
Presenting at DEF CON, Ryan Lackey and Marc Rogers, security researchers at CloudFlare, highlight various methods and helpful tools to avoid OPSEC failures.

Ryan Lackey: Hello everyone! I’m Ryan Lackey, and this is Marc Rogers. Unfortunately, our third co-speaker The Grugq is not here, as you can tell. I think he had some serious travel difficulties, much more than were anticipated, and there are some sketchy details, so I’m not really too filled in on it. But we have worked with him on this project for the last year and I have been in contact with him.
I actually work for CloudFlare, a company that does CDN, DDoS stuff. Marc works for Lookout, working on this as a sort of side project, fun thing. And The Grugq is an OPSEC consultant and has worked on a variety of cool projects.
Marc Rogers: I’m also the Head of Security here at DEF CON, so I apologize in advance for shouting at all of you.

Ryan Lackey: We are excited to be here and show off this cool stuff that we’re working on (see right-hand image). We are going to go over why you want to hide. We are using software to let you hide in network traffic. We are going to go over principles of operational security, which is really The Grugq’s main area of study, and he is pretty much the most interesting person in the field, taking how larger organizations learn about OPSEC and applying that OPSEC to the hacker community and to the activist community and also to other groups that don’t themselves have a huge intelligence potential. We are going to go over some serious OPSEC fails and what happens to people, and then how technical countermeasures are used against people; existing tools, countermeasures to those tools. And then we are going to bring in the exciting new technology, the travel routers, and how to use these things for safety.

So, just to start, why would you actually ever want to hide? You are just doing normal stuff, we’re not really talking about helping people hide from doing all sorts of bad stuff – this is in your normal life. There’re a lot of reasons why you would actually want to hide (see left-hand image). A lot of this has become much more clear in the last couple of years, especially post-Snowden, but even before that it was fairly widely understood, at least within this community. Part of it is to avoid sort of a global dragnet. You want to make sure that if somebody is monitoring all the communications, you are not sort of swept up in that. Because the problem is, while you might be doing nothing at all wrong, somebody next to you, somebody you have a phone call from, somebody in any loosely connected way to you might do something – and due to how software works and scoring that plus another interaction plus something else, depending on where you live, could actually get you droned. Not just on a watch list, but signature strike or something like that. Really, it’s just none of your business. Why would you want to be monitored? It doesn’t benefit you in any way, so if you can avoid it you should possibly do it.
Marc Rogers: Or maybe you are doing something that you don’t want people to watch. Maybe it’s something illegal, maybe it’s just something that you want to ensure that you maintain OPSEC for your project, you want to maintain OPSEC for your company. People are actively trying to steal secrets, both for national security reasons and because they want to steal your secrets.
Ryan Lackey: And the crazy thing is people that were in various illegal activities knew this, people that were in the hacker community knew this. But now there’s a whole new realm of people that really need to worry about this kind of thing that you would never think of as spies or hackers or anything else. Journalists, people involved in any sort of activism in any sort of environment where their adversaries are well-resourced – these people have this as a serious concern now. And it’s kind of crazy and it’s sort of an asymmetric problem, where there are people that have problems now and don’t have the resources to defend themselves.
Marc Rogers: There are two very important takeaways that you can get from all of this. Number one, OPSEC is not new. We like to talk about OPSEC and information security as if this were a new thing that we have discovered. The reality is OPSEC is as old as mankind, and many of the techniques to protect OPSEC are just as old.
And the other one is that the tools and stuff we are talking about – there’s no rocket science here. We are talking about using existing tools, existing techniques. The difference is we’re packaging it together and showing you how you can use it in a seamless way so that you don’t have to think about it and you avoid that number one problem – human error.

Ryan Lackey: So, The Grugq has sort of distilled OPSEC into some basic principles, which are listed here (see right-hand image). We are not going to really go over them, but he has done this many-many times. Biggie Smalls actually had a great song about how drug dealers apply OPSEC to selling crack. It’s been analyzed by law professors and everyone else as pretty good actionable advice for people that are involved in any sort of activity. And it’s not just crack dealers that need this these days; it’s people that are involved in complaining about spying systems being installed to their local port system in Oakland, or people that are worried about companies and potentially boycotting them due to human rights abuses or, really, anything. So it’s a pretty universal problem that a lot of people have.

