Content:
TrueCrypt 7.1a is one of the simplest, best organized and most efficient encryption utilities we have come across. It installs in a matter of seconds, offers an optimal range of services, and takes a reasonable amount of time to perform the complex tasks it’s designed for. Though the app’s graphical representation, as well as the vendor’s website, is far from today’s high-end trends across the industry, it is appealing as an essentially reliable and robust tool for maintaining privacy the right way. Plus, it’s freeware.
The core idea of TrueCrypt 7.1a is all about protecting private files from unauthorized access; the rest is technicalities. In case you’re unfamiliar with encryption software as such, this application will definitely add a couple of new terms to your vocabulary, concurrently giving you great guidance on such notions as data volumes, (non-)system partition drives, volume mounting / dismounting, keyfiles, security tokens, smart cards, and of course encryption and hash algorithms. All of these are the things computer privacy is inalienably associated with.
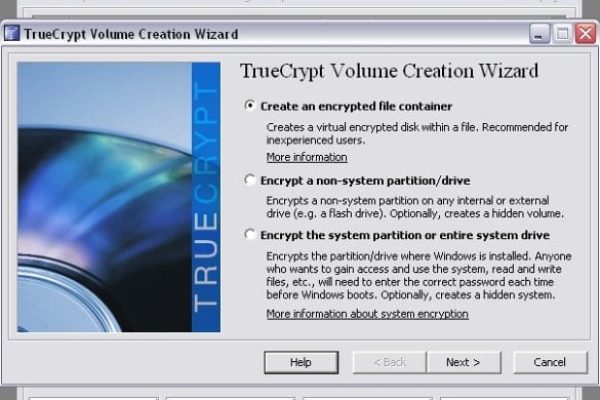
In a nutshell, TrueCrypt enables creating secure encrypted volumes on virtual disks and USB memory sticks; allows encrypting full partitions or even the entire system drive; and provides the option of making the volumes hidden if desired.
System Requirements
Operating System:
- Windows 2000 SP4 / Windows Server 2003&2008 / Windows XP / Windows Vista / Windows 7
- Mac OS X: 10.4 Tiger / 10.5 Leopard / 10.6 Snow Leopard (32-bit) / 10.7 Lion (32- and 64-bit)
- Linux (32- and 64-bit versions, kernel 2.6)
Usability
Installing this product is all simplicity. The 2.7 MB stub installer does the job flawlessly, pulling in the latest version and barely requiring user interaction. The only thing you are to do at this point is pick the Wizard mode out of the default ‘Install’ and ‘Extract’ options. The latter applies to the case where you are going to use TrueCrypt in portable mode, so this one does not actually install anything on the system. Should you further need to encrypt the system partition or system drive, do not select this one. During the install, you get the question about the vendor’s business model answered: on the final stage of the setup there’s a request to consider making a donation. This is completely optional and unobtrusive, so we’re pretty sure tactic like that works wonders.
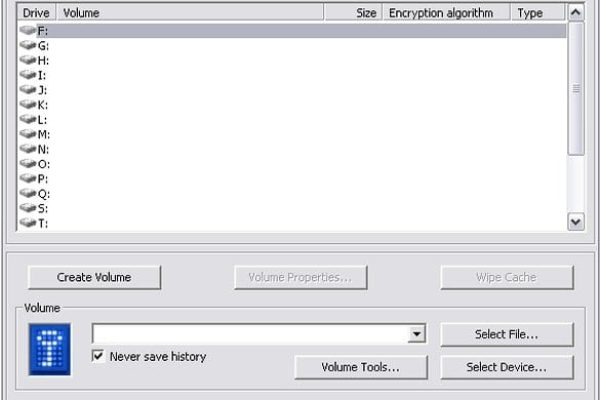
Looking at this app’s interface, you kind of find yourself years back – due to ultimately plain design and a minimum of graphical components as we know them from most of the present-day utilities. This old-style appearance has its virtues though: it’s restrained in a good way, and you find things with ease. Moreover, the zero cost is a heck of a compensation. The main options that bear the greater part of the functional value are right there on the main screen: the list of virtual drives to select from; buttons for creating, mounting and dismounting a volume; as well as tools, settings, help, etc.
To avoid misunderstandings during first experience with the program, users are advised to review the Beginner’s Tutorial providing step-by-step tips on the essentials: how to create a volume, mount / dismount it, use encrypted partition, and the like. Overall, there is nothing complicated in performing on-the-fly encryption with TrueCrypt 7.1a after you study the corresponding guides, although this is essentially a sophisticated procedure associated with military-grade authentication and the use of complex algos. There are some things to keep in mind when encrypting stuff with this program. For instance, whereas the files mounted to a selected drive behave just like regular ones, you need to make sure you remember your password before dismounting the volume, because a forgotten password means serious trouble for further access to those files – in other words, mounting them again simply won’t go through. So, proper password management is one of the things to not neglect in TrueCrypt use scenario.
Compared with other encryption utilities we have tested, TrueCrypt 7.1a is pretty complex for the average person to use. Therefore, once again, getting started with this product takes time and some effort, so before performing the common tasks be sure to thoroughly study the product materials to do everything the right way and avoid making irreversible mistakes.
Neither the setup nor further use of this product turned out a burden for our lab machine in terms of the memory or time consumed. The app is feather-light and it really stays on the background without disturbing you at all. Time-wise, it all depends on the size of the container or partition you are attempting to encrypt, but we assure you this process will not cause a wait beyond what you expect from an application of this kind.
Features
TrueCrypt 7.1a has got all it takes to make file encryption work the way it should. It is finely balanced, neither lacking any of the core features nor providing an excess of them. Now, some details.
