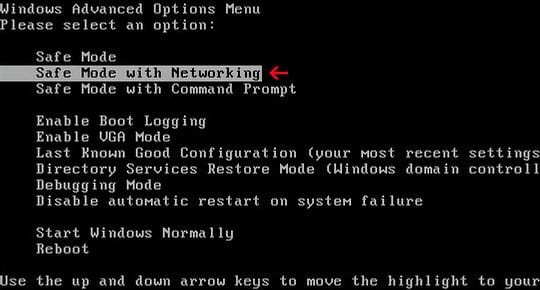
- When the infected computer is starting to load, tap F8 on your keyboard repeatedly to open up Windows Advanced Options Menu. When on this screen, use the arrow keys to highlight Safe Mode with Command Prompt, and hit Enter.
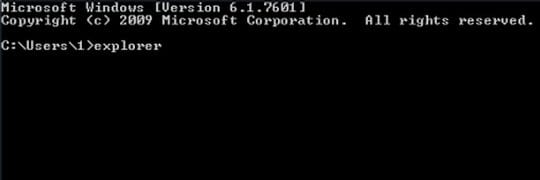
- Once the Command Prompt screen opens, type explorer and press Enter. Be advised this needs to be done quickly (within 2-3 seconds) or else the malware will not allow you to type anymore and you will have to start the process over.
- In Windows Explorer, browse to the following path:
On Windows XP: C:\windows\system32\restore\rstrui.exe and hit Enter
On Windows Vista / 7: C:\windows\system32\rstrui.exe and hit Enter
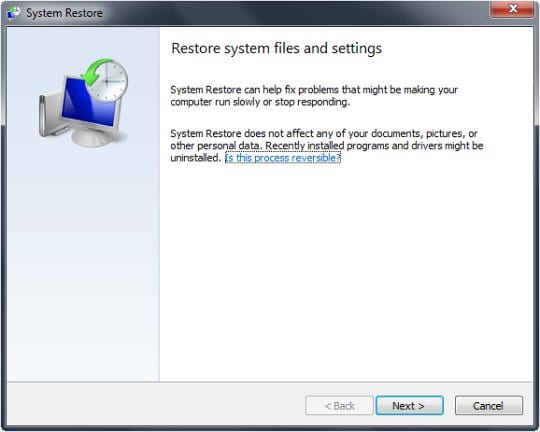
- Using the System Restore prompts, get your system restored to the date when it was unaffected by the ransomware virus.
Download, install and run reliable security software to get effective protection from cyber threats further on.

Besides using efficient antivirus or antispyware, in order to prevent web exploit kits from delivering Reveton or similar malicious software on to your computer in the future, be sure to install Java updates on a regular basis and get other software patched whenever possible.