But, on the other hand, what happens when OPSEC goes wrong? This is a photo from Somalia (see left-hand image), where the U.S. Marines were going in during the Operation Gothic Serpent to intervene and try to distribute aid and food and stuff and get rid of warlords. They did an opposed beach landing, which they hadn’t really done since Normandy in World War II. It was a big opposed beach landing. Unfortunately, the media knew about it in advance. So they were doing this landing with a bunch of little rubber boats and everything else, with a bunch of journalists sitting there with cameras waiting for them on the beach, putting the thing live on satellite TV that all the warlords saw. That’s sort of an OPSEC failure. Nobody got hurt as a result of that directly, but it could definitely have gotten a lot worse.
Then we’ve got other examples of some basic OPSEC failures bringing down an organization that many people think was sort of a libertarian commercial market.

Marc Rogers: When you look at many of the big bust issues that have happened recently, you will see that OPSEC failures behind them are basic, really-really basic (see right-hand image). Take, for example, Silk Road, the largest and most successful online contraband bazaar: over 957,000 user accounts, 9.5 Million Bitcoins ($1.2 Billion in transactions). The guy behind it, “allegedly” Ross Ulbricht, used his personal Gmail when setting up an account that he then used as the administrator, the “Altoid” account. He then used that “Altoid” account to post jobs advertising for people to come in and do coding for Silk Road and related projects. He also advertised Silk Road using the same account. He later on kind of caught up to this and he changed his Gmail to frosty@frosty.com. But once you’ve opened the door and you left information out there, the Internet doesn’t forget. It all becomes fruit of the poisonous tree, and everything you do from that point onwards is tainted.

Next one, Sabu and LulzSec – even worse (see left-hand image). Sabu, skilled hacker, knew what he was doing, used Tor all the time, except every now and then he would forget and he would log into IRC. Just once is enough in this day and age. It used to be that you could get away with one mistake, but now in this world where it’s possible for people to wholesale, capture and store, just in case there’s something interesting, that one mistake will hang you. Perhaps even worse than that, he also used his home address to use stolen credit cards, to buy car parts and had them shipped to his home address. These kinds of OPSEC failures – really obvious. Not surprising he got busted.

Mark Karpeles – allegedly, we don’t know exactly what’s going on, but what we do know is that around the time that Mark Karpeles and MtGox had completely run out of money, there were wallets that he had used previously when proving that MtGox still had liquidity and had moved money into (see right-hand image). Those accounts were still around and active, and so people started looking at them. And guess what, you follow the chain and look to them – they still had money in them, way more money than he allegedly had. And, unsurprisingly, when people started talking about it, he miraculously found another pile of Bitcoins that he “didn’t know about”.

Ryan Lackey: So, what are the common mistakes and vulnerabilities here? These are just several examples (see right-hand image), there’s a bunch more. It’s always insider threat, which is probably the most insidious and difficult to resolve, also the easiest to find in almost any organization. It’s pretty universal. There are people making mistakes, human error; and then data leakage – people using the wrong channels for the wrong kind of data. There are more serious technical threats. You’ve got people either seizing your hardware or getting temporary access to your hardware, doing live or cold analysis on it. You’ve got people doing either network or RF monitoring of your system. You’ve got people tearing down remote servers. Also you’ve got active tampering with things.
These are pretty serious threats, and maybe it’s not worth trying to mitigate the most difficult thing – start with the easy things. And then, of course, there’s the financial and physical audit trails left by almost every system people interact with.
Marc Rogers: One of the probably most important points about this is you cannot take care of everything, you can’t think about everything. But if you can automatically catch the low-hanging fruit and protect a certain segment of your stuff that you don’t have to think about, you can then focus the rest of your resources on the more complex problems.

Ryan Lackey: Network forensics is pretty widely understood, metadata of course being the target of almost everything (see right-hand image). Metadata is so much easier to process from the attacker side. They don’t need to bother translating it into the native language, they don’t need to normalize the data. It’s already there, it’s automated, it’s trusted, it’s reliable, and it’s the easiest thing to go after. We have seen a lot of recent attacks where metadata, really, was the focus of the attack.
Marc Rogers: And it is very much the low-hanging fruit. As we saw from a talk that was given at H.O.P.E., even data that you think is encrypted, such as some of your personal information on the iPhone, is not; because when the device is running, certain segments of the device are unencrypted so that the device can operate and receive messages. That means it’s accessible, and in fact the only time your iPhone is completely secure is when it’s powered off.