- On-the-fly encryption / decryption means that files get automatically encrypted right before they are saved, and decrypted right after they are loaded when you copy them to or from a mounted volume. More importantly, the decrypted data is not saved to a disk – instead, it gets stored temporarily in RAM, loading in portions so that memory won’t get over-consumed.
- Instant File or Folder Locking – this feature means that regardless of the item you are going to encrypt (be it an individual file or a directory with all of its contents), you are just a click away from the goal, once you’ve located the right object. Indeed, doing this with this software is made as simple as ABC.
- TrueCrypt allows mounting the containers to a large number of virtual drives (there are 20 of them), so you shouldn’t lack room for maneuver. The volume size can be random – from kilobytes to gigabytes – depending on free space on the corresponding system drive. It’s worth mentioning that encrypted volumes may be hidden if needed.
- Strong encryption algorithms – this basically translates to securely stored data. The software being reviewed lets you choose from 8 encryption algos, 3 of them being standalone, and the other 5 – cascades, i.e. blends of the former in different configurations. Here is the list of available algorithms: AES, Serpent, Twofish, AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES, and Twofish-Serpent. This is quite an extensive set enabling military-grade on-the-fly encryption.
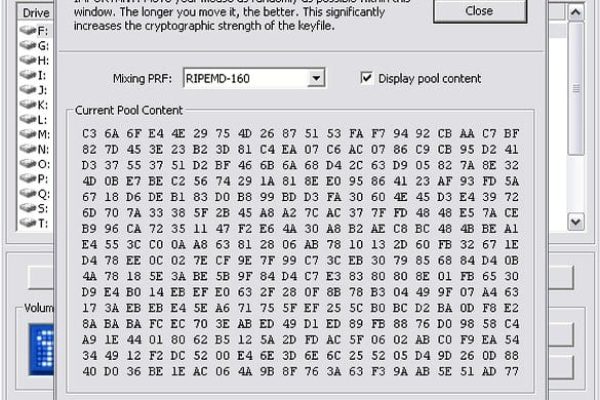
- Hash algorithms are applied as pseudorandom mixing functions by the app’s Random Number Generator to assure enhanced volume access security. TrueCrypt 7.1a offers 3 of them: RIPEMD-160, SHA-512, and Whirlpool. The ‘Encryption Options’ dialog box conveniently contains a link to learn more about these algorithms on www.truecrypt.org. These algos are also involved in keyfile generating.
- To further reinforce intactness of your data, TrueCrypt allows using keyfiles. The content of such files is combined with a password to deliver additional protection against brute-force attacks, rendering unauthorized access chances very faint. The use of keyfiles also enables shared access to encrypted volumes.
- The use of smart cards and security tokens is another supplementary method included in TrueCrypt authentication model. There are some requirements to such devices though, apart from the presence of the right keyfile: they must conform to PKCS #11 (v2.0 or later) crypto standard. Again, this way you get yet more security layers added, especially if the smart card or token is protected by PIN or its own password.
- Encrypting a partition or device is a remarkable option making it possible to secure entire system drives and external devices (e.g. USB memory). Naturally, encrypting system disks is time-consuming, solely due to their large size.
- Furthermore, the program allows creating a hidden operating system, which is a system installed to a hidden TrueCrypt volume – therefore, no one can possibly find out it’s there. This is the OS where you can store all sensitive data. In the meanwhile, you may use the regular operating system (so-called decoy OS) to demonstrate to anyone interested, e.g. to ill-minded individuals threatening you and the like. Just make sure no private files are stored on the latter.
Efficiency
When it comes to the way TrueCrypt 7.1a does its job, frankly, there’s barely anything that hints at the fact it’s freeware. Reliability in this case is metered by the technology this software utilizes to keep your sensitive data secured. By this criterion, the application is beyond all praise: it uses the encryption and hashing algorithms that usually tend to be called ‘military-grade’. Even more, availability of additional privacy-enhancement options, such as the use of keyfiles, smart cards and security tokens, makes the utility an extremely hard nut to crack. Our test showed that the tasks TrueCrypt declares to fulfill are taken care of nearly impeccably. Generally, we are pretty impressed with this degree of effectiveness.
Help & Support
The built-in Help menu contains an extensive 150-page User Guide providing in-depth details on nearly every aspect of the product’s features and the technologies leveraged. Additionally, it links to the Beginner’s Tutorial and frequently asked questions. It would be fair to admit that self-help appears to be the vendor’s primary focus; in the meanwhile, the information is comprehensive and complete. The contact section is not quite what it sounds like though, being more of an interactive system with multiple choices, where in the end you don’t really get to get in touch with tech support. Instead, the website only provides recommendations on where to go and what might be the best way of solving the issue, so it’s more like an advisory, not a contacting option. TrueCrypt forums are more helpful – they’re lively and might well give you guidance on general inquiries and problems. Live chat and telephone support are not among the options, which is understandable considering that this is a free utility, but still kind of distressing.
+/- (Pros/Cons)
- Zero price
- Very low system performance impact
- Reliable on-the-fly encryption
- Use of smart cards and tokens as an option
- Plenty of encryption and hashing algorithms
- Primitive design
- Restricted tech support opportunities
- Knowledge of product basics required prior to use
- Windows 8 currently not supported
Bottom line
Despite the old-school GUI and lack of direct support, we enjoyed the way TrueCrypt 7.1a works for the most part. Once again, it is free software, and while some might expect poor functionality – that’s not the case. Not only does the utility encrypt individual files with strong algorithms, it also delivers the optional multi-layered authentication tools and allows encrypting whole partitions, system drives, and items stored on removable media, not to mention the unique ‘hidden operating system’ feature. Generally, TrueCrypt 7.1a effectively secures sensitive data by utilizing military-grade crypto algorithms.