Ryan Lackey: There’s all this kind of data you would attack from a desktop system (see left-hand image), any sort of server that you are attacking – it’s all pretty clear. And on cellphones, which are basically computers, you have fairly similar kinds of targets (see right-hand image).

They have some additional threat vectors because they connect to telco networks directly, and in fact they are with you at all times, they are taken into secure spaces, taken out of secure spaces, taken back into secure spaces and taken out over and over again. It’s a more interesting threat, but it’s not really terribly novel.
Marc Rogers: The important thing to point out is this is all low-hanging fruit. This is easy stuff that can be gotten off of almost every type of cellphone with commonly available tools and without expending too much effort.

Ryan Lackey: Yeah, all of this stuff used to actually be hard. People haven’t taken into account that it has changed and it has become a lot easier to go after (see right-hand image). It used to be you had maybe one agency in the U.S. and one agency in the Soviet Union to worry about – now pretty much anybody with a little bit of RF equipment can be your threat, anybody with a network router in your path can be a threat, anybody running a service can be a threat, and anybody who gets access to your equipment. So it’s a much wider population of people attacking you. If you are not attractive to the government as a target, perhaps you are attractive to a different government or to an individual or to an organization. It’s really sort of a democratization of SIGINT and attacks.
Marc Rogers: One interesting thing from this slide is everyone is talking about the impact of Snowden and how that’s changing behavior, how everyone is moving towards more encrypted. It has had an effect on the traffic on the Internet. We’ve gone in U.S. from 2.29% of traffic that was deemed to be SSL traffic – today it’s 3.8%. That’s a really big increase, right?

Ryan Lackey: And a lot of the traffic that is unencrypted, of course, leaves all this data available (see right-hand image). Even if the data is encrypted you can get a lot of information just from pure traffic analysis. You can see source and destination of target; you can see the type of traffic in a flow. You can actually in a lot of cases get content information just by the sizes of packets and how they interact, because it’s not data-independent. And it’s pretty terrifying.
Marc Rogers: And what you have to realize is a lot of the time you don’t have control over this. Vast majority of this traffic is backend traffic. This is your application talking to application server; you don’t have a choice to say “I’ll only use encryption,” because that’s up to the dev who built your app.
Ryan Lackey: Yeah, it’s pretty bad when you pop up a commercial operating system on a new computer for the first time – it’s got all this other software that you are not really familiar with, and you don’t really know what’s phoning home and when.

Cellphones are even scarier (see right-hand image), because you actually do have pretty good information that they are phoning home all the time, they are always in contact with the tower, and they are relaying an awful lot of information that you don’t really ever see as a user but is there and is a threat. And the scary thing is, while you might trust your operator and you might trust your phone vendor, over the air a lot of this data can be gathered just from passive monitoring, and anybody else who is over the air can do a lot of this stuff.

Ryan Lackey: Then we’ve got examples of when you travel to places like China. China is a great place to visit, but they have a fairly restrictive international firewall, the “Great Firewall” (see right-hand image). It’s not really one firewall, it’s a different firewall in every province, and different operators have different policies. But in addition to being monitored, there is just a basic problem of stuff getting blocked. And it’s really annoying when you go and you want to connect to your services, you want to basically operate like you would at home. You’d think just a VPN would protect you and would allow you to bypass all this stuff, but in a lot of cases it’s a little of a “whack-a-mole” game they play, where they block different VPN technologies all the time. So it’s a pain to deal with.
Marc Rogers: One more thing on the Chinese Firewall is they are actually getting smart with how they are looking out for VPNs. Before, it was identification of VPN points – and they would get blocked. Now, as we have seen with Tor since about 2011, they are actively scanning suspected nodes and they are doing things like talking Tor to suspected nodes, and if they get a reply they flag it and they block it. But that makes it really difficult, because now you’ve got folks who are actively looking for your tools and blocking them. So, whatever you have to do has to be robust enough to protect it.

Ryan Lackey: There’s a bunch of tools that people use today that help users protect themselves and that are provided to users (see right-hand image). Some basic principles that make certain tools easier to use and more privacy-protecting than other tools: generally, I would say decentralized tools and tools that are used by smaller communities rather than a wider tool are going to be more likely to work in any given scenario, though there’s an engineering quality issue of a tool that’s not used by very many users isn’t going to generally be as high quality. Generally, I like things like real-time, things that are asynchronous, like email-based systems rather than connection-oriented systems. However, we’ve really moved to the worldwide web and everybody wants to use connection-based systems, and it’s sort of a pain. And then, encryption – even if it doesn’t provide you with full protection – it does provide you with a little bit of content protection in a lot of cases, even if it’s not implemented terribly thoroughly. So if you get the choice, always add encryption.
Also there are a lot of common tools that can be reconfigured. VPNs were never really intended as anonymity technology; they just happened to be useful in certain circumstances. They do provide some privacy and they provide some firewall busting just because people don’t want to block all VPNs because it will block a lot of business traffic. So it’s an interesting thing. And the really awesome thing is that cheap hardware has gotten so cheap that you can dedicate a given piece of hardware to a certain task. It’s really-really hard to build a secure multi-user, multi-application operating system; it’s really a much simpler challenge to build a single-purpose device and dedicate it to a certain thing.
Marc Rogers: Before we move off of VPNs, one amusing thing that came off in our discovery. As we were playing around with the Great Firewall, we discovered that you can actually weaponize it. The Great Firewall, really, detects a node doing something it doesn’t like, it floods it with reset packets, and it’s not really doing much to validate the source address. It’s also quite nice that it floods it with reset packets for sometimes up to 30 seconds, so it’s an amplifier. I was just playing around at another conference and I sent some packets spoofing a colleague, and the Great Firewall flooded him with reset packets for the next couple of hours, and he couldn’t do anything. Although I hardly advocate doing this, be careful.

Ryan Lackey: …Yeah, so tempted. Another thing that’s really scary is JavaScript. If you don’t have a great separation between your data and your code, bad things happen. And a lot of the problems with anonymity tools leaking information are either when addressing information is somehow conflated with the messages, so the OSI stack isn’t really kept as separated as it should be; or where code is mixed with data. These things lead to very bad stuff.

As we were saying, cheap hardware is great, it prevents a lot of user errors. The problem with a lot of these secure systems is users use them incorrectly (see left-hand image), and if you give somebody a single device and say that’s for talking to one other person, that’s a much easier user model than you need to enter this code every time you use it, you need to authenticate then and do all sorts of stuff.
Marc Rogers: I had a great real-life example of this, literally yesterday. As part of my goon job I had to provide protection for John McAfee. And we’re walking around with John, who is a colorful character, with his security detail who are even more colorful (especially the one who remembers faces). And he was talking about security with phones, he’s like: “I always use burner phones and I’m very careful. Once I’ve used a phone for a certain amount of time I attach it to a lorry, and it goes off around the country, and they can follow that. But they always track me down within a couple of days and find me again.” And I said: “By the way, do you regularly call the same kinds of numbers?” He said: “Yes.” I’m like: “That’ll be why.” It doesn’t matter if you are changing your phone if you keep calling your mom.

Ryan Lackey: One of the issues is, again, if you go by this hardware and you order hardware from the Internet, your odds are going to be pretty high (The Grugq knows that pretty well) that that hardware is not going to come to you exactly as the hardware vendor intended it (see right-hand image). And you probably want to start buying stuff off the shelf that’s pretty configured, it’s sort of commodity thing. It’s unlikely that they are going to backdoor every single piece of hardware that’s a retail thing out there, but the one piece of hardware that The Grugq orders is very likely to be backdoored.

And cash is great. And Bitcoin is not so anonymous. The same things sort of apply to accounts (see left-hand image).

VPNs are sort of nearer to my heart; I ran a VPN provider for about a year and then we shut it down when the Lavabit thing happened. They are definitely useful tools (see right-hand image). There are some concerns: they are not end-to-end; they are not really designed for anonymity, so they don’t give you anonymity. You have to use them correctly and all sorts of stuff like that. And then there’s of course the problem of your trusting the operator of some service to 1) operate in a certain way, keep logs and things; and 2) it’s really-really a bad idea to ever expect the third party to break the law on your behalf for, like, $3 a month – it’s not going to happen. So you’re going to have data turned over. The third-party doctrine in the U.S. means that a server provider, really, has very little ability to protect their customer data.

There’s some cool stuff that sort of counters this. There’s Tor (see left-hand image). Tor is a great tool, it can keep you anonymous. I believe Snowden has endorsed it, lots of other people have endorsed it. But it’s got some disadvantages. It has a very recognizable signature. It’s a high-profile, lots of people are looking for it. And it’s pretty complicated and not really so simple for users to understand. You have to build additional systems on top of it to make it usable. Tor Browser Bundle and other similar things are great, but you need that level of additional tool to make it a really useful end user tool.

However, it’s got some enemies (see right-hand image). If you are trying to use it in a place like China, they are getting better and better at blocking it if it’s the default Tor protocol. Deep packet inspection can block it, and then of course if you have exfiltrated data from some secure network that logs everything, there might be a human analyst looking at it after the fact, and the Tor traffic will be pretty obvious. So whoever sent the Tor traffic is bound for a visit. So people realize this is a problem and they came up with transforms.

Marc Rogers: There are Tor pluggable transports (see right-hand image), which is a great tool. There are seven of them that are live right now, I think this is still accurate. And there’re a couple that are much more popular than the others. The benefit of the Tor pluggable transports is they have recognized that there is no one tool that will solve the problem. There’s no silver bullet. And whatever solution you use needs to be variable, because if you keep doing the same thing, eventually someone is going to catch on to it. Plus, if you make as many people develop as many different things as possible, you are going to get some real genius. And, honestly, some of these pluggable transports are phenomenal. The general concept of this is to take Tor traffic and to transform it so that it doesn’t look like Tor traffic. And the next level up from that is to take this transformed traffic and make it look plausibly like some other form of traffic.

This (see left-hand image) is probably one of the best ones. A lot of the censorship tools out there are quite crude. What they do is they use regular expressions to look at the protocol and make a judgment as to what they think it is. If you use those same types of regular expressions yourself you can play to them and make your traffic look like whatever you want. The screen here is transformed Tor traffic that has been put through a transform that makes it look like SSH. While it won’t stand up to immediate scrutiny – any of you who are familiar with SSH look to that – you’ll say it’s clearly not SSH. The point is, with this vast volume of traffic going through, the only people who are going to get that special extra scrutiny are people who have popped up a red flag. This is about not popping up that red flag. As long as your traffic hides amongst the general Tor traffic, there’s going to be no reason for them to dive deep enough to say this is suspicious.
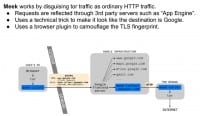
Ryan Lackey: And then there’s an additional tool (see right-hand image), where if you have a cooperating end point on the other end, such as Google App Engine, you can encode your traffic as normal HTTP traffic and then also put it inside HTTPS; you can make it look like it’s going to a regular website. You can do a lot of cool stuff there. And I guess the ultimate thing would be to make it look like natural language.

Bananaphone does this. It obviously won’t stand up to a human analyst looking at this after the fact if you aren’t routinely sending literature back and forth with someone, but you can imagine a scenario where this evades an automated detection system or even where you build a system on top of that (see left-hand image).

Then there’re of course the classic network tunneling tools (see right-hand image) that are primarily used for getting around, like, captive portal authentication systems with dnstunnel and things like httptunnel. These are pretty cool.
Marc Rogers: The point of going through all of these is these are the tools that we looked at for building the travel router. The travel router itself, really, isn’t that much to it, but what we did was we looked at all the best tools out there and we built them into this as a library so that you have an OS build that is going to sit on device that you can carry anywhere, it’s tiny, and all of these things will be available to you to choose. And we are hoping to build some intelligence onto it as well so that it will make some of those choices for you to say: “Are you sure you wanted to select that? That might not be the best thing.”

Ryan Lackey: There’s no silver bullet, so it’s a bunch of separate tools that are combined (see left-hand image). As we were thinking about this we had the practical concern – we travel a lot, we go to places, we’re not really the most interesting targets, but we get some level of target, and I know a lot of people that are much greater targets. And it’s really difficult. I can build something that I can use myself, mostly out of existing software. But building something I can have somebody else use that’s easy for them to use, simple, that I don’t have to then go with them all the time – is a much harder problem.
We looked at a lot of the VM systems. VMs are great but the problem is, if something gets subverted in the top level operating system, fingerprinting stays the same and there’s really no way to know that the system is intact. I’ve worked on a lot of stuff with the TPM tamper-resistant computing stuff, and it still is not quite there. And the other problem is this stuff is expensive. If you were to build it out of pure software on dedicated high-end laptops with virtualization, like 16GB RAM MacBook Pro’s, you can’t really afford it. Most of the people that really need this stuff are also people that are not rich. They are also not willing to throw away a 3000-dollar laptop every time it might be compromised. So it wasn’t really the most ideal target. So we looked at something that would be providing much of the same protection but be a lot cheaper, a lot easier to use and a lot easier to support, and ideally something that people already have to use. And we came up with secure travel routers being the sweet spot.

They are pretty awesome (see right-hand image) because they are $20-100 each, they are made by a bunch of vendors – TP-Link, Linksys, D-Link – all the standard low-end network companies make this stuff. They are available everywhere. A lot of people use them when they go to hotel and they have to pay per WiFi device or per MAC address. This lets you share a wired connection in a hotel room with a lot of connections. There’s a lot of cool stuff you can do, but they really weren’t explored as a security tool very much.
Marc Rogers: One of the challenges we have there is that hardware is incredibly variable across the whole range. Some of them have a fair amount of flash memory; some of them have almost no flash memory. So the next version of the device is going to have a kind of a “kitchen tool”. What you’ll do is you’ll put in the version of the travel router that you’re working with – you’ll look it up in the library and know how much resources it has – and it will then tell you which modules you can select. So you can have Tor plus these transforms, or if you want to have secure voice you can have this SIP phone plus these other things added in – just enough to squeeze it in without filling it up.
Ryan Lackey: We’ve used a lot of OpenWRT built on that, there’s a lot of open-source firmware for these routers, for home routers. I think maybe the Linksys WRT54G was the grandaddy of this stuff, where it came with pretty crappy firmware. You added awesome firmware to it that was free – and you’d have a great device. Unfortunately, wireless hardware has moved on, so you need to use newer stuff, but that whole wireless router hacking community has been going on for a while, it just hasn’t been focused on the travel router market or the “building security tools into it” market. The EFF is sort of working on a project to make secure routers for home use, primarily focused on protecting them from outside threats as opposed to using them for security tools themselves. And that’s a huge improvement over the status quo even a year ago. The problem with these things is they are embedded; there’re, like, a billion different ones of them. The toolchain process takes about two weeks to self-host, so it’s a pain. It’s not a huge pain; it’s not as much of a pain as dealing with very minimal-resource embedded stuff, but it’s still not the easiest thing to do.

Other people have worked on this stuff before (see right-hand image). The Pogoplug guys have the Safeplug, which is pretty cool, but they don’t do pluggable transports. The have Tor, they don’t do pluggable transports. It’s not really a portable device; it’s more for home use. Onion Pi, which Adafruit – the awesome company – has, is sort of like a “learn how to do something” project. It uses a device, Raspberry Pi, and has some external WiFi hardware and stuff. And there’s Portal, which I found out about when I started talking to Grugq. I’ve been looking at this stuff individually and then I talked to Grugq, and then I realized that the guy who was working on Portal was actually the same Grugq that I’d been talking to on other stuff. So it was kind of an obvious thing to do; Marc and Grugq have known each other for forever.
Marc Rogers: There is only one Grugq.
Ryan Lackey: Yeah, it’s not that rare a name, so… The original Portal from a couple of years ago had Tor pluggable transports and voice, but it was a huge pain to install – there’s, like, a GitHub page for it. It did a lot of the stuff but it wasn’t an all-in-one thing.

Ryan Lackey: So, out of this full range of hardware we needed to come up with initial piece of hardware that we wanted to support as a development environment (see right-hand image). The Qualcomm Atheros AR9331, which is used in the Hak5 Pineapple, used in a bunch of travel routers, super cheap in quantity – is awesome. We wanted to have a pre-built image for it and multiple ports. The other thing is we really want to be able to power it off of USB, because then you can use USB batteries, you can power it off your laptop. And one use case for this is you use something like a Nexus 7 or a cell phone with the baseband turned off, and you want your mobile phone to be able to talk to this device, which then have a WiFi connection or a 3G connection plugged into it. So having something that could be battery-powered is great, but putting a battery into a small cheap device is more of a consumer engineering challenge for us. We are not really all hardware guys, so trying to make things as simple as possible made sense. And, obviously, it needs to be easy to use, with a GUI for configuration.

But there are some problems (see left-hand image). A lot of this hardware is designed to be as cheap as possible when you make it in, like, million-unit quantities. The price difference between a 64 MB RAM chip and an 8 MB RAM chip is substantial in those quantities. So they put the absolute minimum amount of RAM, absolute tiniest flash they can possibly do in these devices. And we wanted to have multiple radios and multiple ethernets in a small device, which wasn’t really a common use case. The other problem is we’re sort of in the middle of 802.11n and 802.11ac. USB 2.0 is still the most widespread power protocol we could use, so we’re limited to 500mA. Radio quality on a lot of this stuff is actually really-really bad: they’re using questionable antennas and their whole RF chain is pretty questionable.
Also, making quantity under 10 of something is really easy because you can make it yourself. Making quantity, like, 100,000 or a million of something is also fairly easy because you can justify amortizing your dev costs over a large number of things. But making, like, 1000 of them or 5000 of them is still a pain point. We looked at the cost of making them; you can buy these travel routers for about $100, $20, whatever. For us to make a small quantity of them is going to be really expensive. And there’s a problem of, if we make the special secret spy router that everyone can use – 1) we have to distribute it to all the people that want it, and 2) it’s itself very suspicious, so the guy carrying around the super-secret spy device is going to get special attention, and special attention is the absolute last thing you want.
Marc Rogers: Speaking to someone who gets special attention every time he goes to the airport, I can tell you it’s a real drag.

Ryan Lackey: I had been working on this as a hardware thing and ended up selling my company instead and doing some other stuff at CloudFlare. So it was sort of like a back burner thing, and then I was like: “Oh, what are we gonna do?” And then – we’re saved by China (see right-hand image). There’s apparently a company in China that makes the perfect device. It appears to be a clone of a much more popular device, but it happens to have a huge amount of RAM and a huge amount of ROM. And they are really cheap. It’s the “Goodlife” GL-iNet box. You can buy them for $215 for 10 of them and you get them in three days. They’re awesome. It’s pretty much the perfect hacking platform for this kind of hardware. It’s got two ethernet ports on it, USB and the micro USB for power. It’s pretty ideal.
So we’ve got portalmasq.com, we’ve got tools that are loading up there that will let you effectively use the old Portal toolchain and then additional pluggable transports on it. Building the server side of it is maybe a little bit ambitious at this point, but definitely the client-side hardware will work with the existing services.

Marc Rogers: We would welcome a ton of feedback because we want to shake this into a tool that’s generally usable. This is no good if it’s hard to work with. It needs to be the kind of thing that you pop in your pocket, that a journalist can take, go to a foreign country and use it for secure communications without even thinking about it.
Ryan Lackey: … And open-source, obviously, non-commercial.
Marc Rogers: Thank you! Any questions?
Question: Could you provide some additional details about the device?
Ryan Lackey: This is a clone of TP-Link 703N.
Question follow-up: Why didn’t you use other devices to build the travel router?
Marc Rogers: They are great; the problem is – less RAM means less stuff. And what I ultimately want to put on this is I want there to be a SIP phone, I want there to be Tor with pluggable transports, and I want to put on some tools so that they can actively probe the networks they are connected to and make some judgments about the kind of networks. It needs to give some guidance and give a little bit of advice in terms of the level of security that the user is experiencing at that point.
After we gave a similar talk for H.O.P.E. and after the feedback we got from that, we’ve started putting together this kitchen tool so that you guys can use anything you want. There just may be some tradeoffs. If you put some of the tools onto a USB device, perhaps it’s not going to be quite as fast and there may be some UI issues. Likewise, maybe you don’t care about the SIP phone and you just want something that has Tor stuff on it. This will allow you to just point and click, choose what you want, build the image, flash it to your device – and off you go. And the big benefit of that is, if we can have a ton of people with a ton of different devices doing it – it makes it much harder for anyone to say: “This is the bad thing.”
Question: The people here are hackers and they can get one of these things and use it. Is your device going to be available enough for, like, my mom to use it?
Marc Rogers: That is a great question. We’re contemplating, maybe we should do a Kickstarter, maybe we should donate a bunch to the EFF and have them give out. I’m kind of hoping that, as people start to use it, more people will hear about it and want to use it. I’ve been talking to a global telco provider, they’re potentially going to give us a global SIM that we can put in this and bundle a chunk of free data. So, at that point you’ll have a pocket travel router that has a 3G bearer no matter where you are. This thing will get you going before you’ve even checked in to a hotel. At that point, this could be useful enough that people will start using it, and then the security features will kind of come as a benefit.
The code is already up, the basic stuff. It’s a living project. I would be really happy to have the kitchen and most of the UI done by the end of this year.






























